Penetration Testing as a Service
Strengthen your security year-round with our penetration testing service. Find your weaknesses before hackers can.

Trusted by companies of all shapes and sizes
Discover PTaaS in 60 seconds!
What is Penetration Testing as a Service (PTaaS)?
Penetration Testing as a Service (PTaaS) is a continuous approach to ethical hacking that delivers expert-led security testing through a dedicated platform. Unlike traditional penetration testing, which is typically performed once a year, PTaaS offers ongoing, flexible access to testing resources that integrate with your existing security program.
PTaaS combines automated tools with in-depth manual testing carried out by experienced security professionals to provide actionable insights, helping you to identify and fix vulnerabilities.
Unlike the traditional model of penetration testing, Rootshell’s PTaaS offers a more comprehensive, ongoing security posture assessment, making it a valuable asset for organizations of any service type or organization type.
At Rootshell, we offer Managed Vulnerability Scanning (MVS), Penetration Tests, Attack Surface Management (ASM), and Red Team Assessments as part of a combined PTaaS security package.
Types of Penetration Testing
From net new projects through to compliance and beyond.
Project Based Penetration Testing
A one-off security test carried out over a defined period. It focuses on specific systems or applications, often around a launch, change, or compliance requirement, to identify vulnerabilities before they can be exploited.
Business as Usual (BAU) Testing
This is structured penetration testing on an agreed number of days per year. Designed for compliance, audits, and ongoing assurance, BAU testing keeps you aligned with regulatory requirements.
Continuous Penetration Testing
Continuous Penetration Testing is an ongoing approach to security testing that regularly checks systems for new vulnerabilities as changes are made. It helps organizations identify and address risks in near real time, rather than relying on one-off tests.
Comprehensive PTaaS security package bespoke to your needs
Build your package:
- Core Continuous Testing
- Managed Continuous Testing
- Targeted Continuous Testing
- We help you choose the services that best fit your needs
- Solutions tailored to meet your team’s objectives, risk appetite, and budget
Plus receive your results an data through The Rootshell Platform .
Benefits of Penetration Testing as a Service (PTaaS)
Improve your security strategy and ensure year-round protection with Penetration Testing as a Service (PTaaS).
