External Attack Surface Management (EASM)
If you’re finding it difficult to manage the ever-growing complexities of your security perimeter, Rootshell’s External Attack Surface Management (EASM) service is your solution. In today’s dynamic and constantly evolving threat environment, we help your organization keep pace with the latest threats and optimize your cybersecurity efforts.

Join 1,000+ leading companies who trust Rootshell Security
What is External Attack Surface Management?
External Attack Surface Management (EASM) is an essential component of modern cybersecurity strategies. It involves identifying, analyzing, and securing any of your organization’s digital assets that are exposed to the internet – and therefore to potential external threats. With the average cost for a data breach now $4.8 million, your organization simply can’t afford to ignore this powerful methodology.
EASM extends beyond traditional network security, addressing the complexities of today’s interconnected digital ecosystems. Its key objective is to provide a comprehensive view of an organization’s external digital footprint. This surface includes all the internet-facing assets such as websites, web applications, cloud services, and any online platforms that can be accessed externally.
By monitoring these assets, security teams can detect potential vulnerabilities and threat vectors that malicious actors might exploit.
Why External Attack Surface Management Matters
Limited visibility into your digital attack surface increases the risk of data breaches by malicious actors. Without full visibility, unknown assets remain unprotected. But as organizations continue to expand their digital capabilities and employ a broader range of connected technologies, maintaining this kind of visibility is no simple task.
From the rise of remote working to the growing risks of shadow IT, maintaining a clear, up-to-date view of your external attack surface poses significant challenges. At the same time, malicious actors are increasingly leveraging cutting-edge technologies like generative AI to deploy ever more sophisticated attacks.
To effectively manage these challenges, organizations need to adopt an EASM strategy that incorporates continuous discovery, risk management, and vulnerability management. Utilizing advanced EASM solutions can help in identifying unknown assets, assessing potential vulnerabilities, and providing continuous monitoring to safeguard against external threats. By doing so, businesses can maintain a robust security posture in the face of evolving cyber risks.
Challenges in External Attack Surface Mapping
Mapping the external attack surface poses significant challenges for organizations in today’s rapidly evolving digital landscape. Understanding these challenges is crucial for effective attack surface management.
Distributed IT Ecosystems
The modern IT ecosystem is often a complex and distributed network of digital assets, spanning cloud services, web applications, and various internet-facing assets. For instance, a multinational corporation may have its data scattered across multiple cloud platforms, making it difficult for security teams to maintain a comprehensive view of their digital footprint. This dispersion of data and services complicates the process of asset discovery, leaving potential vulnerabilities unaddressed.
Siloed Teams
In many organizations, the security team may operate independently from other IT and development teams. This siloed approach can lead to gaps in attack surface management. For example, a development team might deploy a new application without fully communicating its details to the security team. Such gaps can create blind spots in the security stance of the organization, making it vulnerable to external threats and data breaches.
Constantly Changing External Attack Surface
The external attack surface of an organization is not static – it evolves continuously as new technologies are adopted and old ones are phased out. Keeping up with this dynamic environment is a challenge. A business, for instance, may introduce new external-facing assets as part of its expansion, unwittingly increasing its exposure to attack vectors used by malicious actors. The rapid pace of change can overwhelm security teams, especially if they lack tools for continuous monitoring and threat intelligence.
Shifting Regulatory Requirements
As cyber threats become increasingly sophisticated and the potential impacts more severe, regulatory requirements are evolving to tackle them. With the introduction of regulations such as the EU’s Digital Operations Resilience Act (DORA), organizations face more extensive and demanding compliance challenges. Without a comprehensive way to map and monitor their attack surface, organizations may find it hard to keep pace with these new requirements.
