Continuous Threat Exposure Management (CTEM)
Today’s cybersecurity landscape is changing rapidly. CTEM helps organizations take a proactive approach to managing vulnerabilities and staying ahead of emerging threats.
The Rootshell Platform offers two flexible pricing models: a free trial license with limited access for evaluation and an Enterprise License with full platform functionality for comprehensive threat exposure management.

Join 1,000+ leading companies who trust Rootshell Security
What is Continuous Threat Exposure Management (CTEM)?
Continuous threat exposure management (CTEM) uses advanced analytics and machine learning to monitor, manage, and reduce your vulnerability to cyber threats. It integrates attack surface management, vulnerability scanning, threat intelligence and risk-based remediation to provide a comprehensive cybersecurity framework.
The term CTEM was coined by Gartner in 2022 to define a new model of cybersecurity that no longer relies on one-and-done security assessments or reactive responses to new threats. Instead, it offers a continuous program for identifying vulnerabilities, verifying them against real-world scenarios, and implementing remediations.
According to Gartner, organizations that employ CTEM will be three times less likely to suffer a breach by 2026. With the range of critical cyber threats continuing to expand, CTEM is now an essential component of any cybersecurity strategy.
Why CTEM Matters
For most businesses, the cyber threat surface is expanding rapidly. From large-scale cloud deployments to remote working and an expanding tech stack, the growing range of potential vulnerabilities poses serious risks. Your organization can face everything from regulatory and legal issues to long-term reputational damage.
In this environment, traditional security approaches, built around periodic scans and compliance checklists, are no longer enough. CTEM is a fully integrated and proactive alternative to strengthening your cyber security posture. It ensures organizations don’t just identify vulnerabilities – they focus on the ones that truly matter and remediate them effectively.
As a result, CTEM ensures businesses can stay ahead of attackers, reducing exposure and strengthening resilience. It is now the cornerstone of any future-proof cybersecurity strategy, and will only become more critical in the years to come.
The 5 Stages of CTEM
CTEM integrates a full range of cybersecurity disciplines into a five-stage framework. Instead of a linear start-to-finish process, CTEM adopts an iterative approach. Each stage is continuously revisited to identify new issues and adapt to changing circumstances.
Scoping
The first stage defines the scope of your CTEM processes based on your business goals, your mission-critical systems, and your risk tolerance. Key decision-makers from across your organisation should be directly involved to provide a holistic view of your needs and to set relevant KPIs. This stage ensures you can make the most effective use of your security resources.
Discovery
In the discovery stage, the focus is on building a detailed inventory of your digital assets, including hardware, software, data and cloud resources. This enables you to identify the full range of potential attack vectors, from weak configurations and poor encryption to shadow IT and zero-day vulnerabilities. This stage delivers a clear and comprehensive picture of your attack surface within the scope defined in stage one.
Prioritization
The vulnerabilities identified in the discovery stage are now evaluated according to the risk they pose to your business. This stage factors in the likelihood of a vulnerability being exploited based on the latest threat intelligence, as well as the potential consequences for your business if an attack were to succeed. Detailed risk scoring using the Common Vulnerability Scoring System (CVSS) allows you to direct your resources to the most critical issues.
Validation
This stage uses a range of interlinked cybersecurity strategies, including pen testing and red teaming , to assess the likelihood of a vulnerability being successfully exploited. This also allows you to map out paths attackers can take to target your systems and where they might end up following a successful breach. This stage prevents your organization from using limited resources to remediate issues that don’t pose a practical risk.
Mobilization
The final stage focuses on the execution of your response plan. Automated vulnerability remediation allows you to target your prioritized vulnerabilities while minimizing the demands on your security team. Importantly, this stage is not the end of the process – instead, it connects back to the scoping stage to identify improvements and monitor progress against KPIs.
