Next Generation Vulnerability Management
The Rootshell Platform is a vendor-agnostic Vulnerability Management solution that puts you at the centre of your IT security ecosystem. Consolidate assessment results, accelerate remediation from start to finish, and gain real-time insight into your threat landscape.
The Rootshell Platform is Powered by and Integrates With Leading Technologies
Consolidate vulnerability management and penetration testing
The Rootshell Platform enables you to consolidate results from any scanner or penetration testing vendor. This makes it easy to analyse different assessment results alongside each other, helping you make the best decisions for your organization. (Read about our Vulnerability Management Best Practices.)
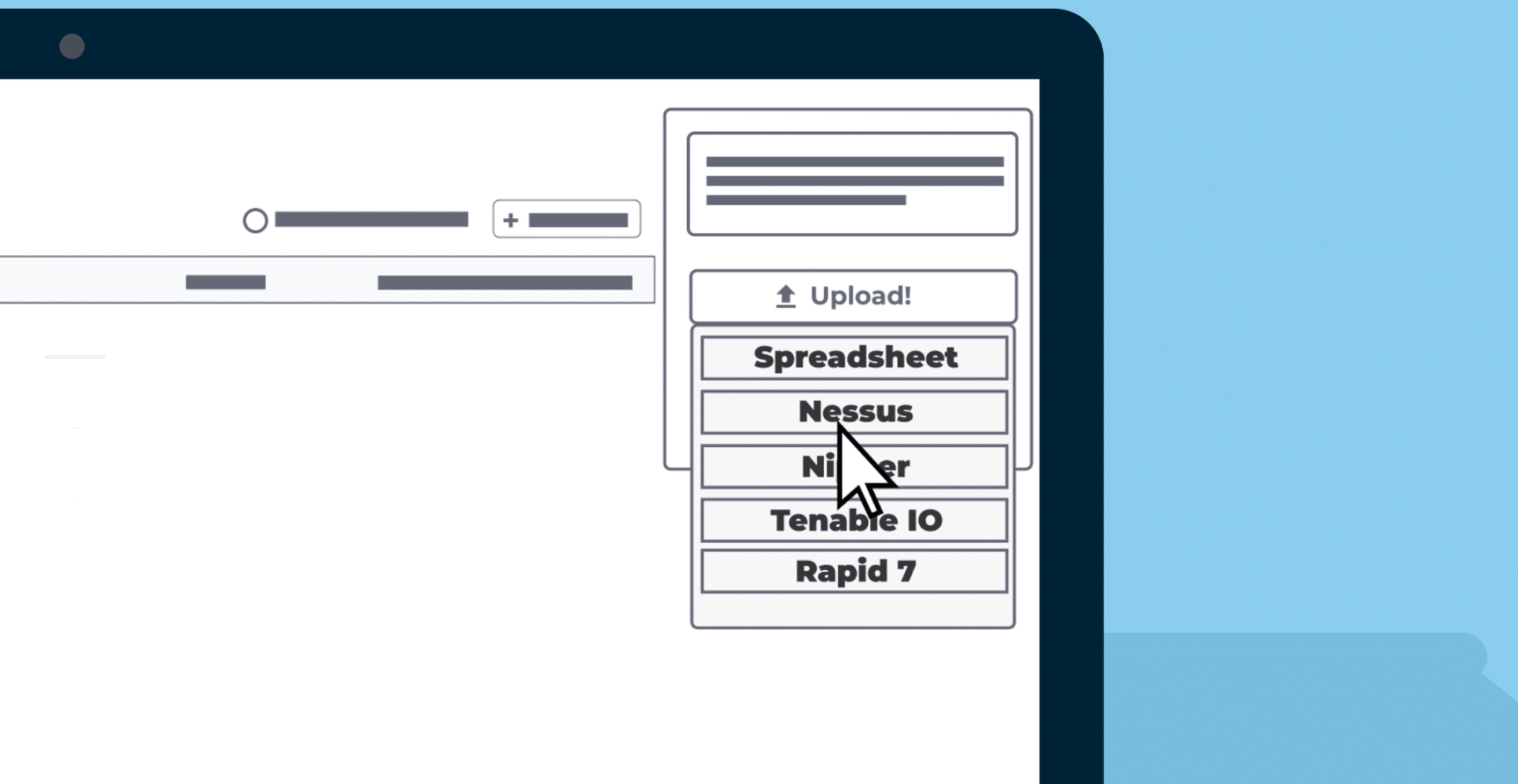
Integrate and standardize your assessment data
The Rootshell Platform generates a database of your results in a standardized format, making it easy to manage all your vulnerabilities in one place and saving your team the time spent on manual data admin.
