Penetration Testing Services
Identify critical vulnerabilities before they can be exploited; strengthen your organization’s security defenses.

Join 1,000+ leading companies who trust Rootshell Security
Removing Guesswork from your Cybersecurity Posture
In today’s digital age where cyber threats are continuously evolving, securing your organization’s IT infrastructure is more important than ever. A solid cybersecurity posture isn’t a luxury but a necessity. While businesses often invest in various security controls, these alone aren’t sufficient. The key to robust cybersecurity is understanding the existing vulnerabilities in your IT environment. Ignoring these weak links could pave the way for unauthorized access to sensitive data and systems.
This is where penetration testing services come in. These services are designed to simulate real-world attacks to reveal existing security vulnerabilities, thus providing a clearer perspective on your security posture.
Our Penetration Testing Services
At Rootshell Security, we pride ourselves on offering comprehensive penetration testing consulting. Our team of penetration testing experts employs a detailed and rigorous approach to uncover any chinks in your IT armor. Armed with a group of certified ethical hackers, we offer an extensive range of penetration testing services, including external penetration testing services and internal system assessments, to provide a 360-degree view of your organization’s security framework.
The Benefits of Penetration Testing
Prepare for a real-world attack
Penetration tests are one of the most effective ways to evaluate your security posture. By emulating the same tactics, techniques, and procedures used by sophisticated threat actors, our penetration testing services truly put your organization’s defences to the test.
Uncover critical vulnerabilities
As the risk of cyber attacks continues to increase, it’s crucial you have complete visibility of your organization’s vulnerabilities. Our penetration testing services will identify any vulnerabilities, from low to high risk, so you can take action.
Effectively remediate risk
Penetration tests provide you with the data you need to manage and resolve vulnerabilities. Our penetration testers offer expert support so you can remediate as quickly and effectively as possible.
Comply with security standards
Carrying out penetration testing services is essential for meeting a number of different regulatory standards. Our CREST-certified penetration tests will ensure your organization is compliant.
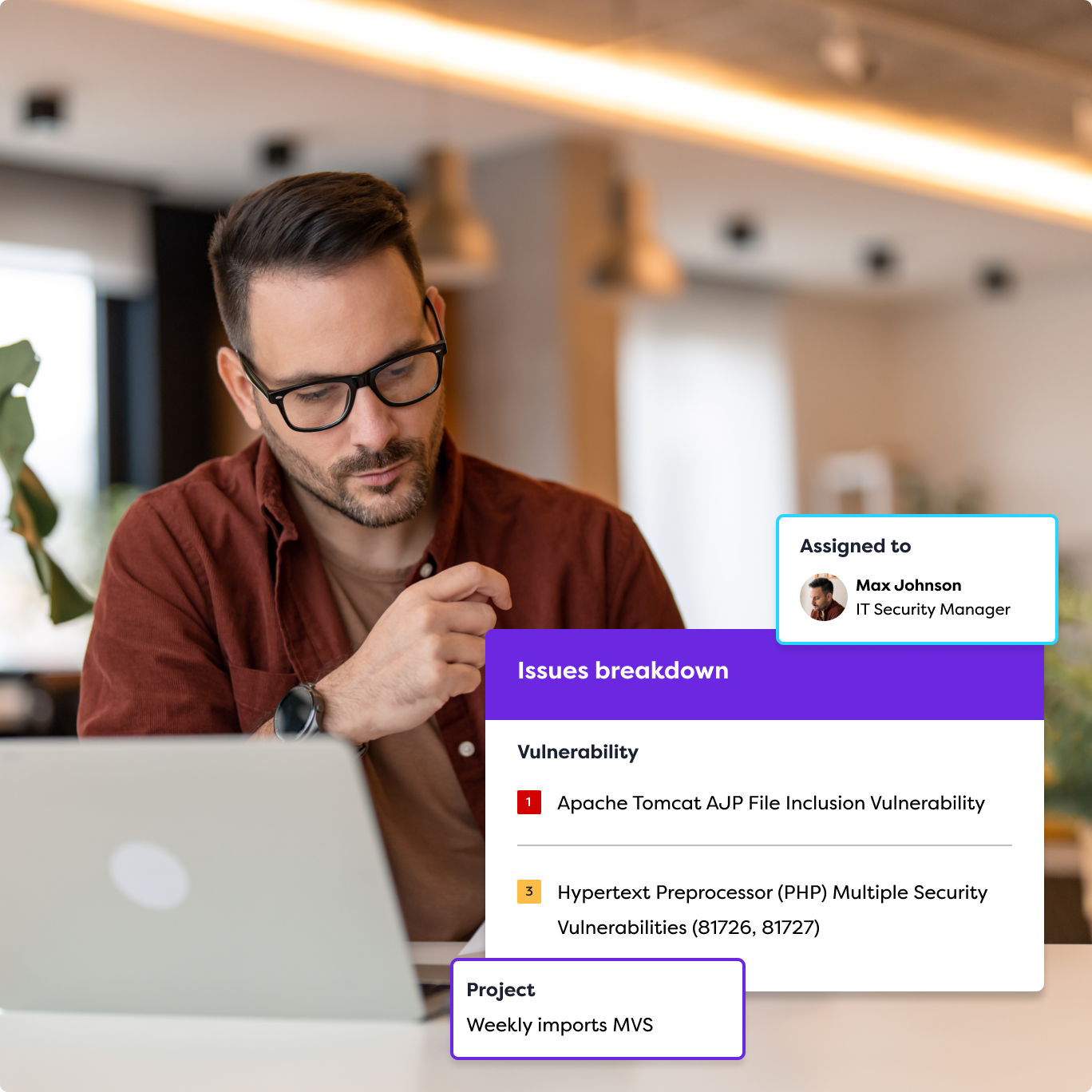
Phases of Penetration Testing
Planning and Scoping
We work closely with your organization to understand and agree on the complexity of your requirements. This gives us the opportunity to discuss any prerequisites, such as test accounts, authorization, and escalation processes. All scoping, including exchanging information, is conducted securely within the Rootshell Platform.
Pen Testing
Your penetration testing services will be performed by our experienced security consultants, who hold the highest industry qualifications, such as CREST and Offensive Security Certified Professional (OSCP). Your assigned consultants will carry out the pen testing as agreed and update you throughout the process.
Reporting
