Attack Surface Monitoring
Attack Surface Monitoring offers continuous visibility into your exposed assets, helping you detect and address vulnerabilities before they lead to attacks.
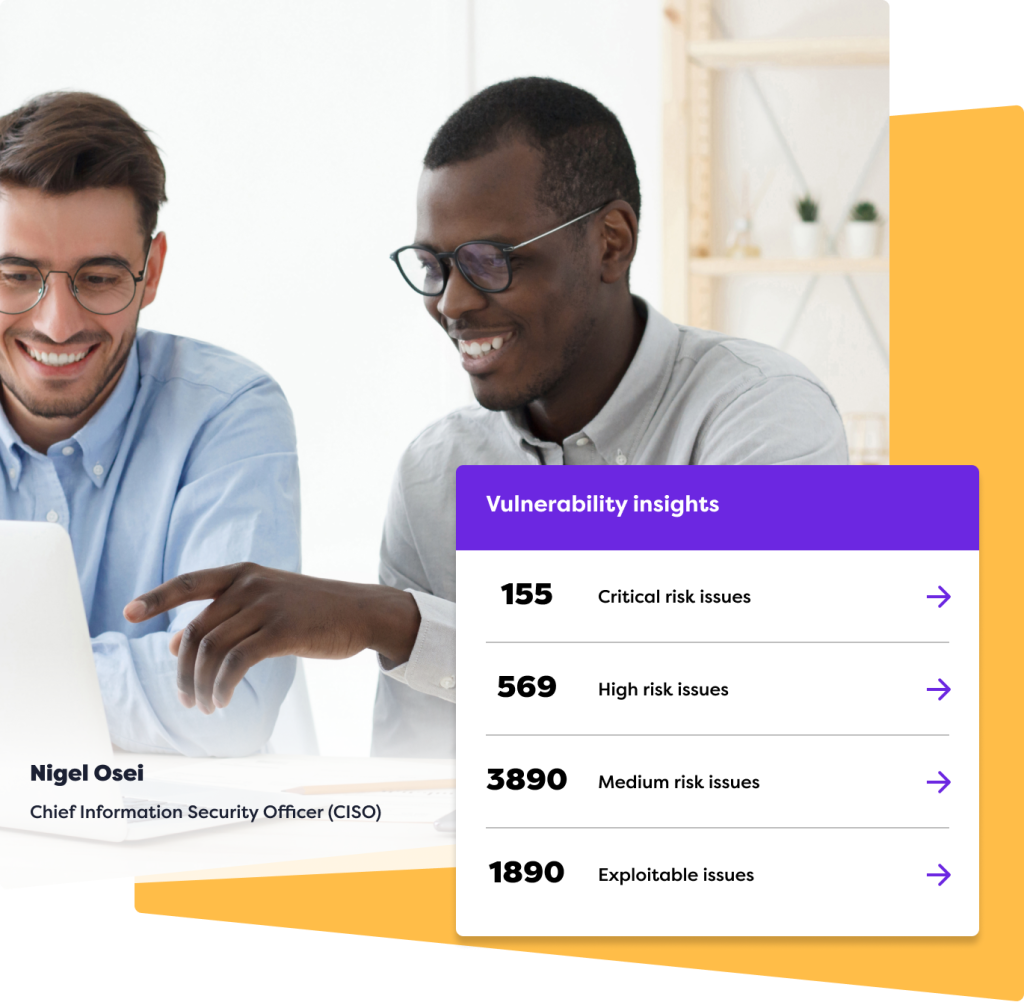
Trusted by companies of all shapes and sizes
What Is Attack Surface Monitoring?
Attack Surface Monitoring is the ongoing process of identifying, tracking, and evaluating all of your external digital assets and entry points that could be targeted by cyber attackers. This practice involves continuously looking for these assets, assessing them for vulnerabilities, and monitoring for changes. By monitoring your digital presence, you can quickly find weaknesses and take measures to address potential threats. This approach helps you reduce your attack surface, strengthens your cybersecurity defences and lowers the likelihood of data breaches or cyberattacks.