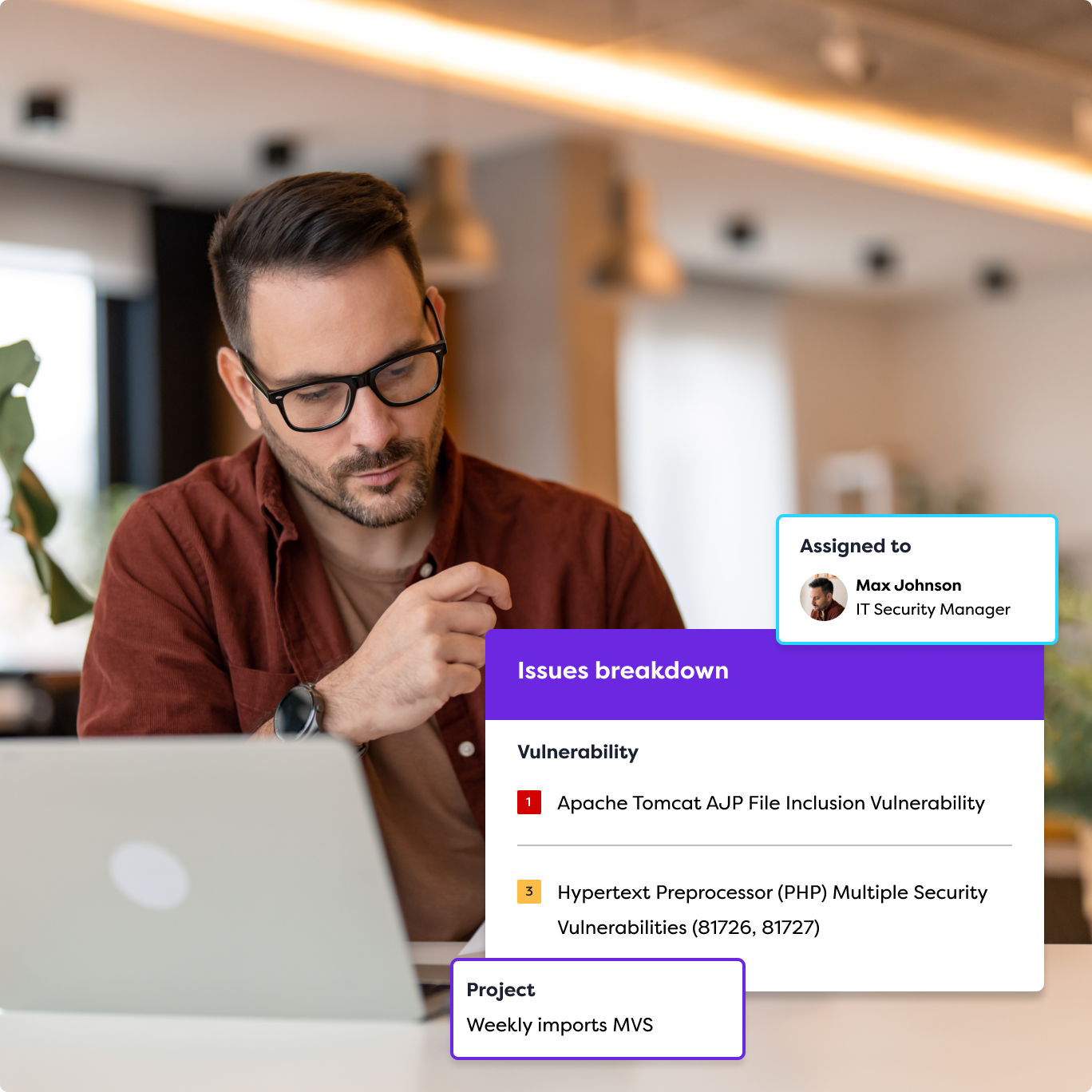
The Benefits of Adopting a CTEM Program
Implementing a robust and efficient CTEM solution can offer a range of benefits for your organization, including:
Increased Business Resilience
A CTEM program contributes to a robust incident response strategy, helping you build effective business continuity plans and keep critical functions up-and-running in the event of a breach.
Improved Security Posture
CTEM helps your organization reduce its attack surface, detect vulnerabilities, and stay ahead of emerging threats. As a result, you’ll be better prepared to navigate the fast-changing threat landscape in both on-prem and cloud environments.
Enhanced Trust and Reputation
Cybersecurity incidents don’t just pose financial and legal risks – they can have a long-lasting impact on your brand, too. Taking steps to protect critical data and keep customers safe helps you protect your reputation in an increasingly privacy-focused environment.
