VENDOR NEUTRAL VULNERABILITY MANAGEMENT
Welcome to the Future of Vulnerability Management
Are you tired of the headache-inducing spreadsheets that come with managing penetration test results? Say goodbye to the days of manual data entry and tracking vulnerabilities on multiple Excel sheets. Welcome to the future of cybersecurity management with our cutting-edge, vendor neutral Security Platform.

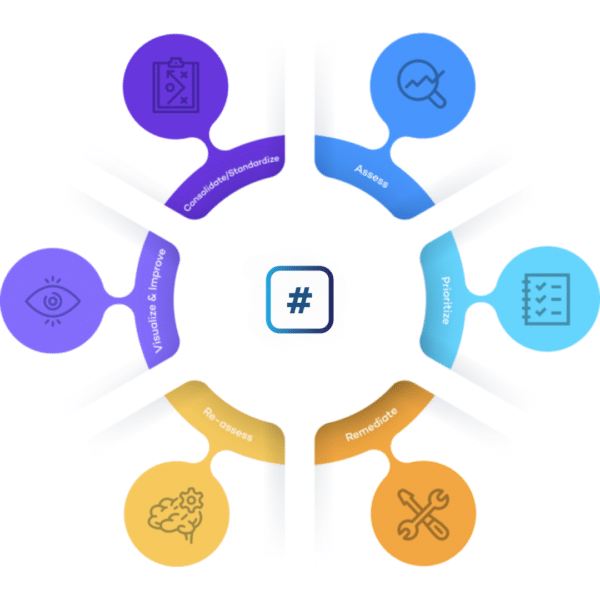
INTEGRATE, CONSOLIDATE, REMEDIATE
Unify Your Vulnerability Data, Automate Your Remediation Workflows
Consolidate all data from penetration test reports and leading assessment tools, accelerate remediation from start to finish, and gain real-time insight into your threat landscape.
Platform Users Experience a Massive Decrease in Mean-Time-to-Remediate

![]() Active Exploit Detection
Active Exploit Detection
Overhaul point-in-time reporting and provides teams with powerful, continuous surveillance.
The Rootshell Platform provides the context needed to cut through the noise of vulnerability data, pinpointing which issues are truly most vulnerable to you and empowering teams to implement the most effective prioritization possible.
![]() Remediation and Collaboration
Remediation and Collaboration
Dynamic remediation saves significant admin time, remediator dashboard transforms remediation tracking. You can even set and track Remediation SLAs.
Streamline project management, by integrating with popular ticketing systems, enhance collaboration between colleagues, testers, and third-parties, and get live updates from tests. including a calendar view and reminders for your tests
Our Platform Integrates With Leading Tools, Ticketing Systems, and Exploit Intelligence Feeds
Consolidate Your Suppliers’ Assessment Data
Rootshell’s Platform enables you to consolidate results from any scanner or penetration testing vendor. This makes it easy to analyse different assessment results alongside each other, helping you make the best decisions for your organization.
- Import results from any security assessment provider in a few clicks
- Support for major third-party scanners, including Nessus, Qualys, Tenable, and more
- Require your security assessment providers to input your results into the platform
Integrate and Standardize Your Assessment Data
Our platform generates a database of your results in a standardized format, making it easy to manage all your vulnerabilities in one place and saving your team the time spent on manual data admin.
- Manage all your vulnerabilities from one database
- Automatically standardize the format of your assessment data
- Search, filter, and tag results
Contextualize and Prioritize Your Assessment Data
Our platform uses industry-leading Daily Exploit Detection that helps you gain context of your issues in real-time, helping you prioritize most effectively.
- The platform integrates with exploit resources to add context to your issues
- Be alerted as soon as an exploit becomes available for your issue
- Assign priority ratings to your assets to easily track your most important ones
Streamline Your Remediation Workflow
By eliminating the need for spreadsheets, PDFs, and manual processes, Rootshell’s Platform modernizes vulnerability management programmes and makes every aspect of your remediation workflow faster and more efficient.
-
Integrate with ticketing systems (JIRA and ServiceNow)
- Enhance collaboration between colleagues, testers, and third-parties
- Receive live updates from tests
- Streamline project management, including a calendar view for your tests
Track and Validate Your Remediation Results
With Rootshell’s Platform, you can measure your remediation efforts against your service level agreements (SLAs) and track key compliance metrics, such as your monthly remediation rate.
-
Set and measure SLAs
- Monitor compliance using the Compliance Dashboard
- See your best performing system owners ranked on the Compliance Leader Board
- Allow the platform to mark issues as remediated on your behalf with Dynamic Remediation
Visualize and Analyse Technical Risk Across the Whole Organization
Rootshell’s platform helps you gain a clear understanding of your global threat landscape and makes it effortless to continuously analyse your technical risk, with insightful dashboards and automated reporting.
-
The Dashboard puts key insights front-and-centre, including the number of exploitable issues
- See trending data across your digital estate
- Our platform takes the legwork out of reporting, providing you with useful charts and graphs
CASE STUDIES
What Our Customers Think . . .

Streamlining the Management of Multiple Security Assessments and Accelerating Remediation for Zinc
“The Rootshell Platform gives me the visibility to easily understand issues, approve projects, and collaborate with colleagues so that our remediation process is as streamlined as possible. The platform is incredibly intuitive for non-technical leaders like me. The tooltips and training make it really easy to get the most out of the platform from the get-go. ”
– Stephen Shackell, Director of Intelligence and Risk

Improving Vulnerability Management for Sphere’s Remote Global Team
“Rootshell’s Platform is very useful for coordinating a global, remote team, and invaluable at helping us stay on top of our critical issues and delegating them accordingly. The platform’s dashboards are vital for us to manage our weaknesses, and I love the user interface – it looks slick and professional for our clients.”
– Richard Sacré, IT and Operations Director






