- Manage all your vulnerabilities from one database
- Automatically standardize the format of your assessment data
- Search, filter, and tag results
Contextualize and prioritize your assessment data
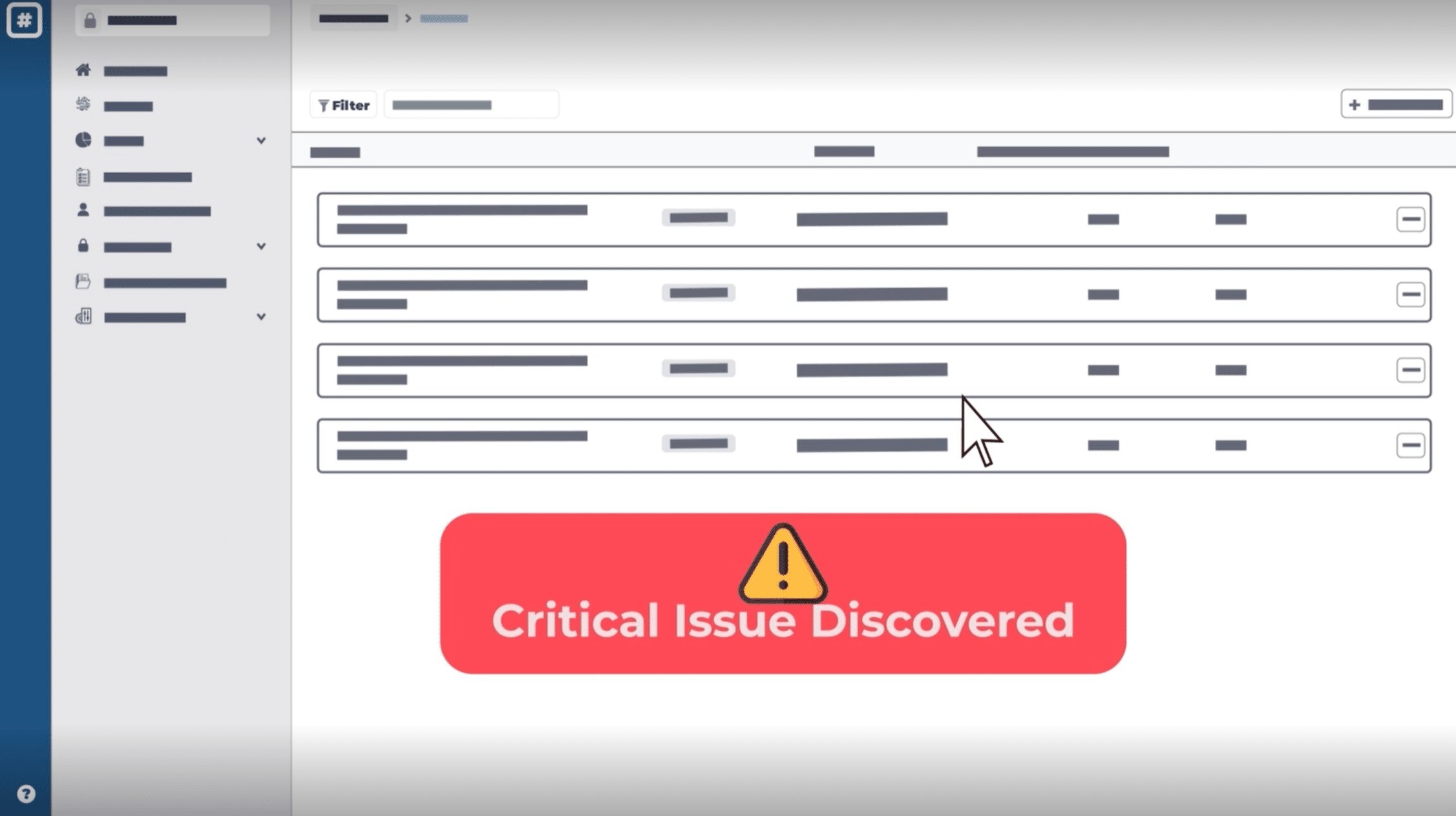
The Rootshell Platform’s industry-leading Daily Exploit Detection helps you gain context of your issues in real-time, helping you prioritize most effectively.