Reduced Blast Radius
If an attack takes place, preparation is key to minimising the impact. An effective CTEM program reduces the likelihood of a breach spreading between systems and compromising key business processes.
Lower Costs
A CTEM program won’t just minimize the costs of data breaches – it also helps integrate and focus your cybersecurity efforts on the most critical vulnerabilities. As a result, it can deliver cost savings and reduce the demands on your security teams.
Hear why the world’s top companies trust us for external penetrating testing

Boost your cybersecurity with penetration testing
How is CTEM Different From Traditional Vulnerability Management Programs?
Traditional vulnerability management takes a “point-in-time” approach. By providing a snapshot of current conditions, it can identify any existing vulnerabilities – but it can’t place them in context, evaluate their potential impact over time, or spot novel threats. As a result, organizations can find themselves prioritizing minor vulnerabilities while missing critical issues.
CTEM is a paradigm shift from this traditional reactive security posture to a proactive and predictive approach. It enables organisations to assume a stance of continuous vigilance, helping them predict, prioritize, and alleviate potential cybersecurity risks.
CTEM strategies also enable security teams to simplify their cybersecurity operations. They can streamline their response plan, measure their security maturity, and increase their resilience. Most importantly, they can align their cyber risk mitigation efforts with broader business goals.
Best Practices for Implementing CTEM
CTEM is a powerful framework for strengthening your cybersecurity posture – but only when implemented effectively. To ensure your organization secures the full benefits of CTEM, you should:
- Collaborate with cross-functional teams for a unified vision. Effective collaboration prevents silos from emerging, which can lead to gaps in your implementation or inefficient processes.
- Measure security maturity regularly to highlight areas for improvement. Using clear, verifiable metrics to measure your progress helps showcase the impact of CTEM for key stakeholders. It also allows you to measure any improvements against industry benchmarks.
- Integrate with other cybersecurity platforms. For maximum impact, integrate your CTEM program with your
external attack surface management (EASM) toolset and Penetration Testing as a Service (PTaaS) implementations for broader and deeper threat scanning. - Invest in data analytics and artificial intelligence. In a fast-paced cyber environment, you need to embrace cutting-edge technologies that can process large quantities of data and identify unusual activity and suspicious access patterns without delay.
- Emphasize risk prioritization and efficient mobilization efforts. Closing the CTEM loop means turning asset discovery and vulnerability assessments into effective remediation. This ensures that enhanced visibility translates into a reduced likelihood of breaches.
Incorporating these best practices into your CTEM implementation will maximize its impact on your organization. You will be well-prepared to build a more resilient future, no matter what new threats emerge.
CTEM Examples
- Real-time threat monitoring. CTEM enables organizations to implement systems for constant network monitoring. You will be able to detect threats in real-time and respond before they escalate. For instance, suspicious network activity can trigger alerts that prompt immediate investigations or preemptive action to prevent an attack.
- Endpoint security. CTEM can deploy advanced AI-driven solutions to identify and respond to threats at endpoints. From on-prem workstations and servers to virtual machines, CTEM enables you to quickly spot anomalous behaviour and zero-day exploits.
- Threat intelligence integration. Integrating threat feeds directly into your vulnerability management efforts enables up-to-date threat awareness and risk scoring based on real-world attack patterns. That means you can focus your remediation efforts on vulnerabilities that are being actively targeted by known threat actors.
- Cloud security. In today’s remote-first world, it’s essential that you can continuously assess and secure your cloud assets. CTEM enables you to identify and respond to misconfigurations, overly permissive access controls and other vulnerabilities without delay.
- Incident response automation. CTEM’s emphasis on automated processes accelerates your ability to respond to cybersecurity incidents and minimizes the potential blast radius of an attack – all without waiting for manual intervention.
CTEM Tools
To effectively implement CTEM, organizations can leverage a range of cybersecurity tools and technologies. Here are some tools commonly used in the CTEM process:
- Vulnerability scanners. These automated tools continuously scan systems, applications, and networks to identify vulnerabilities that could be targeted by attackers.
- Threat intelligence platforms. These platforms aggregate and analyze global threat data to identify emerging threats and new attack techniques.
