Managed vulnerability scanning (MVS)
Continuously monitor and maintain your security posture with Rootshell’s managed vulnerability scanning services. This human-led, fully managed service provides year-round visibility of your organization’s vulnerabilities, backed by remediation guidance from our expert team.
Trusted by companies of all shapes and sizes
Understand your assets, risks and threats with managed vulnerability scanning
With MVS, Rootshell Security’s scanning agents regularly scour your technology estate, supporting you to remediate vulnerabilities before they’re exploited using industry-leading technology. Enhanced reporting provides you with the data you need to ensure compliance with key standards such as ISO 27001 and Cyber Essentials Plus.
What is managed vulnerability scanning?
Managed vulnerability scanning involves regularly monitoring and scanning your organization’s IT infrastructure to identify security weaknesses. These scans cover networks, servers, applications, and other digital assets, ensuring continuous detection of vulnerabilities such as outdated software, misconfigurations, and potential entry points for cyberattacks. MVS not only improves your overall security posture, but also gives back time to internal teams to focus on business critical activities.


Full coverage, year-round defense
By leveraging intelligence-driven insights, we can detect if your organization’s infrastructure is listed on bad-reputation or “deny-lists” associated with malicious activity. Our managed vulnerability services are also flexible, evolving alongside your organization’s changing needs. As your objectives shift, our service adapts, ensuring your network is responsive to new challenges. Plus, our MVS can work hand-in-hand with your annual penetration testing for even better protection.