- The Rootshell Platform integrates with exploit resources to add context to your issues
- Be alerted as soon as an exploit becomes available for your issue
- Assign priority ratings to your assets to easily track your most important ones
Streamline your remediation workflow
By eliminating the need for spreadsheets, PDFs, and manual processes, The Rootshell Platform modernizes vulnerability management programmes and makes every aspect of your remediation workflow faster and more efficient.
-
Integrate with ticketing systems (JIRA and ServiceNow)
- Enhance collaboration between colleagues, testers, and third-parties
- Receive live updates from tests
- Streamline project management, including a calendar view for your tests
Track and validate your remediation results
With The Rootshell Platform, you can measure your remediation efforts against your service level agreements (SLAs) and track key compliance metrics, such as your monthly remediation rate.
-
Set and measure SLAs
- Monitor compliance using the Compliance Dashboard
- See your best performing system owners ranked on the Compliance Leader Board
- Allow The Rootshell Platform to mark issues as remediated on your behalf with Dynamic Remediation
Find out more about Vulnerability Remediation and Vulnerability Remediation Management Tools.
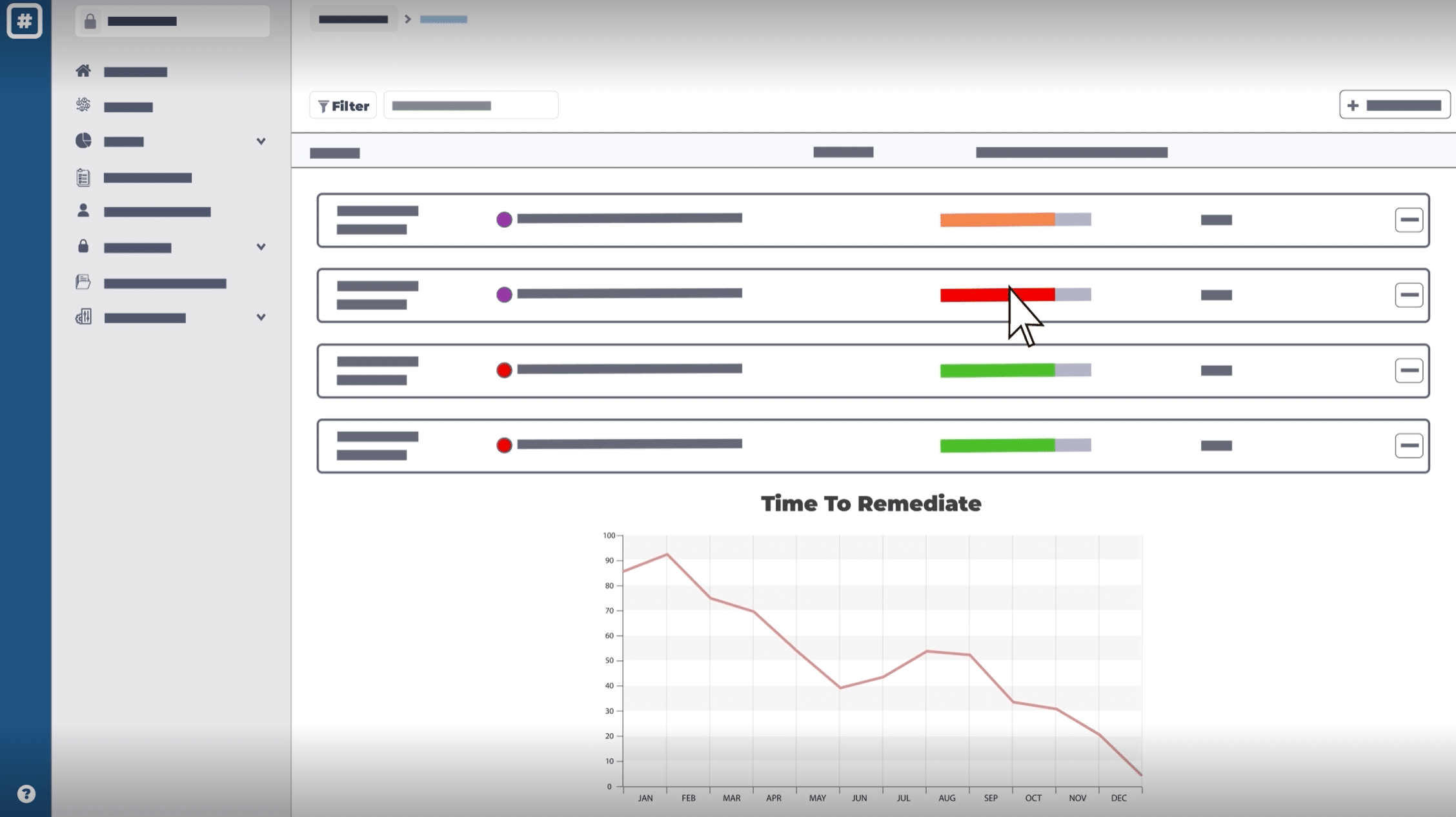
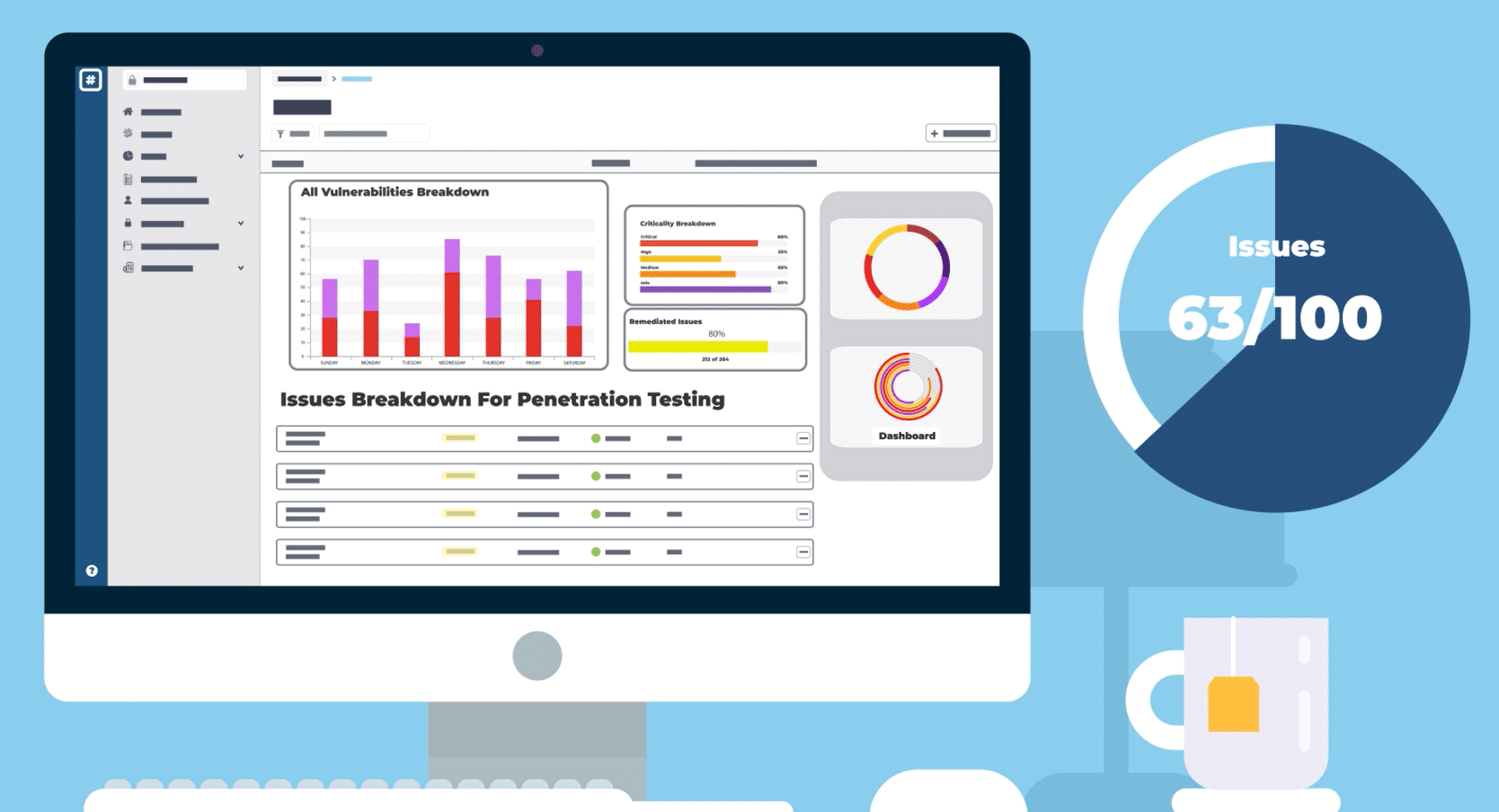