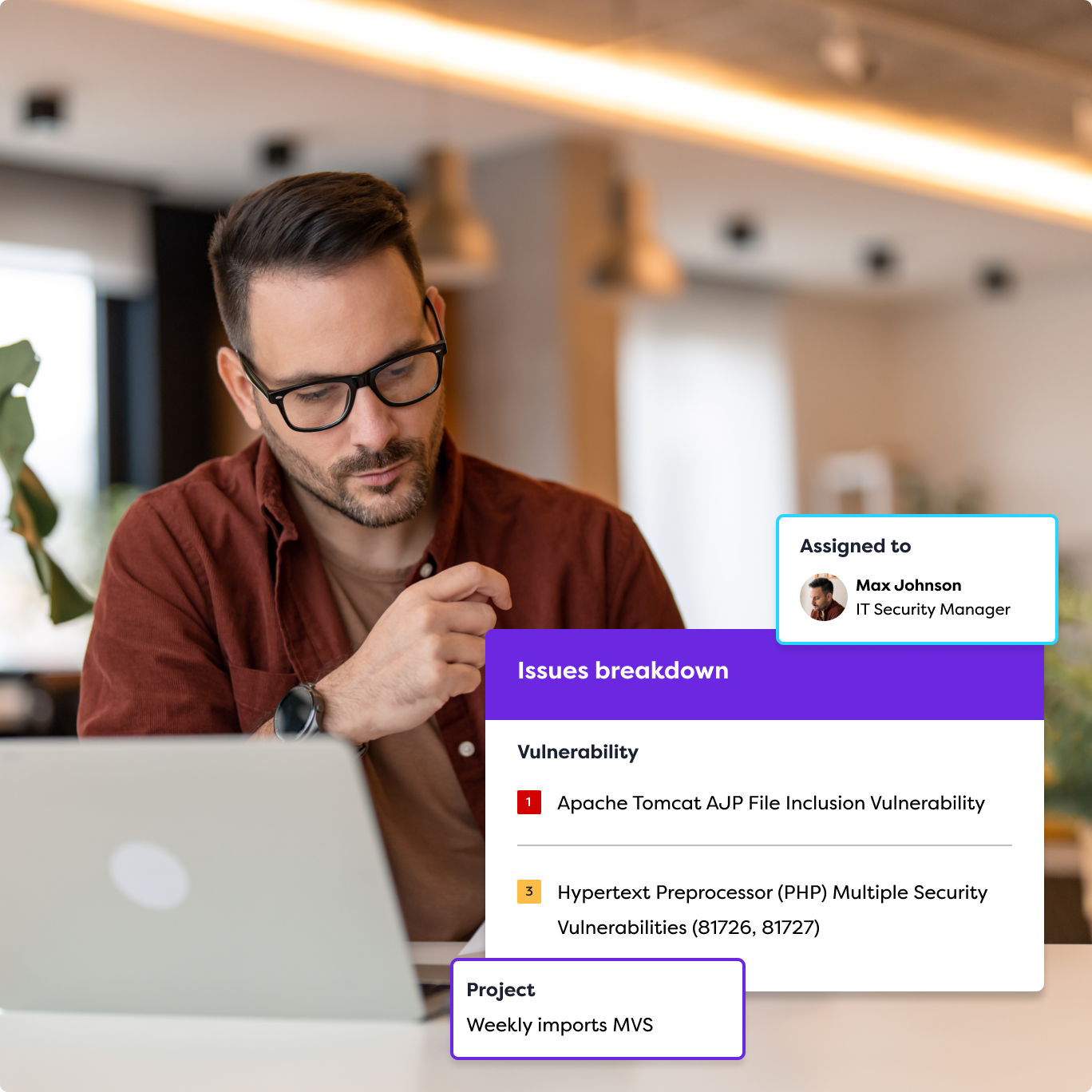
How Does an EASM Solution Help?
An EASM solution gives your organization the capabilities you need to tackle the ever-growing range of cyber threats that threaten to disrupt your operations. The benefits of an effective EASM platform include:
Identify Unknown Risks and Exposures
Asset discovery is key in uncovering unknown assets and potential vulnerabilities, meaning remediation can happen quicker.
Streamline Operations
A robust management solution integrates with existing systems for better risk management.
Get More Out of Your Existing Security Stack
Enhancing your security configuration with threat intelligence, prioritizing vulnerabilities and continuous monitoring.
Optimize IT and Security Costs
Effective vulnerability management can significantly reduce costs related to cyber threats.
Hear why the world’s top companies trust us for external penetrating testing
Boost your cybersecurity with penetration testing
Internal vs External Attack Surface Management
Internal and external attack surface management are distinct but complementary elements of an effective cybersecurity program. While they are similar in approach, they focus on different areas of your digital landscape:
- External attack surface management focuses on any digital assets that are exposed to the public internet. This includes websites and web applications, APIs, cloud services, and IoT devices.
- Internal attack surface management focuses on vulnerabilities within your internal network. This includes internal servers and databases, network infrastructure, software, and firewalls.
Both internal and external attack surface management are crucial to ensuring you have proper oversight of the cyber threats your organization faces. Together, they provide full coverage of your security perimeter and enable you to proactively remediate vulnerabilities across your entire attack surface.
