Attack Surface Management
Struggling to keep up with the challenges of an expanding attack surface? You’re not alone.
Rootshell Security helps you stay ahead by continuously monitoring your attack surface, uncovering unidentified vulnerabilities, and responding to growing threats in real time.
Trusted by companies of all shapes and sizes
What Is Attack Surface Management?
Attack Surface Management (ASM) is the process of identifying, monitoring, and reducing all potential entry points, known as the attack surface, that an attacker could exploit within an organisation’s digital environment. This includes everything from internet-facing assets like web applications, IP addresses, and cloud services, to less visible components such as third-party vendors, shadow IT, and forgotten or misconfigured systems. If your organization doesn’t have clear visibility into its internal and external assets, it cannot protect them from cyber threats.
Types of attack surfaces
Physical attack surface
Key features
- Unsecured server rooms or data centres can be exploited for unauthorized access.
- Potential data breaches are a significant risk.
- Robust physical security measures are essential for comprehensive attack surface management.
Digital/network attack surface
Key features
- New web applications add to the digital footprint and may introduce vulnerabilities.
- Continuous monitoring is crucial.
- Vulnerability management is necessary to protect against external threats.
Human attack surface
Key features
- Threat actors often target human elements as primary attack vectors.
- Training and awareness programs are essential.
- Reducing human-related risks is a key part of a holistic security strategy.
Tips for addressing diverse cyber attack surfaces
Understanding diverse attack surfaces is crucial. To effectively manage these diverse attack surfaces, organizations must employ a robust EASM strategy.
Key components of this strategy include asset discovery, implementing cybersecurity solutions, and fostering a culture of security awareness.
The benefits of this approach are clear. By recognizing and securing each type of attack surface (internal and external), businesses can significantly mitigate the risks of cyber-attacks and strengthen their overall security posture.
Discover What ASM Can Do For You
ASM solutions are designed to provide real-time visibility into an organization’s digital footprint, allowing security teams to identify potential vulnerabilities and attack vectors. ASM solutions offer a range of functionalities, including:
