Innovate your Penetration Testing & Vulnerability Scanning Services
Unlock efficiency and best practices with The Rootshell Platform

Breaking Down Walls Between Departments
“Integrate Vulnerability Technologies – Launch or Streamline Vulnerability Scanning Services”
Combine Pentesting, Managed Scanning and OSINT services to deliver PTaaS, ASM services and more. The Rootshell Platform provides a unified delivery platform that helps your consultants work in partnership cross-discipline, breaking down what can be a very siloed nature between departments.
Optimize your penetration testing workflow using the Rootshell Platform, simplifying the entire process from the initial scoping and scheduling to results recording and reporting, as well as the quality assurance sign-off and secure delivery of final results. The platform minimizes manual tasks, offering features like scheduling, scoping, automated SOW generation and real-time reporting tools for multiple consultants, removing the need for PDFs and Spreadsheets.
What Our Partners Think…

Integrity360 procured Rootshell’s Platform to streamline the delivery of penetration testing engagements to their clients.
“We have seen dramatic time savings across our project management and testing teams. The ability to report in real-time as the test is conducted, with rich multimedia content, significantly reduces reporting time, and allows clients to access results quickly and efficiently.”
“This has improved the way we deliver our red team assessments to clients allowing them to benefit from significantly improved visibility across their penetration testing engagements with us.
Implementing Rootshell’s Platform has transformed the way we deliver reporting to clients.”
– James Hinton, Head of Pentesting at Integrity360.
Benefits by Area:
Continuous Threat Exposure Management (CTEM) Alignment
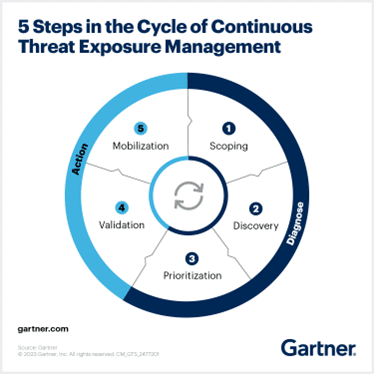
The platform allows you to consolidate, normalise and manage your assessments for your clients in line with Gartner’s Continuous Threat Exposure Management (CTEM) process:
Step 1: Scope – the organization’s attack surface, which includes both traditional and non-traditional assets and entry points. Add Assets, Asset Prioritization, Asset Grouping, and Attack Surface Management.
Step 2: Discovery – of visible and hidden assets, vulnerabilities, misconfiguration and other risks, using various tools and methods. Build and deliver cybersecurity assessments, penetration tests, managed scanning services, managed endpoint monitoring and consolidate all results into a single format and interface within the Platform.
Step 3: Prioritization – of the risks based on their business impact and likelihood of exploitation, considering attack pathways and response plans. Prioritize Vulnerabilities – Velma AI, Underlying Asset Priority, Vulnerability location, Business Context, Vulnerability Risk Rating
Step 4: Validation – of exploitability of the vulnerabilities, analysis of the potential attack pathways, and assess the adequacy of your current response plan. Daily Exploit Monitoring, Attack Pathway (due 2024). Compare current process remediation timeline expectations vs risk appetite and re-prioritise based on low-noise Threat Intel data.
Step 5: Mobilization – of the CTEM findings by reducing any obstacles to approvals, implementation processes or mitigation deployments. Assign Remediation tasks, Ticket System
Penetration Testing
The Rootshell Platform was originally built by pentesters for pentesters to enable a modern method for the delivery of penetration testing results to clients. Benefitting both the penetration testing firm to automate and reduce the overhead of the administrative and reporting functions, whilst also benefitting clients to more easily engage with pentesting firms and access results in real-time as the test is delivered.
Simplified remediation for clients means more efficient risk reduction.
The Rootshell Platform has the ability to streamline the delivery of penetration testing engagements to your clients.
Key benefits include :
- Modernise the delivery of your penetration testing with dynamic reporting including video
- Create bespoke SOW templates and automatically generate DOCX SOW’s from completed questionnaires
- Gain operating efficiencies through automation and ticket integration (ServiceNow, Jira, Freshdesk)
- Provide clients with platform access to complete questionnaires, securely share documents and manage remediation of issues identified.
- Monitor emerging exploits and leverage AI tracking of active use, alerting clients on a daily basis
- Tailor and export pentesting reports
- Add recurring revenues through premium license sales
- Securely exchange documents and data with clients
- Benefit from ‘Partner’ platform branding
Enterprise License Sales
Opportunity awaits for upselling annual recurring Rootshell Platform licenses to clients seeking to maximize the platform’s capabilities, integrating local technologies like Tenable, Qualys, Rapid7, Microsoft Defender, and more, along with seamless ticketing via Jira and ServiceNow.
- Streamline remediation process leveraging automation and integrations (ServiceNow, Jira)
- Consistent remediation management – OS, Infrastructure, Applications
- Enforce and drive a consistent patch management process
- Apply business context and value to prioritise and focus remediation
- Elevate issues (CVEs) through active exploit monitoring
- Create and track ServiceNow and Jira tickets automatically (bi-directional)
- Clearly identify when issues have been remediated (Including from ServiceNow and Jira)
- Standardise penetration testing reporting from multiple firms
- Integrate multiple vulnerability technologies (Outpost24, Qualys, Tenable…)
- Single Sign-on support for Azure and Okta
- Flexibility to switch out vendors or manage multiple vendors that feed into the platform
- Consolidate vulnerability management into a single platform
- Drive down cyber insurance costs
Experience a new level of efficiency and security with the Rootshell Platform.