End-to-end expert support
Our experienced security consultants handle every aspect of the process, from initial configuration to detailed reporting. They are always available to provide remediation advice, guiding you on the best steps to maintain a secure environment. Meanwhile, our Security Operation Centre (SOC) analysts meticulously review your vulnerability scan results,, minimizing false positives, and assigning appropriate risk ratings.
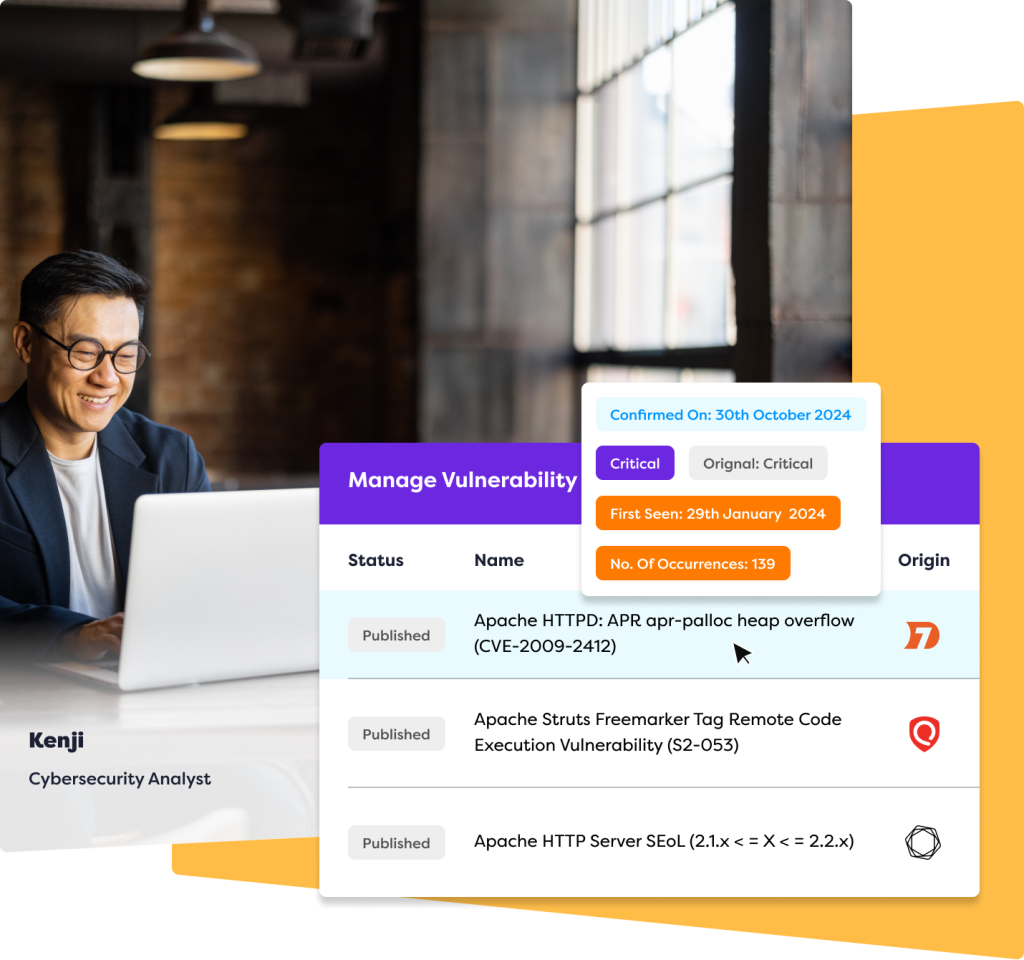
Real-time reporting through The Rootshell Platform
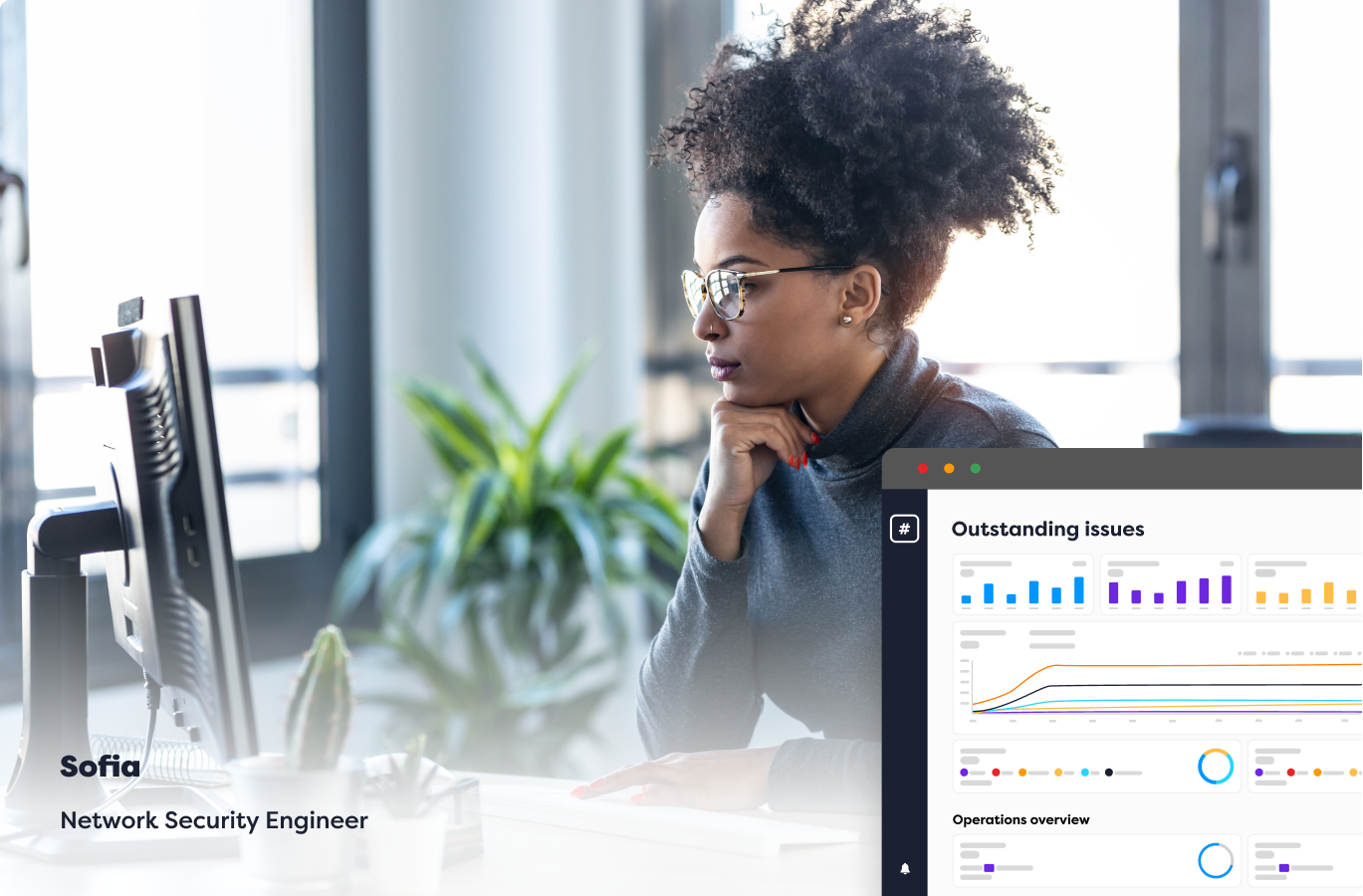
Say goodbye to static spreadsheets! Unlike most cybersecurity providers, we provide dynamic reporting through a centralized dashboard, collating and prioritizing all of your penetration testing and attack surface management reports in one place – even if you use other vendors. This means you can see which vulnerabilities need your attention in real-time, vastly accelerating the remediation process.
Hear why the world’s top companies place their trust in us
Managed vulnerability scanning benefits
Managed vulnerability scanning offers significant benefits by providing continuous, expert-driven monitoring of your IT infrastructure. With automated scans and detailed analysis, this service enhances your organization’s security posture, minimizes false positives, and ensures that vulnerabilities are prioritized and remediated effectively.
Regular surveillance
Continuous vulnerability management helps to identify and eliminate security weaknesses. Our managed vulnerability scanning alerts you to issues as soon as they are discovered, providing your organization with round-the-clock protection.
Manual reviews
