Red team exercises provide a controlled, realistic method to assess security posture, simulating attacks to expose vulnerabilities in systems, processes, and human behaviour. Unlike routine vulnerability scans or automated tools, red team exercises adopt the perspective of a real attacker, uncovering risks that conventional testing might miss.
This guide explores what red team exercises are, how they work, their applications, and how success is measured.
What is a Red Team Exercise?
A red team exercise is a simulated attack designed to test how strong an organisation’s security is. A team of expert ethical hackers, the red team, adopts the mindset and techniques of potential adversaries. Their goal is to challenge existing security controls, identify weaknesses, and provide actionable intelligence that supports risk reduction.
These exercises go beyond testing individual systems. They examine the organisation holistically, including network architecture, operational processes, human behaviour, and incident response capabilities. Unlike traditional penetration testing, which often follows a checklist, red team exercises are adaptive, creative, and unpredictable.
Red teaming can include a wide range of attack methods, from social engineering and phishing to physical security breaches and simulated insider threats. The results give organisations a clear picture of vulnerabilities and the potential impact of real-world attacks.
Why Do Red Team Exercises Matter?
Red team exercises provide insight into both technical and organisational weaknesses. They test whether policies, processes, and security technologies can withstand realistic attacks. Some of the main benefits include:
Showing hidden vulnerabilities: Traditional testing may miss complex attack paths or weaknesses in human behaviour. Red teams show risks that otherwise remain hidden.
Testing incident response: These exercises stress-test an organization’s detection and response mechanisms under realistic conditions.
Improving security awareness: Employees experience controlled attack simulations, helping organisations identify areas where training is needed.
Supporting strategic decisions: Findings can inform security investments, policy adjustments, and risk management strategies.
Red team exercises help organizations reduce the likelihood of costly or damaging incidents by highlighting areas of concern before an actual breach occurs.
How Red Teaming Works
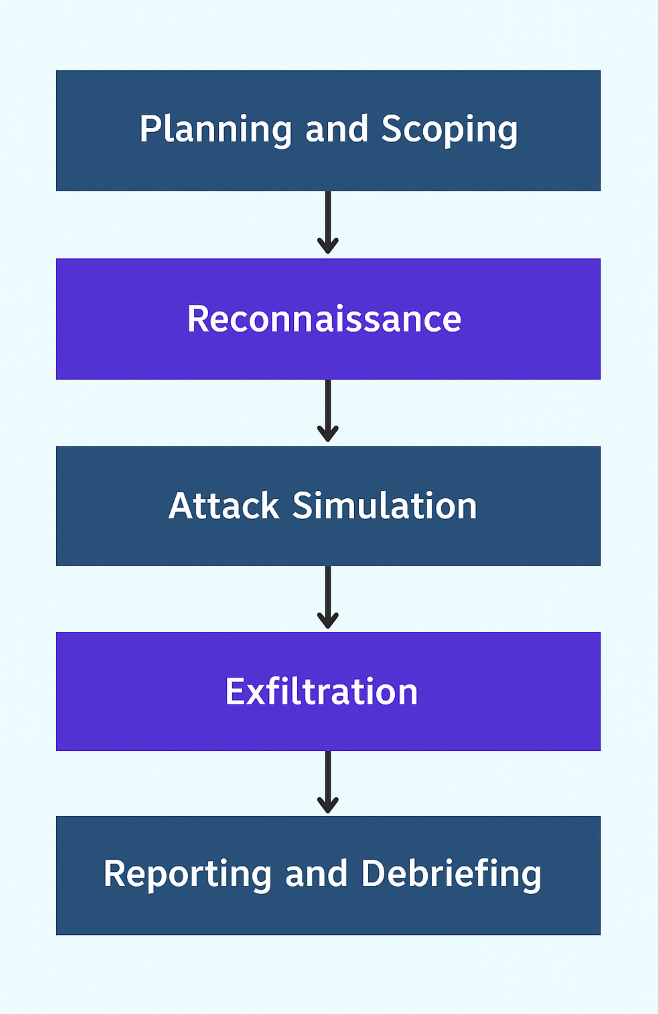
Red team exercises follow a structured approach, often resembling the tactics of real attackers. While methodologies vary, a typical exercise includes the following stages:
Planning and Scoping
The organization and red team define objectives, scope, and rules of engagement. This includes determining which systems, networks, and personnel are in scope and which are off-limits. Clear communication ensures the exercise is realistic without disrupting business operations.