We provide you with clear and extensive pen test reporting, detailing all our findings from your penetration test. The report provides you with a clear understanding of any areas of risk or vulnerability and will form the basis of your remediation process.
Review and follow-up
Once your penetration test is complete by our ethical hackers and you have reviewed your report, you can discuss all aspects of it with your consultant. We offer expert post-pen test support and guidance on remediation activities.
Free Re-Test
We are passionate about our cybersecurity testing and it’s our firm belief that delivering a report of vulnerabilities should not complete a penetration test. Following an assessment, we will provide clear recommendations on how to mitigate against reported vulnerabilities and offer free remote retesting following remediation.
Hear why the world’s top companies trust us for external penetrating testing

Boost your cybersecurity with penetration testing
Penetration Testing as a Service
Unlike traditional penetration tests, Rootshell Security offers Penetration Testing as a managed service. This approach allows for ongoing, regular testing, ensuring that your vulnerability management is always up-to-date and reflective of any new threats or updates in the cybersecurity landscape.
Why Choose Rootshell Security?
Selecting Rootshell Security for your penetration testing needs comes with multiple advantages and we provide industry-leading services to some of the largest businesses in the UK.
- CREST-certified pen testing: CREST is an internationally recognized accreditation for penetration testing services. Our CREST-certified testers carry out your penetration testing services to the highest technical and ethical standards.
- Quality assured: We deliver our penetration testing services to industry standards, such as Open Web Application Security Project (OWASP) guidelines, the National Institute for Standards and Technology (NIST), and the Penetration Testing Execution Standard (PTES).
- Expertise: Following your penetration test, our penetration testing experts provide you with guidance and support. You will receive clear reports and advice, along with step-by-step instructions, ensuring you know exactly how to remediate and reduce risk.
- Remote penetration testing: We believe cyber security must continue, whether we can access your site in-person or not. Our penetration testing devices enable our testers to remotely access your organization from our secure Security Operation Centre (SOC). They can then carry out penetration testing services as though they were on-site.
- Technological Sophistication: We employ the latest technologies and methodologies, including social engineering tactics, red team exercises, and cloud penetration techniques, to offer the most comprehensive service available.
Contact us today for Penetration Testing Services
There’s no better time than now to reinforce your cybersecurity defenses. Rootshell Security is your go-to partner for top-notch penetration testing services. Don’t wait for an attack to unveil your vulnerabilities. Let our penetration testing specialists guide you in enhancing your cybersecurity infrastructure.
Contact us today to take the first, proactive step in solidifying your organization’s cybersecurity standing.
