External Vulnerability Scanning
Identify and fix vulnerabilities in your external-facing assets. Proactively strengthen your most exposed network areas and stay ahead of emerging threats.
Trusted by companies of all shapes and sizes
What Is External Vulnerability Scanning?
External vulnerability scanning involves assessing internet-facing systems—like websites, servers, and web applications—for security weaknesses that cyber attackers could exploit.
These scans simulate how an outsider would probe your network to identify open ports, outdated software, misconfigurations, and other vulnerabilities without internal access. It’s an important part of perimeter defense, allowing organizations to proactively fix issues before they’re targeted.
Why your organization needs External Vulnerability Scanning?
Improved Perimeter Security
External vulnerability scanners protect your systems by continuously monitoring for weaknesses in web servers, cloud services, and firewalls. This helps detect and fix issues before attackers can exploit them, strengthening your perimeter and reducing your attack surface
Early Threat Detection
A benefit of external scanning is early vulnerability detection, spotting issues like outdated software, open ports, or misconfigurations before attackers can exploit them. This proactive approach helps prevent breaches and reduces the cost and effort of damage control.
Faster Remediation
Some scanners integrate with ticketing systems or security platforms to automatically create tasks or alerts when vulnerabilities are found. This speeds up response times, helping teams fix issues quickly and reduce downtime and the impact of security incidents.
Continuous, Automated Scanning
Manual testing is slow and error-prone, but external vulnerability scanners automate the process—running regularly or in real time. This ensures consistent coverage, eases the burden on security teams, and helps maintain long-term protection.
Clear, Actionable Reporting
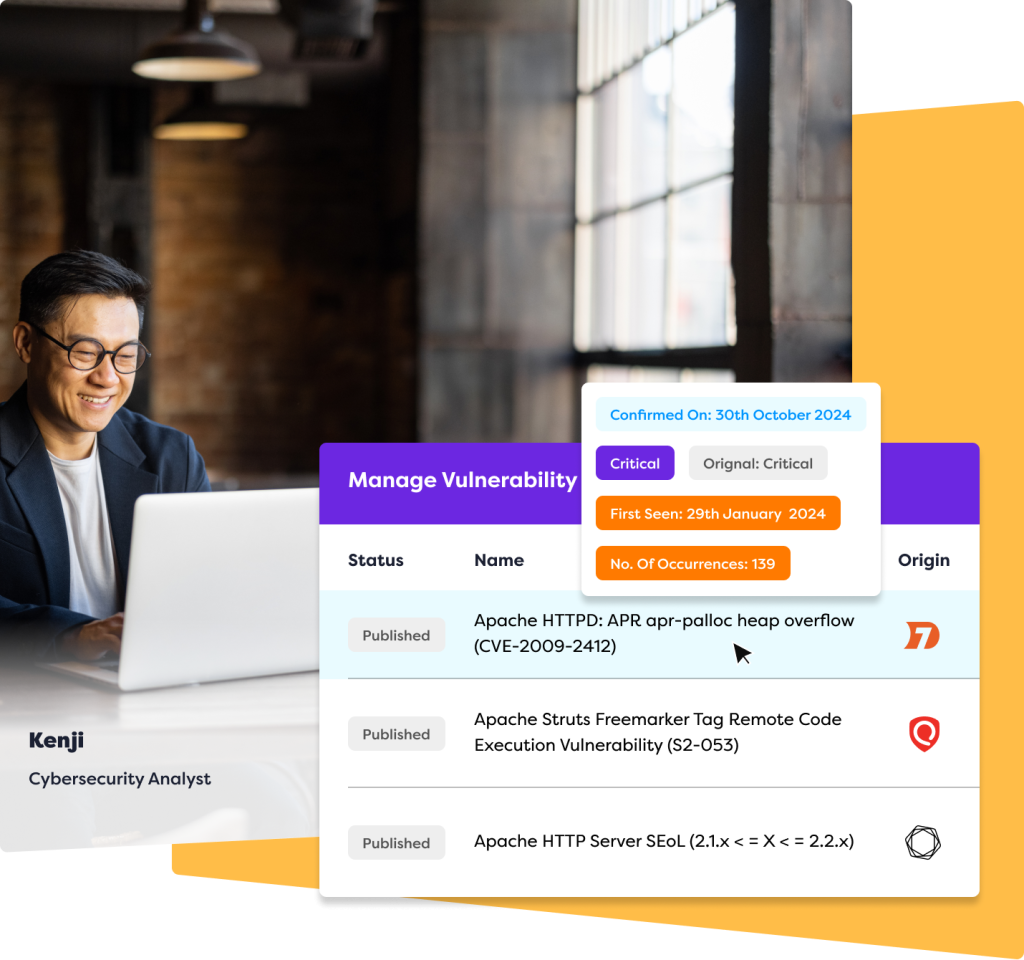
Scanners provide detailed reports that give priority to vulnerabilities based on severity, exploitability, and risk. This allows IT and security teams to focus their efforts where they matter most. Many tools also include remediation guidance, making it easier to fix issues.