Reconnaissance
Red team members gather intelligence about the organization using publicly available information, social engineering, and network scanning. This phase identifies potential attack vectors and targets.
Attack Simulation
The red team attempts to exploit vulnerabilities discovered during reconnaissance. Techniques can include phishing campaigns, network intrusions, physical access attempts, or malware deployment. This phase mirrors real-world attack strategies.
Exfiltration
Once initial access is achieved, the team attempts to move through the organization’s network, access sensitive data, or reach strategic assets. This stage tests internal controls and monitoring systems.
Reporting and Debriefing
After the exercise, the red team delivers a detailed report outlining findings, exploited weaknesses, and recommended improvements. This stage is important for translating insights into practical security measures.
Example Scenario:
A financial services company commissions a red team exercise to test employee susceptibility to phishing.
The red team sends simulated phishing emails and observes which employees click on malicious links or disclose credentials. The exercise uncovers gaps in employee training and monitoring systems.
Metrics and Measuring Success
Measuring the impact of a red team exercise requires more than simply counting successful breaches. Effective metrics evaluate the organization’s resilience, detection capabilities, and response. Common measures include:
Detection time: How quickly did the security team identify malicious activity?
Response quality: Were containment and remediation actions appropriate and timely?
Coverage of attack vectors: How many potential attack paths were exploited?
Resilience of critical assets: Were sensitive systems or data compromised?
Post-exercise improvements: How did the organization implement recommended changes?
Organisations often combine quantitative metrics with qualitative analysis to understand security weaknesses fully and prioritise remedial actions.
Red Teaming vs Penetration Testing
Red team exercises and penetration tests are often confused, but they serve different purposes:
Aspect | Red Team Exercise | Penetration Test |
Goal | Simulate real-world attacks | Identify specific system vulnerabilities |
Scope | Broad, holistic | Narrow, defined systems |
Method | Adaptive, unpredictable | Structured, checklist-driven |
Duration | Weeks to months | Typically, days to weeks |
Outcome | Thorough insight into security posture | Detailed vulnerability report |
Penetration tests provide focused insights into technical flaws, while red team exercises reveal how vulnerabilities could be exploited in combination, including human and process weaknesses.
Threat-Specific Applications
Red team exercises can be tailored to specific threats depending on organizational needs and risk profiles. Common scenarios include:
Data Breach Simulation: The red team tests the ability to access and exfiltrate sensitive information, assessing controls around encryption, access management, and monitoring.
The average cost of a data breach in the United States reached a record $10.22 million in 2025, according to IBM’s 2025 Cost of a Data Breach Report. This represents a notable increase from previous years and highlights the rising toll of cyber incidents.
Ransomware Readiness: Simulating ransomware attacks evaluates detection, response, backup procedures, and business continuity plans.
Nation-State Threats: Exercises mimic advanced persistent threats (APTs) to understand vulnerabilities to highly sophisticated adversaries.
Artificial Intelligence Attacks: Red teams simulate manipulation of AI systems, model poisoning, or adversarial attacks to evaluate AI security measures.
Tailoring exercises to specific threats ensures organizations gain practical insights relevant to their most pressing risks.
Test, Learn, and Improve with Red Team Exercises
Red team exercises give organizations the chance to measure their defenses against realistic attack scenarios, highlighting where improvements are needed across people, processes, and technology. They provide a clearer picture of how security controls stand up under pressure and where response procedures can be strengthened.
The ethical hackers at Rootshell replicate the tactics of real adversaries, using the latest threat intelligence to challenge your systems, processes, and people. The outcome is a realistic assessment of resilience that highlights gaps and strengthens long-term security. Book a demo below to experience the process in action.
Frequently Asked Questions
What is the difference between a red team and a blue team?
A red team simulates attackers, testing an organization’s defences, while a blue team defends, monitoring and responding to attacks in real time.
How often should organisations conduct red team exercises?
Frequency depends on risk profile, regulatory requirements, and organizational size, but many organizations conduct exercises annually or after major system changes.
Do red team exercises disrupt operations?
With careful planning, exercises are designed to minimise disruption, using rules of engagement and controlled simulations.
Can small organisations benefit from red team exercises?
Yes. Even small organisations face cyber threats, and tailored exercises can reveal critical vulnerabilities and improve resilience.
What qualifications do red team members require?
Red team members typically have expertise in ethical hacking, penetration testing, social engineering, network security, and sometimes physical security, often supported by recognised certifications.