Examples of EASM Capabilities
A comprehensive EASM platform will provide your organization with an extensive range of cybersecurity capabilities, including:
- Continuous discovery of digital assets. A company using EASM tools can continuously scan the internet to identify newly deployed web applications or forgotten marketing websites, categorizing them as part of their digital footprint. This process is crucial for asset discovery and ensures that all parts of the digital attack surface are accounted for and secured.
- Vulnerability management. An institution leverages EASM to regularly assess its platforms for potential vulnerabilities. By doing so, they can proactively address issues before they are exploited, significantly enhancing their security posture and protecting sensitive data.
- Mitigating risks from unknown assets. In a scenario where a global corporation acquires a smaller company, EASM can help identify and integrate the acquired company’s external-facing assets into the parent company’s risk management framework. This ensures no unknown assets remain unprotected and susceptible to cyber attacks.
- Monitoring for unauthorized access. By utilizing EASM, an organization can monitor their portal systems for signs of unauthorized access, safeguarding information against data breaches and maintaining compliance with regulatory standards.
In each of these examples, EASM plays a pivotal role in enhancing an organization’s ability to manage its external digital footprint effectively. Through continuous monitoring and threat intelligence, organizations can stay ahead of attackers, reducing the likelihood of successful cyber attacks and mitigating the associated risks.
As digital assets and threat landscapes evolve, EASM becomes an indispensable tool for organizations seeking to fortify their defences in the digital age.
Essential Components of an EASM Solution
Effectively employing attack surface management helps enhance an organization’s security setup and reduces the likelihood of successful cyberattacks. By offering a central point of collation for your cyber security efforts, EASM becomes a very powerful framework.
Let’s take a look at how we can manage the identified attack surfaces:
- Inventory and Discovery
- Mapping Attack Surfaces
- Vulnerability Assessments
- Risk Assessments
- Risk Reduction Strategies
- Continuous Monitoring
- Social Engineering Assessments and Security Awareness Training
- Third-Party Risk Management
- Regular Security Testing
By combining these various strategies, EASM enables your organization to strengthen its security posture and stay prepared as your attack surface grows and the range of external threats intensifies.
Managing Your External Attack Surface with Rootshell Security
End-to-End Service
Our comprehensive service offers ongoing monitoring, reinforced by ongoing vulnerability scans and penetration testing, enabling you to leverage our expert team, advanced technology, and exhaustive methodology. This harmonious approach empowers you to unearth and remediate potential threats and vulnerabilities before malicious actors seize the opportunity.
Cutting-Edge Technology
Rootshell Security is empowered by the Rootshell Platform, which integrates state-of-the-art tools and technology to perform external attack surface assessments and present findings. Our Platform presents clear and concise asset inventory data including software components, exposed ports and vulnerability data. By continuously updating our tool sets to stay ahead of emerging threats and vulnerabilities, we provide clients with accurate and up-to-date insights into their attack surface.
Expert Validation & Remediation Guidance
This service provides a comprehensive understanding of discovered assets and any associated risks. Our security experts are on hand to work with your organisation to discuss results, confirm the accuracy of identified assets and reported vulnerabilities, reduce the number of false positives, and reflect a suitable risk rating proportionate to the affected/identified assets and your organisation’s risk appetite. You can be confident that the reported results are scrutinised by the Rootshell team so that any remedial action can help your organisation reduce risk and improve its overall security posture.
What’s Included in Rootshell’s EASM?
Rootshell’s External Attack Surface Management (EASM) service vigilantly uncovers risks across both managed and unknown parts of an organization’s external attack surface. It works across the whole estate to find risks posed by misconfiguration and software-based vulnerabilities. The Rootshell External Attack Surface Management solution complements our broader service offerings including continuous penetration testing and managed vulnerability scanning, empowering organizations to manage their whole attack surface.
Explore Rootshell’s EASM Platform Today
The cybersecurity landscape is becoming more complex and the range and sophistication of threats continue to grow. To ensure your cyber security strategy can keep pace, your organization needs to take proactive measures – and that means adopting cutting-edge solutions like the Rootshell Platform.
The Rootshell Platform protects your organization against the latest threats while optimizing your security costs. To book an in-depth guided demo with one of our experts, get in touch today. We’ll give you a comprehensive and fully tailored overview of how our Platform can transform your organization’s cybersecurity efforts.