- AI-driven threat detection. These solutions use artificial intelligence and machine learning to analyse threat data and detect sophisticated threats in real-time.
- Cloud Security Posture Management (CSPM) tools. These tools help organizations maintain a secure cloud infrastructure by assessing cloud configurations against security best practices and compliance frameworks.
By integrating these tools into a unified cybersecurity program, organizations can achieve continuous vigilance and stay one step ahead in identifying and mitigating risks.
What to Look for in a CTEM Platform
To secure the significant benefits that CTEM can offer, you need to work with a partner who can provide the support you need. By providing access to a full range of capabilities and targeted support, the right partner can supercharge your CTEM efforts.
When choosing a vendor to help implement your CTEM solution, look for:
- Functionality. An effective CTEM solution should incorporate vulnerability scanning, asset discovery, attack surface analysis
and risk management capabilities to cover the full five-stage CTEM framework. - Cloud and on-prem support. Your CTEM vendor should enable you to manage vulnerabilities and mitigate risks across the full range of physical and digital assets, no matter where they’re located. Your chosen solution should provide comprehensive cloud support, on-prem compatibility and the ability to manage hybrid environments.
- Seamless integration. If your CTEM platform effectively integrates with your full range of cybersecurity tools, you can streamline your operations and reduce the manual load on your security teams. This improved efficiency can provide cost savings without compromising on safety.
- Effective reporting. Clear reporting helps you evaluate your threat exposure and track progress toward KPIs. Look for customizable dashboards and user-friendly reporting tools that let you share impactful updates with key stakeholders and make progress monitoring simpler.
- Advanced capabilities. To stay ahead of emerging threats and scale your cybersecurity efforts as your attack surface grows, you need a platform that deploys cutting-edge technology. Prioritize vendors that offer AI-driven threat detection and automated vulnerability scanning and remediation capabilities.
- Functionality. An effective CTEM solution should incorporate vulnerability scanning, asset discovery, attack surface analysis
Taking these factors into account will help you choose a CTEM partner that meets your needs and delivers a robust, efficient and effective cybersecurity solution.
Our flexible pricing models
The Rootshell Platform offers two flexible pricing models to meet the diverse needs of our clients. The free trial license provides users with limited access to key features, allowing them to explore the platform capabilities before committing to a full subscription. This option is ideal for organizations looking to evaluate our Continuous Threat Exposure Management (CTEM) platform with a restricted feature set.
For businesses requiring comprehensive security coverage, the Enterprise License offers full access to all platform functionalities, including advanced analytics, automation, and integration capabilities. This fully licensed version is designed for organizations that need a robust, scalable solution to proactively manage their threat exposure.
Rootshell Trial License
The only free CTEM platform with AI active exploits built in.-
Users = 1
-
Secured Assets = <1k
-
Integrations = Up to 3 standard
-
Vulnerability Prioritization = CVE & Exploit
-
Automation Centre = No
-
Reporting = Dashboard Only
-
SLA Monitoring = No
-
Support = Knowledge Base
Rootshell Enterprise
For organizations who have global teams, multiple technologies & critical third-party suppliers.-
Users = Scalable Licensing
-
Secured Assets = Scalable Licensing
-
Integrations = Unlimited & API Access
-
Vulnerability Prioritization = CVE, Exploit & Prioritization
-
Automation Centre = Yes
-
Reporting = Export Reporting
-
SLA Monitoring = Yes
-
Support = Dedicated Customer Success Team
Building Your CTEM Program With Rootshell
As we move toward a digital-first world, organizations need a robust and efficient way to tackle the growing range of cybersecurity threats. Rootshell’s CTEM comes to the forefront in such circumstances. Its core focus is on perpetual vigilance against cyber threats. As such, it offers inherent benefits such as vulnerability identification, risk reduction, and overall increased cyber resilience.
Implementing our CTEM solutions offers a pathway to an enhanced cybersecurity posture. It enables organizations to shield their critical assets effectively. As cybersecurity evolves and surprises us at every turn, becoming a moving target for threat actors might just be our best defence.
Remember, cybersecurity is not a destination but a journey of continual improvement. The earlier we embark on it, the better equipped we are to navigate the unpredictable future of cybersecurity.
Let Rootshell guide you towards cyber safety.