Asset Discovery
ASM tools help organizations discover and catalogue all digital assets, including those previously unknown, thereby minimizing blind spots.
Vulnerability Management
ASM solutions assess potential vulnerabilities within an organization’s digital infrastructure, allowing your team to prioritise remediation efforts effectively.
Improve security posture
ASM solutions integrate with other security tools, automating tasks like patch management and remediation, streamlining your security workflow.
Threat Intelligence Integration
Integrating threat intelligence feeds into ASM solutions enhances an organization’s ability to stay informed about emerging threats and vulnerabilities.
Continuous Monitoring
ASM tools provide real-time monitoring of the attack surface, enabling rapid response to any suspicious activities or security incidents.

How Attack Surface Management Works
Attack Surface Management works through several key steps that help identify, assess, and reduce your exposure to threats.
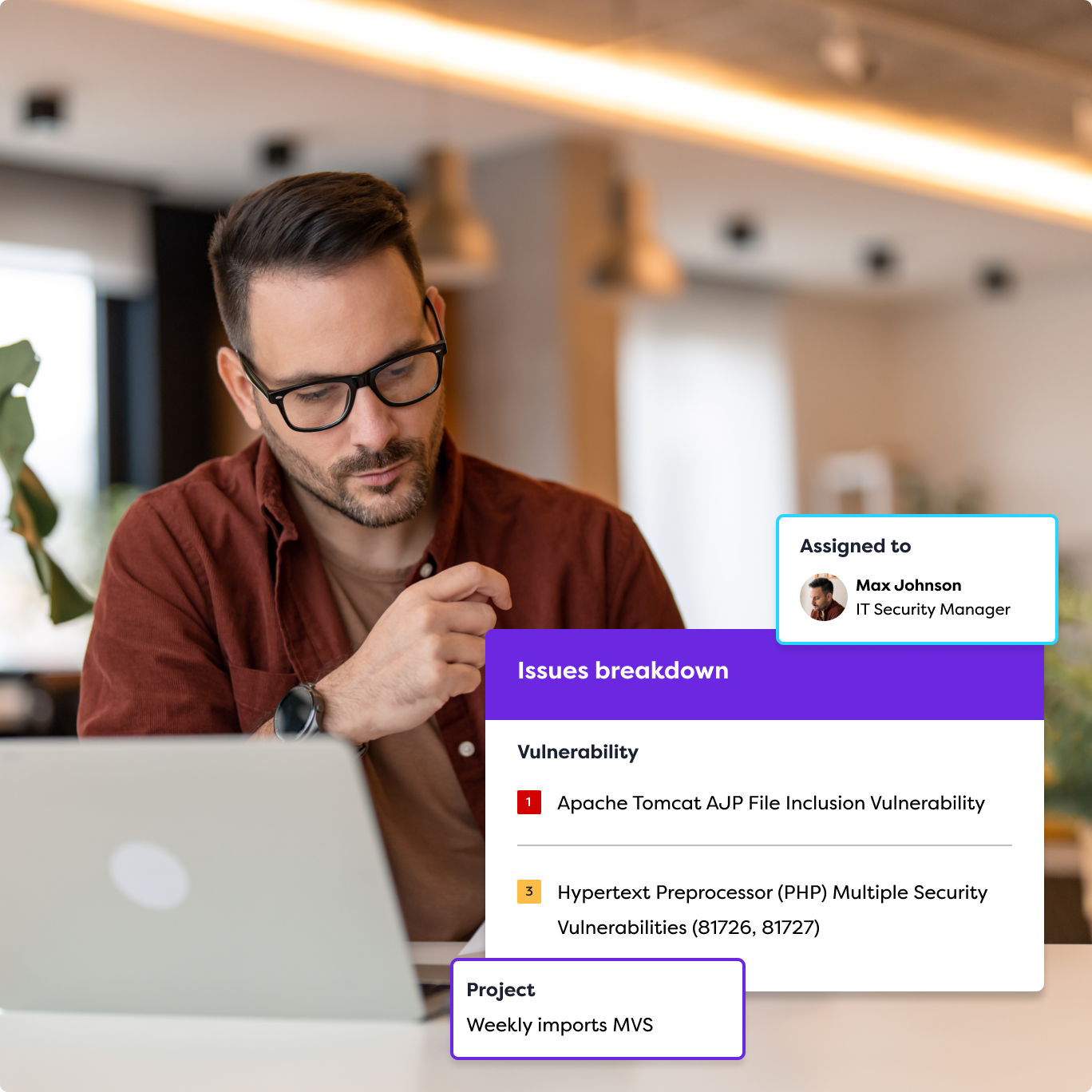
1. Asset Discovery
ASM begins with identifying all internet-facing assets across your environment.. This includes: Known assets like managed servers, endpoints, and websites. Unknown or shadow assets, such as unapproved cloud tools or forgotten infrastructure. Third-party assets from vendors or SaaS providers connected to your environment. Subsidiary assets inherited from acquisitions or partner networks. Malicious or rogue assets, such as phishing sites or leaked data on the dark web.
2. Risk Analysis
Once assets are discovered, they’re categorised, linked to owners, and assessed for vulnerabilities. ASM tools examine factors like misconfigurations, outdated software, or open ports, and determine how likely each asset is to be exploited. Threat intelligence feeds, vulnerability data, and simulated attacks (like red teaming) are often used to calculate risk scores and inform prioritisation.
3. Remediation
Security teams act on high-priority risks first, fixing vulnerabilities, securing weak points, retiring exposed legacy assets, or bringing unmanaged tools under policy. Broader controls, like MFA or least privilege access, may also be rolled out across the environment to reduce systemic risk.
4. Continuous Monitoring
ASM is not a one-time exercise. As assets change or grow, ASM tools scan and alert teams in real time to any new exposures, ensuring your security posture evolves as fast as your infrastructure does.