Continuous Security Monitoring
PTaaS provides ongoing monitoring to ensure your systems are regularly assessed for vulnerabilities and threats.
Cost-Effective Security
Access expert penetration testers without the need for a full-time security team, offering a more affordable solution to strong security.
Fast Vulnerability Detection
PTaaS enables fast identification and remediation of weaknesses, reducing the window of exposure to potential cyberattacks.
Effectively Remediate Risk
Turn testing insights into action with tailored remediation guidance, addressing critical risks and strengthening your security defenses; all powered through The Rootshell Platform.
Comply With Security Standards
Achieve compliance with key industry standards and regulations, demonstrating your commitment to safeguarding sensitive data and maintaining robust security practices.
Stay ahead of threats with our expert-led PTaaS
Get Started
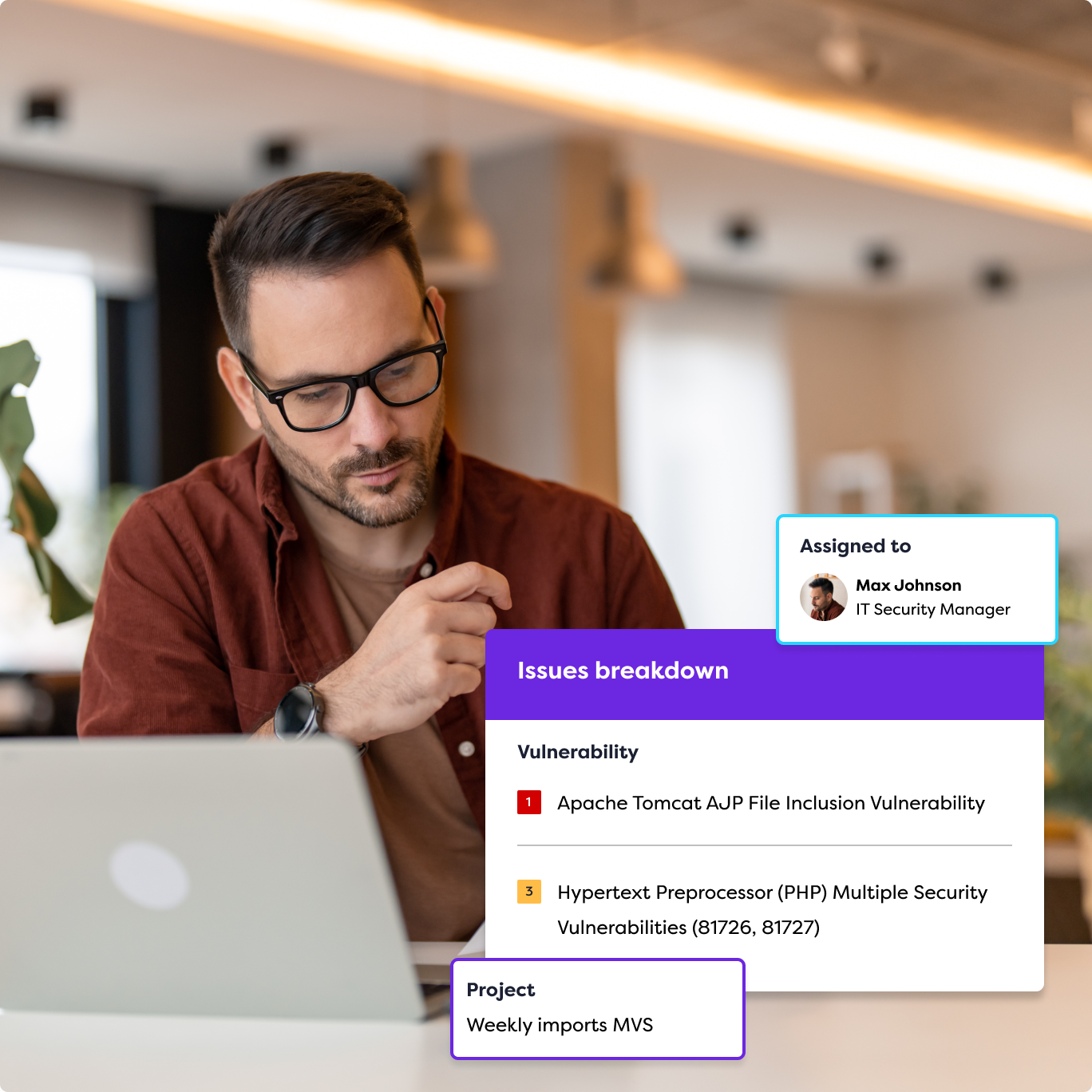
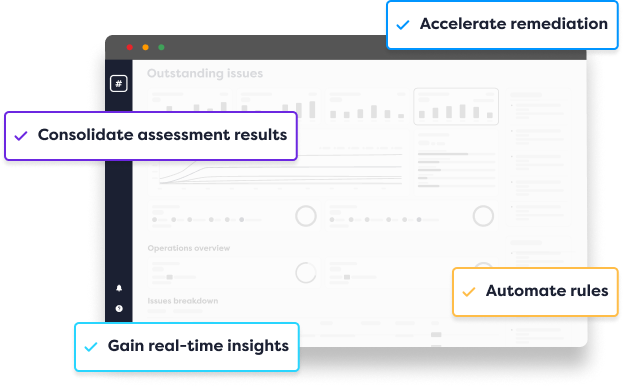
Fix Security Gaps Faster with Our PTaaS Platform
The Rootshell Platform is a neutral solution for managing vulnerabilities, placing you at the heart of your IT security.
Our Continuous Penetration Testing Process
Rootshell’s penetration testing services follow a structured and proven approach to uncovering and reporting vulnerabilities.
Initial Consultation and Planning
The process begins with understanding the company’s needs. This includes determining what will be tested, the level of access for testers, timelines, and communication protocols. For PTaaS, this phase also helps tailor the service model to the organization’s size, structure, and risk profile.
2. Information Gathering
Testers collect data about the target systems to identify potential entry points. This includes both passive reconnaissance and active reconnaissance. The goal is to build a complete picture of the system’s security posture.
3. Vulnerability Assessment
Using a combination of automated tools and manual techniques, testers identify weaknesses in the system. Automated scans quickly detect known vulnerabilities, while manual testing uncovers complex issues like logic flaws or misconfigurations that automated tools may miss.
4. Exploitation
Testers attempt to safely exploit identified vulnerabilities to understand how an attacker could gain access. This may involve privilege escalation to see what sensitive data or systems could be compromised. In a PTaaS model, this step is carefully controlled and monitored to prevent disruption to live systems.
