Our latest update enhances the asset permission capabilities within the platform, introducing Asset Level Permissions and Asset Group Permissions. These new additions provide unprecedented granularity in access control, tailored to meet the sophisticated security and management needs of modern digital environments.
Key Features
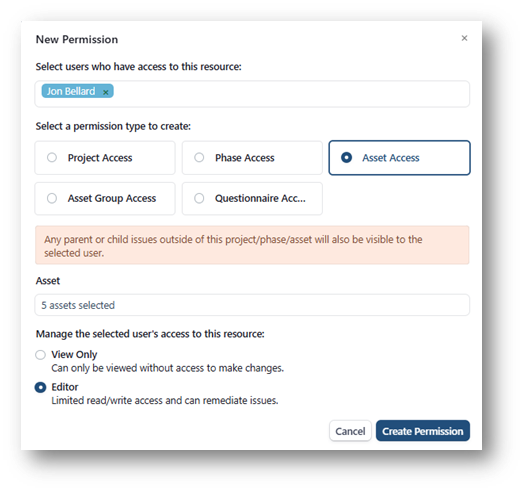
Asset Level Permissions
- Granular Access Control: Users can now assign permissions for individual assets, accessible through the Permissions sidebar menu under the Access Control submenu. This feature is crucial for delegating precise access to asset owners and specific stakeholders.
- Flexible Selection Options: Within the new permission modal, users have the flexibility to select one or more assets to assign to a user or a group, enhancing the adaptability and precision of asset management.
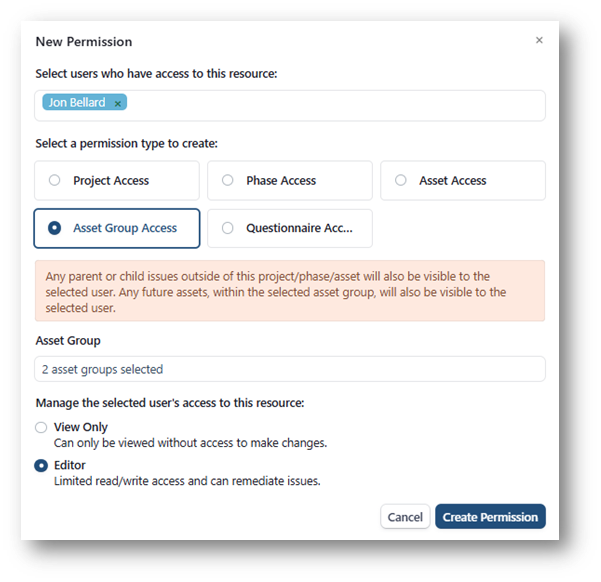
Asset Group Permissions
- Logical Grouping for Enhanced Management: The ability to select asset groups as a permission type allows for logical division of a client’s estate, facilitating targeted management and reporting.
- Focused Access for Remediation: Providing access to designated asset groups rather than the entire tenant ensures that users are focused on relevant assets, improving efficiency and effectiveness in remediation efforts.
User Impact:
The introduction of Asset Level and Asset Group Permissions significantly enhances how security administrators can manage and delegate access within the platform. By enabling more detailed access configurations, organizations can ensure that the right individuals have the right level of access, aligning with security best practices and operational requirements.
Conclusion
These enhancements to the Permissions module underscore our commitment to providing robust, flexible, and secure management tools. With these new capabilities, users can expect a more controlled and streamlined approach to asset access, driving better security posture and compliance across their digital environments.