Hear why the world’s top companies trust us for attack surface management solutions

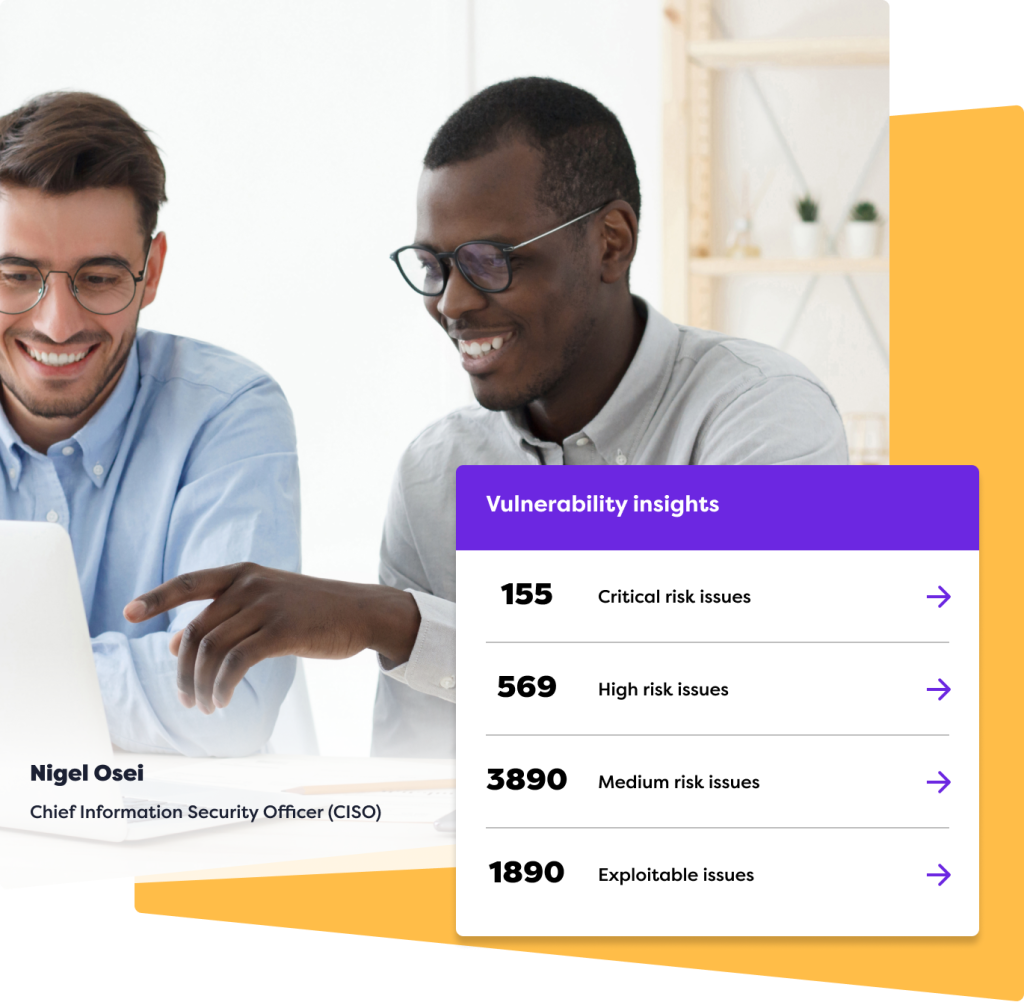
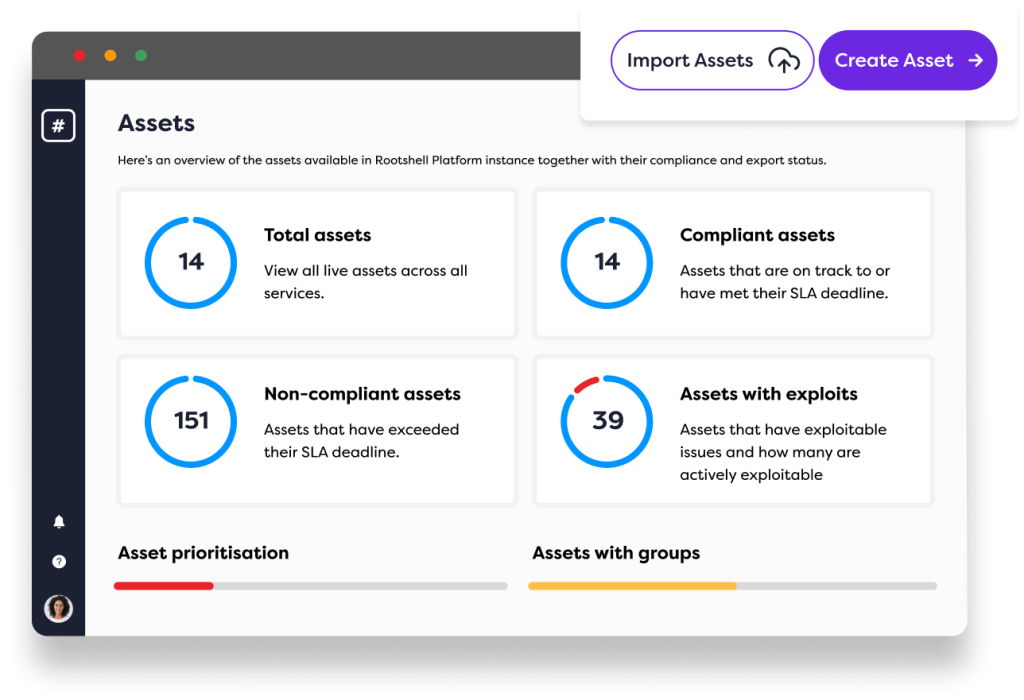
What is Included in Rootshell’s ASM services?
Our attack surface management services include a thorough vulnerability management process and external asset discovery, providing a detailed overview of potential risks within an organization’s attack surface.
Our asset discovery feature monitors for Typosquat domain and subdomain alterations, changes in public IP port/protocol configurations, and any signs of credential leakage, ensuring a proactive defence against cyber threats.
Recognized industry leader in penetration testing as a service (PTaaS)
Build your package:
- Tailored ASM scans and triaged results for internet facing web applications / infrastructure
- Actionable insights for effective risk mitigation, not just vulnerability detection
- Clear, concise reports to support confident decision-making
- Compliance expertise ensures all assessments meet industry standards
- Continuous monitoring to stay ahead of emerging threats
- Cost-effective services without compromising on quality
- Use it as a service or bring your existing vendors into the platform
- Additional offer periodic typosquat domain detection / inspection and data breach checks for leaked credentials, as an addon to the core service
Plus see your EASM, penetration testing and vulnerability data in one single view, in the The Rootshell Platform
Build your package:
- Tailored ASM scans and triaged results for internet facing web applications / infrastructure
- Actionable insights for effective risk mitigation, not just vulnerability detection
- Clear, concise reports to support confident decision-making
- Compliance expertise ensures all assessments meet industry standards
- Continuous monitoring to stay ahead of emerging threats
- Cost-effective services without compromising on quality