Regulatory Compliance
External scanning helps organizations meet compliance requirements like PCI-DSS, ISO 27001, HIPAA, and GDPR by regularly assessing vulnerabilities. It demonstrates active management of security risks and provides audit-ready reports, simplifying documentation.
Keep Cybercriminals Out
Your network is always changing, tracking what’s exposed to the internet and what shouldn’t be can feel like a full-time job.
Intruder’s external network monitoring gives you continuous visibility of your perimeter, helping you stay in control of your attack surface at all times.
Protect your AI investments with proactive testing that stays ahead of evolving threats
Get Started
Common Issues We Detect
- Open or misconfigured ports
- Outdated software and exposed services
- SSL/TLS certificate issues
- Weak or default credentials
- Publicly accessible data or admin panels
- Vulnerable web servers and applications
Recognized industry leader in External Vulnerability Scanning
How is External Vulnerability Scanning Carried Out?
Asset Discovery and Set Up
The process begins by identifying all publicly accessible assets—websites, servers, APIs, cloud instances, and IP addresses. Once discovered, you define which assets should be scanned by entering domains, subdomains, or IP ranges. This ensures all potential entry points are in scope for continuous or on-demand scanning.
Automated Scanning
Our scanner probes your internet-facing systems from an external attacker’s perspective. It checks for:
- Open ports and exposed services
- Outdated software and unpatched vulnerabilities
- Misconfigured servers, firewalls, and devices
- SSL/TLS issues
- Publicly accessible admin panels or default credentials
- Known exploits (based on CVEs and OWASP Top 10)
Vulnerability Analysis
Each issue is assessed and ranked based on severity, exploitability, and potential impact. This helps you focus efforts on the most critical risks and reduce your exposure quickly.
4. Reporting & Remediation
You receive a detailed, actionable report with:
- Severity ratings (Critical to Low)
- Technical findings for each vulnerability
- Clear, step-by-step remediation guidance
- Links to patches or additional resources
Transform your security posture with Penetration as a Service
Book a demo
Frequently asked questions
Can’t find the answer to your question? You can always contact our team of experts for a chat!
What is an external vulnerability scanner?
An external vulnerability scanner is a tool that checks your internet-facing systems—like websites, servers, and cloud infrastructure—for known security weaknesses. It simulates the view of a hacker trying to find a way into your network from the outside.
How is it different from internal vulnerability scanning?
External scans focus solely on assets accessible from the internet, while internal scans check for vulnerabilities inside your network (like workstations, internal servers, or endpoints). Both are important, but serve different purposes.
What types of vulnerabilities does it detect?
The scanner looks for a wide range of issues, including: Open ports and exposed services Unpatched or outdated software SSL/TLS configuration errors Default or weak credentials Misconfigured servers or firewalls Common CVEs and OWASP Top 10 vulnerabilities
Will it disrupt my systems or affect performance?
No external scanning is non-intrusive. It mimics what an attacker could see outside your network and doesn’t require installing software or agents on your systems.
How often should I run external scans?
Ideally, scans should run continuously or on a scheduled basis (e.g., weekly or monthly). You should also scan after making changes to your infrastructure, such as new deployments or configuration updates.
Can it help with compliance requirements?
Yes! Many standards (like PCI-DSS, ISO 27001, and GDPR) require regular vulnerability scanning as part of a broader security program. External scans demonstrate proactive perimeter monitoring and risk management.
What happens if a vulnerability is found?
You’ll receive a detailed report outlining the issue, its severity, potential impact, and step-by-step remediation advice. This helps your team fix issues quickly and effectively.

