Vulnerability management for manufacturing & construction
Keep operations up and running with penetration testing for the construction & manufacturing industry
Safeguard operations from increasingly sophisticated cyber attacks with manufacturing penetration testing from Rootshell. From securing complex supply chains and maintaining uninterrupted production to protecting intellectual property, discover our penetration testing service tailored specifically to fortify systems against cyber threats in the manufacturing industry.
Join 1,000+ leading companies who trust Rootshell Security
Maintain operational continuity
Manufacturing processes rely on smooth, uninterrupted operations. A single cyber attack can lead to costly production halts and delayed orders. Our construction and manufacturing penetration testing ensures that potential vulnerabilities are identified and mitigated before they can cause disruptions.
Secure interconnected systems
Manufacturing environments are complex, often consisting of multiple facilities, interconnected systems, and numerous third-party vendors. Our service focuses on securing both internal networks, such as operational technology (OT) systems, and external infrastructures that connect to suppliers, customers, and partners.
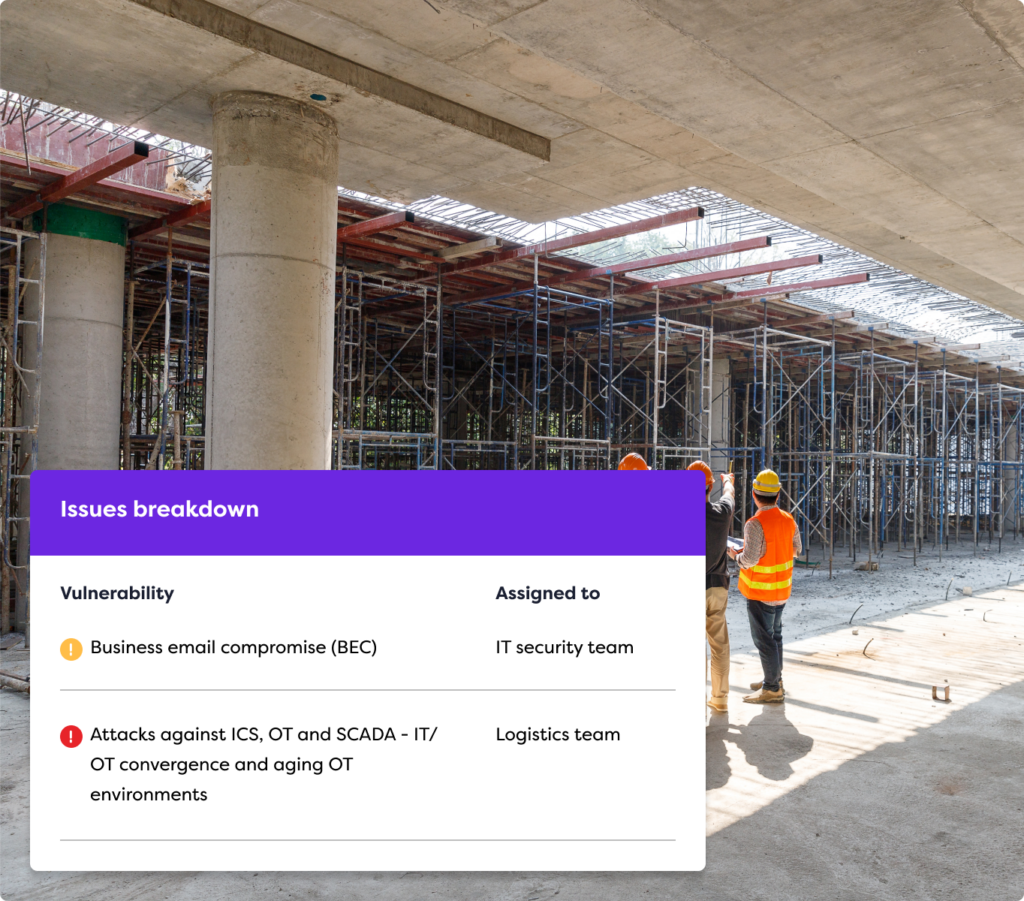
Strengthen supply chain resilience
Vulnerabilities in your supply chain can expose your business to threats such as malware, ransomware, and phishing attacks. If a breach brings your production to a halt, this can also impact partners in your supply chain. Our cyber security assessments ensure you’re protected beyond your four walls.
Why construction & manufacturing businesses choose Rootshell
With Rootshell
- Reduced risk of disruption and costly downtime
- Stronger vendor partnerships
- Data-driven remediation decisions
- Meet industry-specific compliance
- Real-time insights into your security posture
Without Rootshell
- Vulnerable to breaches
- Exposed infrastructure networks
- You may be the weakest link in your supply chain
- Unaware of potential vulnerabilities
- Time-consuming cyber security workflows
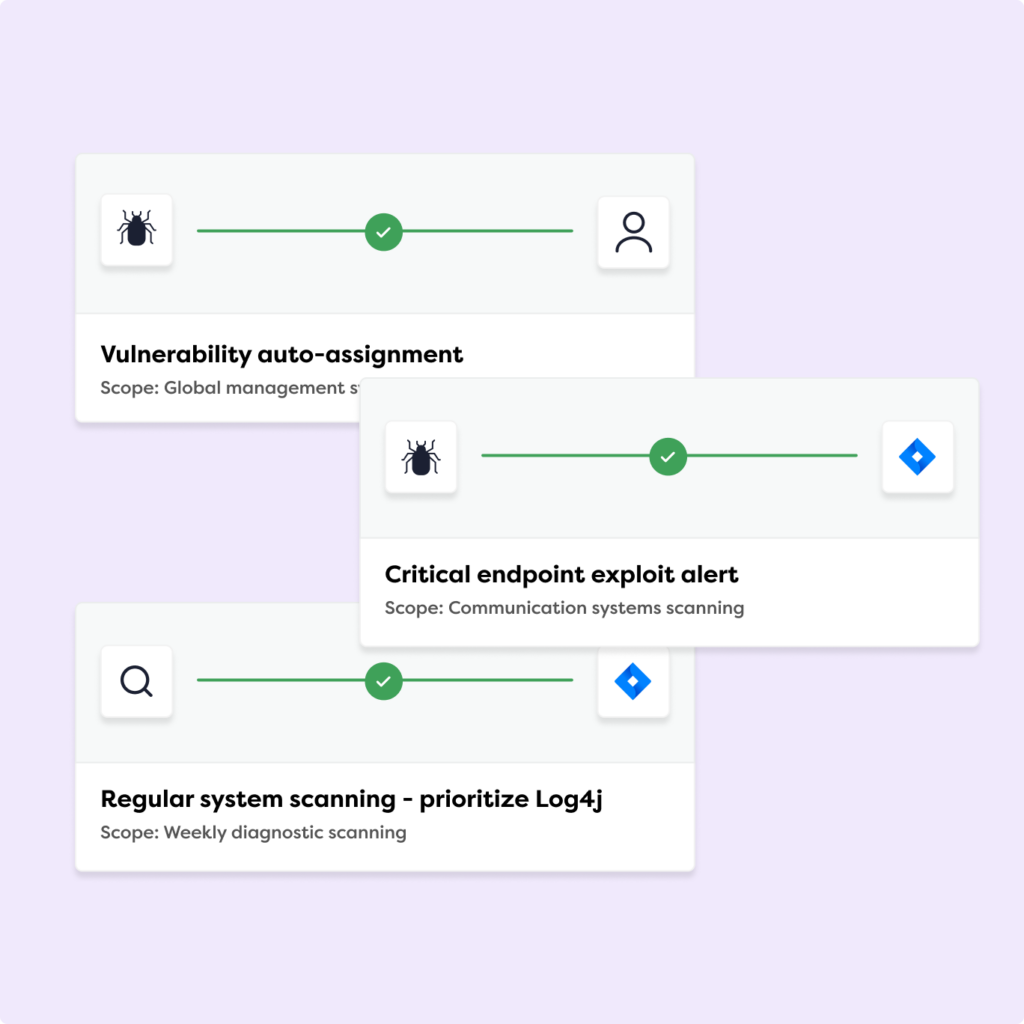
Manage all your vulnerabilities in one platform
Manage all your vulnerabilities in one platform
Our Penetration Testing as a Service (PTaaS) and vulnerability management tool, the Rootshell Platform, consolidates your test result data to accelerate remediation from start to finish, providing real-time insights into your threat landscape.
Uncover emerging threats
Continuous visibility through our active exploit detection helps you stay one step ahead of potential attackers with real-time alerts.
Track cyber security SLAs
Easily set up automated triggers to triage vulnerabilities and speed up the remediation process, deploying solutions the moment a threat is detected.
Project collaboration
Facilitate smooth collaboration between internal teams, external testers, and third parties, with live updates, a calendar view, and automated reminders to keep your projects on track.
Don’t just take our word for it, hear from our
clients...