What ASM Helps You Achieve
Without ASM | With ASM |
Missed vulnerabilities | Real-time alerts on misconfigurations and risks |
Unknown assets left exposed | Full visibility over all internet-facing assets |
Delayed response to threats | Proactive threat detection and faster fixes |
Compliance challenges | Easier audits with clear documentation of the security approach |
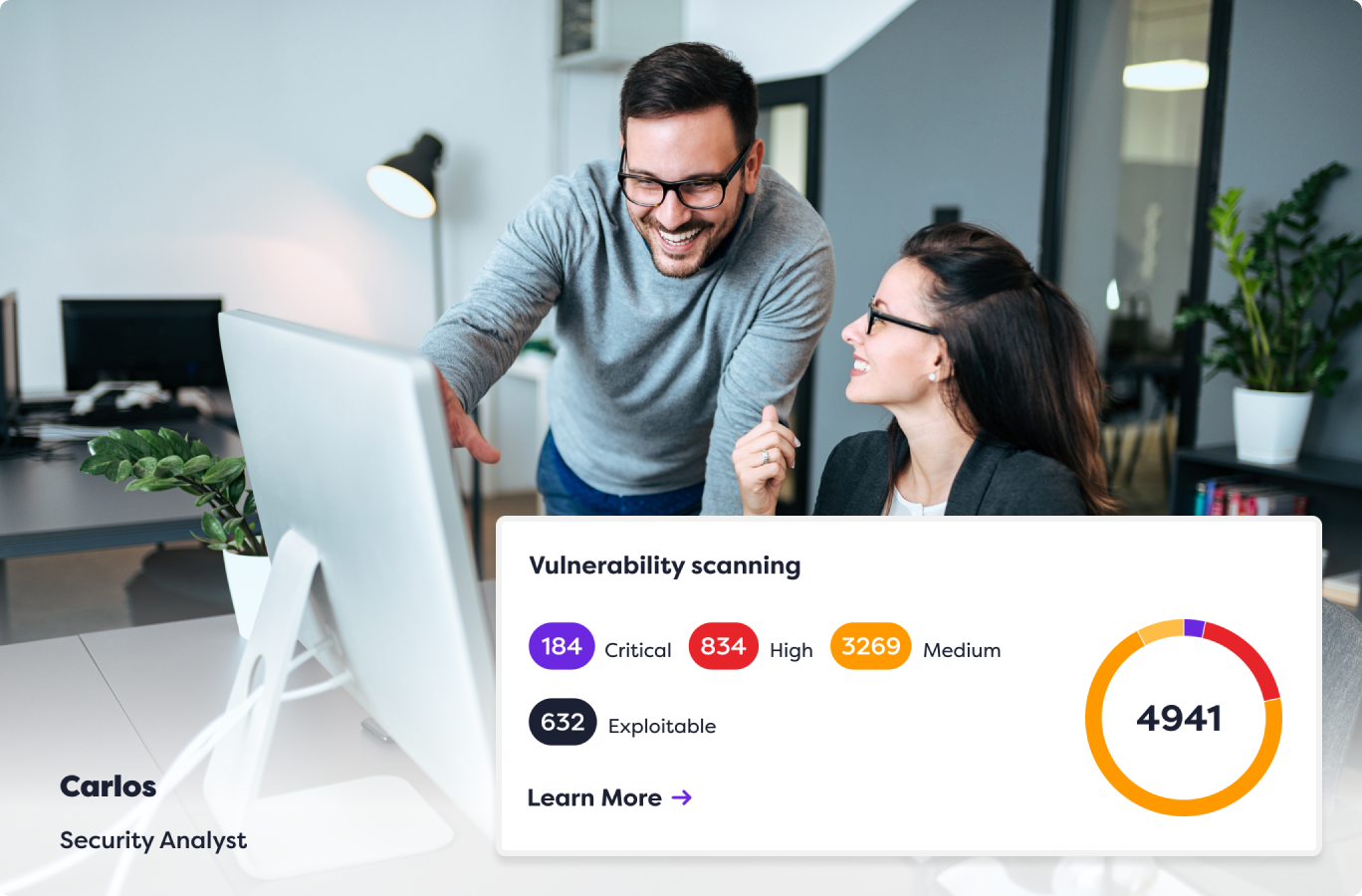
Utilize Rootshell’s platform for continuous protection
Our platform offers continuous exploit monitoring, reinforced by ongoing discovery scans and penetration testing, enabling you to leverage our expert team, advanced technology, and exhaustive methodology. This harmonious integration empowers you to unearth and remediate potential threats and vulnerabilities before malicious actors seize the opportunity.
Hear why the world’s top companies place their trust in us
Recognized industry leader in penetration testing as a service (PTaaS)
Real-World Impacts
- Prevent data breaches caused by exposed databases or misconfigured services.
- Avoid reputation damage linked to public-facing vulnerabilities.
- Protect customer trust by showing a strong security approach.
- Stay compliant with industry regulations like GDPR, ISO 27001, and PCI DSS.
Ready to get started?
Discover your needs
Dive into a personalized demo
Experience a tailored demonstration of our attack surface monitoring, showcasing how it can enhance your security posture.
Seamless onboarding

Take Action, Reduce Risks
Frequently Asked Questions
Can’t find the answer to your question?
You can always Contact Our Team of experts for a chat!
Why do I need Attack Surface Monitoring for my business?
As your organisation grows, so does its attack surface. With cloud environments, remote work, and third-party integrations, your online presence constantly changes. ASM makes sure you have real-time visibility into these risks, allowing you to manage vulnerabilities and protect yourself from cyber threats.
How does Attack Surface Monitoring work?
Our ASM solution uses automated tools to scan the internet for exposed assets tied to your organisation. We identify potential risks such as unpatched systems, outdated services, open ports, or misconfigured cloud storage. Our platform provides alerts and detailed reports on any vulnerabilities detected, allowing for quick remediation.
How often does the monitoring take place?
ASM is a continuous process. Our system performs real-time scanning of your external assets, ensuring that any new vulnerabilities are detected as soon as they appear. You will receive alerts whenever new risks or threats are discovered.
Can you monitor third-party assets and vendor risks?
Yes, our ASM service can monitor third-party assets, integrations. We help identify risks in your supply chain and external partnerships, ensuring that they don’t become an entry point for attackers.
How does Attack Surface Monitoring differ from traditional vulnerability scanning?
Traditional vulnerability scanning typically focuses on known assets and their weaknesses. ASM, on the other hand, offers a broader approach, monitoring all externally facing assets, including unknown or newly created ones. It provides proactive, continuous monitoring and prioritisation of risks.