Our security consultants manually review your vulnerability scans to dismiss errors, false positives, and non-issues, so you only spend time focussing on what’s most important.
Better use of resources
With access to our automation center, our managed vulnerability scanning service frees up your internal team, allowing them to focus on other critical tasks while relying on specialized expertise to keep your defenses strong and up-to-date year-round.
Why choose Rootshell’s managed vulnerability scanning services?
Our highly experienced and dedicated analysts provide the expertise, insight, and advice needed get the most out of your managed vulnerability scanning.
Expertly managed vulnerability scanning
We have the relevant experts on-hand to provide the insight needed to remediate effectively. You will have a dedicated Rootshell Consultant, who holds accreditation by recognized bodies.
Best-in-class tools
When we believe a new or existing product becomes a challenger or market leader, we will deploy it for the benefit of our clients – all at no additional licence cost!
Tailored recommendations
Your organization probably has a vast number of assets, some more important than others. Our security consultants take the time to help you prioritise, ensuring you make the best use of your budget.
Recognized industry leader in penetration testing as a service (PTaaS)
What’s included in Rootshell’s managed vulnerability scanning services?
Your tailored managed vulnerability scanning package will include regular, automated scans of your IT infrastructure ensuring that your defenses remain robust and responsive to new threats throughout the year. As well as advanced, real-time reporting, you’ll also have access to our team of cybersecurity specialists who provide ongoing support and advice.