Ready to get started?

1
Discover your needs

2
Dive into a personalized demo

3
Seamless onboarding
Discover your needs
Dive into a personalized demo
Seamless onboarding
Stories of success from other companies
Eliminating Risk Gaps with Continuous Penetration Testing for Leading Insurance Provider
Overcoming Cybersecurity Challenges with a Managed Service Provider (MSP)
Frequently asked questions & answers
Can’t find the answer to your question?
You can always Contact Our Team of experts for a chat!
Why is penetration testing important for manufacturing and construction businesses?
Penetration testing is essential for manufacturing and construction because it helps identify vulnerabilities in both operational and IT systems that could disrupt production, compromise intellectual property, or lead to a data breach.
How does the Rootshell Platform work to secure manufacturing environments?
The Rootshell Platform continuously monitors your digital estate, assesses vulnerabilities, and consolidates results from multiple security tools into one dashboard. It also uses automated triggers to quickly remediate vulnerabilities. This allows manufacturing and construction businesses to have an always-on, real-time view of their cybersecurity status.
What cyber security risks are unique to the construction and manufacturing sector?
The manufacturing and construction sector faces unique risks due to its reliance on interconnected operational technology (OT) systems and complex supply chains. Threats such as ransomware attacks, phishing, malware, and vulnerabilities in industrial control systems (ICS) can halt production and damage sensitive equipment.
How does penetration testing strengthen my supply chain security?
We evaluate third-party connections and processes to ensure that potential vulnerabilities in your supply chain are detected and mitigated. This not only secures your operations but also protects your partners from cascading attacks.
What types of cyber security testing are best for manufacturing companies?
For a robust approach to identifying and managing vulnerabilities, our team will work with you to create a bespoke 12-month package, which can also include attack surface management support. Depending on how your business operates, this might include managed vulnerability scanning, web application penetration testing and phishing testing to assess employee readiness.