5. Post-Exploitation
Once access is gained, testers assess the potential impact of the breach. Each vulnerability is rated based on severity and risk to help prioritize remediation.
6. Reporting
Findings are compiled into clear, actionable reports. Reports include:
- A summary of identified vulnerabilities
- Exploitation methods used
- Potential impact and risk ratings
- Recommended remediation steps
Reports are delivered through the Rootshell Platform, a centralized dashboard that allows you to track vulnerabilities, assign remediation tasks, and monitor progress in real time.
7. Remediation and Retesting
After vulnerabilities are addressed, systems are retested to make sure fixes are effective and no new weaknesses have been introduced. This ensures that organizations can confidently strengthen their security posture.
8. Continuous Exploit Monitoring
For organizations using PTaaS, the VELMA AI engine continuously monitors for active exploitation of vulnerabilities. It tracks reports from leading sources like CISA, the Zero Day Initiative, and Exploit DB, alerting clients when known vulnerabilities in their environment become exploitable.

Recognized industry leader in penetration testing as a service (PTaaS)
Challenges of Rootshell’s Penetration Testing?
While PTaaS offers many benefits, organizations should be aware of potential challenges to make the most of the service:
Third-party restrictions and compliance: Cloud providers, partners, or industry regulations may limit the scope of testing. Organizations must ensure PTaaS activities remain compliant.
Sensitive data and privacy: Testing involves accessing systems that may hold confidential data. Strong data handling and privacy protocols are essential.
Budget and cost management: Initial costs may be a concern, especially for smaller companies. Balancing investment against long-term security benefits is important.
Integration with existing tools: PTaaS must work with current security systems to ensure findings are actionable and consistent.
Skill and expertise requirements: Understanding results and implementing remediation may require skills not available internally.
Scaling and adaptability: As organizations grow, PTaaS must adapt to more complex environments and threats.
Boost your cybersecurity with penetration testing
Why Choose Rootshell’s Penetration Testing?
At Rootshell Security, we understand that penetration testing requires expertise, guidance, and continuous support. As a trusted PTaaS provider, you can be sure that your organisation’s security is in safe hands.
Powered by our platform
You will receive your PTaaS data through the Rootshell Platform, which speeds up and streamlines every remediation workflow through automation to help you resolve issues faster than ever before.
CREST-certified pen testing
Quality assured
We deliver Penetration Testing services that follow industry standards like OWASP, NIST, and PTES guidelines.
Expert advice and support
Our experienced testers offer expert guidance, delivering clear reports, advice, and step-by-step remediation instructions, prioritized by actionable insights.
Remote penetration testing
Our pen testing devices enable our testers to remotely access your organization from our secure Security Operations Centre (SOC). This allows your organization to operate as normal whilst we carry out your PTaaS.
Transform your security posture with Penetration as a Service
Book a demo
Don’t just take our word for it, hear what our customers think

Ready to take back control of your cyber security?
Frequently Asked Questions
Can’t find the answer to your question?
You can always Contact Our Team of experts for a chat!
What is included in Rootshell’s Penetration Testing as a Service?
Rootshell Security’s Penetration Testing provides penetration tests, managed vulnerability scanning (MVS), attack surface management (ASM), and red team assessments as part of a combined, continuous security solution. This is offered as a 12-month contract, tailored to your organization.
How is Penetration Testing as a Service billed?
It is a 12-month contract with flexible billing options (monthly/annually).
What is the Rootshell Platform?
We deliver PTaaS through the Rootshell Platform, which helps to speed up our clients’ remediation processes and the delivery of our services. This includes a live feed of vulnerabilities, a dashboard of key insights into your security posture, collaboration tools, a centralised location for all your results, and much more.
What systems can you perform Pen Tests on?
We can perform penetration testing services on a range of systems, including but not limited to: web applications, mobile applications, wireless networks, operating systems, hardware devices, and firewalls.
Can Penetration Testing be carried out remotely?
Yes. We can deploy a remote penetration testing box to your site, which enables our testers to remotely access your organization from our SOC. Our testers can then carry out Penetration Testing as though they were on-site.
What’s the difference between Pen Testing and Vulnerability Scanning?
A penetration test simulates a real-world attack to identify any weaknesses. It’s carried out by skilled consultants, who use the same techniques as real-world hackers; you can think of it as ‘ethical hacking’. Vulnerability scanning is carried out using automated tools and focuses on identifying vulnerabilities within software, unlike traditional penetration testing performed by a security team.