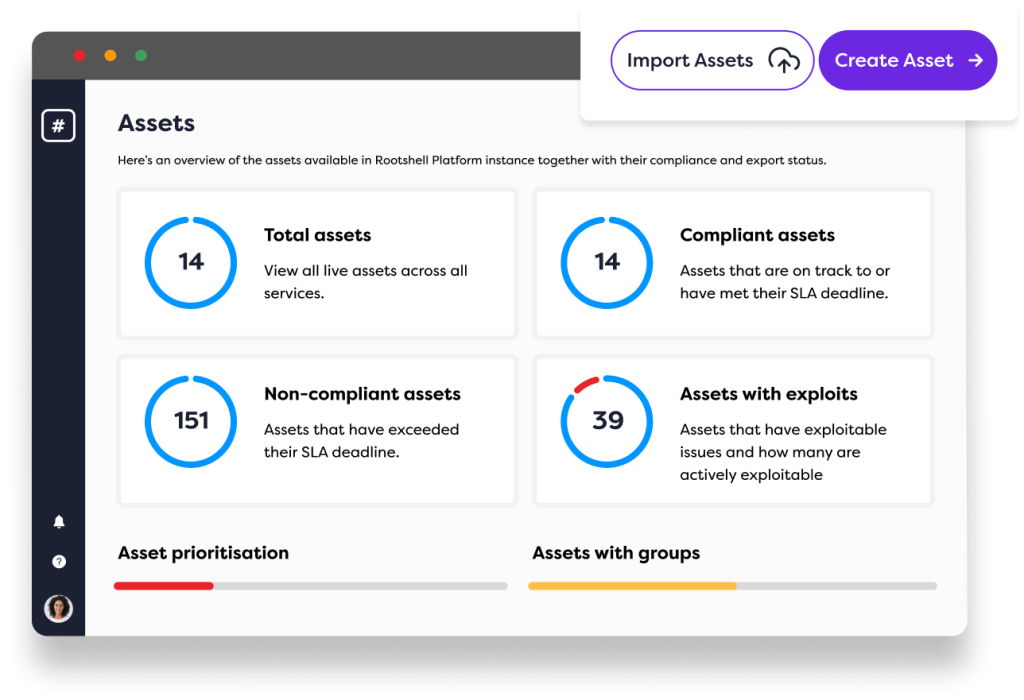
Build your package:
- System misconfiguration
- Unpatched software
- Encryption issues
- Weak credentials
- Injection flaws
- Broken access control
- Broken authentication
- Security misconfiguration
Plus receive your results an data through The Rootshell Platform
Ready to get started?
Discover your needs
Dive into a personalized demo
Seamless onboarding
Frequently asked questions & answers
Can’t find the answer to your question?
You can always Contact Our Team of experts for a chat!
What is the purpose of managed vulnerability scanning?
Managed vulnerability scanning continuously monitors and assesses an organization's IT infrastructure for security weaknesses. By identifying vulnerabilities such as outdated software, misconfigurations, or potential entry points for cyberattacks, it enables proactive remediation before these issues can be exploited. This service helps maintain a strong security posture by providing ongoing protection and reducing the risk of breaches.
Vulnerability scanning vs penetration testing - what’s the difference?
Vulnerability scanning and penetration testing are both essential security practices, but they serve different purposes. Vulnerability scanning is an automated process that identifies potential security weaknesses in your systems by scanning networks, applications, and other digital assets.
Penetration testing is where security professionals simulate real-world attacks to exploit identified vulnerabilities. Penetration testing not only identifies vulnerabilities but also tests the effectiveness of existing defenses.
How do you ensure my vulnerability management is compliant?
To ensure your vulnerability management is compliant, our managed vulnerability scanning service follows industry standards and regulatory requirements relevant to your organization, such as the Payment Card Industry Data Security Standard (PCI DSS), GDPR, HIPAA, and others. Additionally, our service adapts to changes in compliance requirements, ensuring that your vulnerability management remains up-to-date and aligned with legal and industry obligations.
What are the most common ways to manage vulnerabilities?
The most common ways to manage vulnerabilities include regular vulnerability scanning to identify potential issues, patch management to update and fix software vulnerabilities, configuration management to ensure systems are securely configured, and implementing access controls to limit exposure. Additionally, penetration testing helps validate the effectiveness of your security measures, while ongoing monitoring and expert remediation support ensure that vulnerabilities are promptly addressed as they arise.