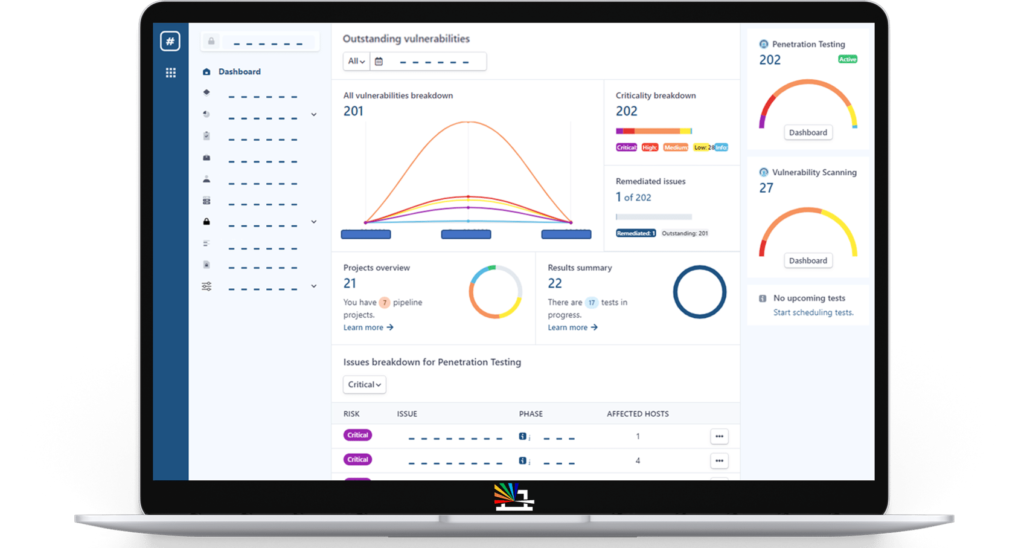
Visualize and analyse technical risk across the whole organization
The Rootshell Platform helps you gain a clear understanding of your global threat landscape and makes it effortless to continuously analyse your technical risk, with insightful dashboards and automated reporting.
-
The Dashboard puts key insights front-and-centre, including the number of exploitable issues
- See trending data across your digital estate
- The Rootshell Platform takes the legwork out of reporting, providing you with useful charts and graphs
More reading on this topic: Continuous Vulnerability Management, Threat and Vulnerability Management, Cloud Vulnerability Management