- Use it as a service or bring your existing vendors into the platform
- Additional offer periodic typosquat domain detection / inspection and data breach checks for leaked credentials, as an addon to the core service
Plus see your EASM, penetration testing and vulnerability data in one single view, in the The Rootshell Platform

Boost your security
posture with effective
attack surface
management
Frequently Asked Questions
Can’t find the answer to your question?
You can always Contact Our Team of experts for a chat!
Why is ASM important?
Modern IT environments are dynamic, with new assets appearing regularly. ASM helps security teams stay ahead by detecting unknown, unmanaged, or third-party assets and securing them before attackers exploit them.
How is External ASM different from traditional ASM?
External ASM focuses on internet-facing assets, those visible to attackers without credentials, while broader ASM may include internal systems, configurations, and insider threat considerations.
Why choose Rootshell for Attack Surface Management services?
At Rootshell, we offer a combination of advanced technology and expert insight. Our Attack Surface Management solution blends continuous asset discovery and vulnerability scanning with consultancy and penetration testing. Backed by a trusted platform and experienced security professionals, Rootshell helps organisations reduce blind spots and prioritise real threats.
What constitutes an “attack surface”?
An attack surface includes all entry points that could be exploited by a threat actor, such as:
- Public-facing domains and subdomains
- IP addresses and servers
- APIs and endpoints
- Cloud services and misconfigured assets
- Third-party and supply chain components
Who uses ASM tools?
ASM is typically used by:
- Security teams (SOC, Red Team, Blue Team)
- IT operations and network admins
- Compliance and risk management teams