
What is Rootshell’s Penetration Testing as a Service (PTaaS) Platform?
In the evolving landscape of cybersecurity, Penetration Testing as a Service (PTaaS) has emerged as a pivotal solution for businesses. PTaaS, offered by companies like Rootshell, is a comprehensive approach that integrates penetration testing into a service model, tailored to meet the unique security needs of organizations.
Unlike the traditional model of penetration testing, Rootshell’s PTaaS offers a more dynamic, ongoing security posture assessment, making it a valuable asset for organizations of any service type or organization type.
At Rootshell we offer managed vulnerability scanning (MVS), penetration tests, attack surface management (ASM) and Red Team assessments as part of a combined PTaaS security package.
How the Pen Testing as a Service Works: The PTaaS Lifecycle
The PTaaS model is designed to streamline the penetration testing process.
However, PTaaS goes beyond mere scanning and testing. It combines these tools with the expertise of seasoned security professionals, who perform in-depth analysis, providing richer insights than automated tools alone.
Rootshell’s approach to penetration testing as a service (PTaaS) is comprehensive, ensuring that every phase of the lifecycle contributes to a robust security framework. Here’s a closer look at each stage:
- Initial Consultation and Planning: The lifecycle begins with a thorough consultation to understand the organization’s specific needs. This phase involves defining the scope, including identifying key systems, applications, and network components to be tested. It’s a stage where the service type and organization type are considered to tailor the PTaaS model effectively.
- Manual Testing and Exploitation: Expert security professionals first step in to perform manual penetration tests. This phase is where the human element of PTaaS becomes crucial. Experts simulate real-world attack scenarios to validate identified vulnerabilities and attempt to exploit them (Only in a controlled agreed and safe manner). This hands-on approach often uncovers risks that automated tools might miss, particularly in complex application environments.
- Best of breed Vulnerability Scanning and Analysis: Tools are deployed to scan for known vulnerabilities across the organization’s digital infrastructure. This includes web applications, internal and external networks, and cloud environments that have been defined as in scope. The scanning process is designed to identify potential weak points, ranging from software flaws to misconfigurations.
- Risk Assessment and Prioritization: Each identified vulnerability undergoes a thorough risk assessment. Rootshell employs a risk rating system to classify vulnerabilities based on their severity and potential impact. This step is crucial for organizations to prioritize their remediation efforts effectively.
- Reporting and Strategic Insights: The PTaaS lifecycle culminates in comprehensive reporting. Rootshell provides detailed reports that go beyond mere data presentation. These reports include strategic insights, offering a rich text element that guides organizations in understanding their security posture and the necessary steps for remediation. This is all delivered through The Rootshell Platform.
- Remediation and Retesting: PTaaS emphasizes the importance of remediation and retesting. After organizations address the identified vulnerabilities, Rootshell can retest the systems to ensure that the remediation measures are effective, providing peace of mind and a strengthened security stance.
- Continuous Exploit Monitoring: This is conducted by our VELMA AI engine which continuously looks for discussions and evidence regarding Active exploitation of security vulnerabilities along with access to leading sources of exploit information such as CISA, Zero Day Initiative & Exploit DB. This works by triggering client alerts on reported CVE’s that a client has in that the vulnerabilities but have now changed and are exploitable.
Our packages are tailored to meet your team’s objectives, risk appetite, and budget. Below, you can see an example of a fully managed PTaaS package. We can help you choose the services that best fit your organisation.
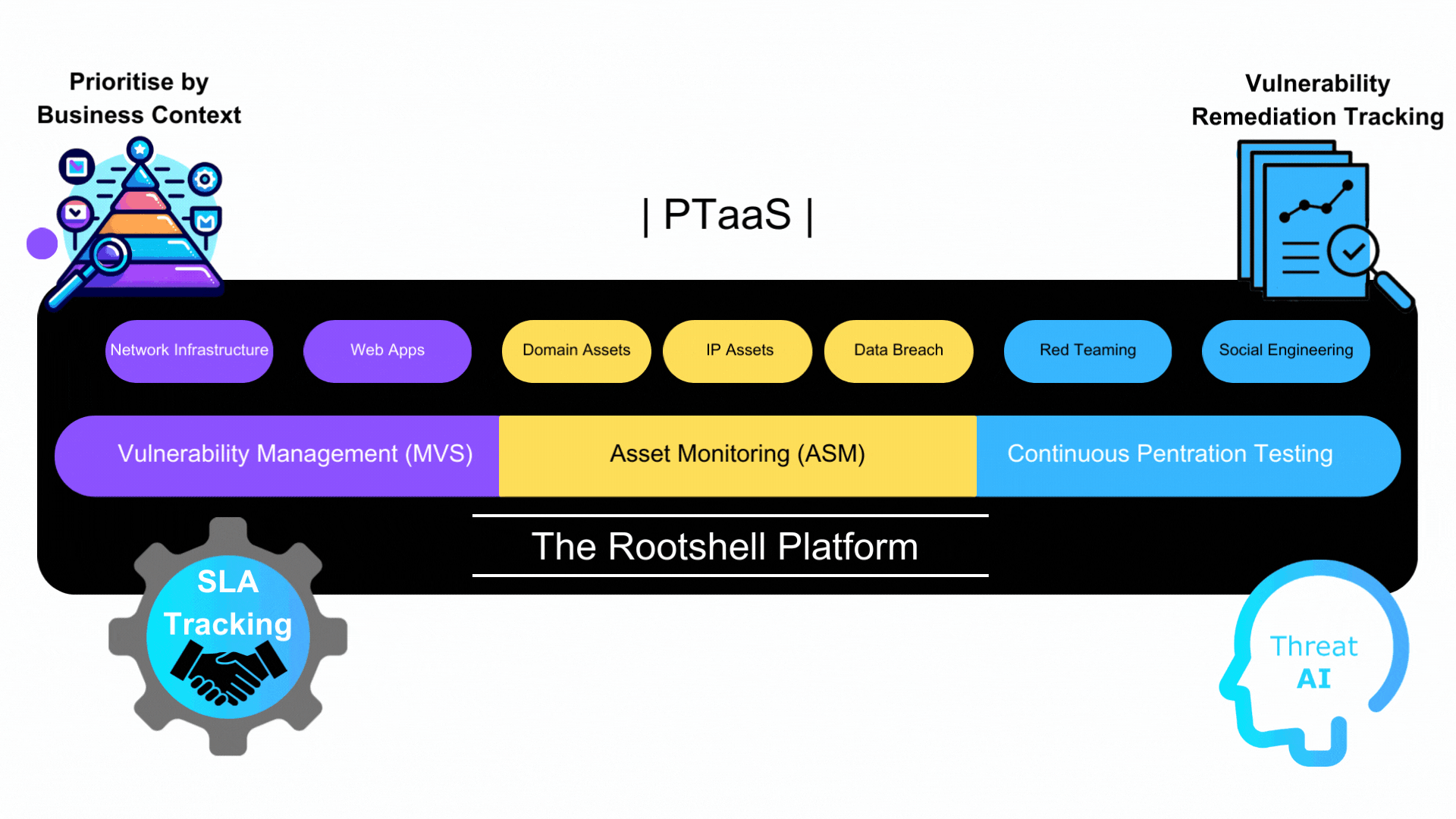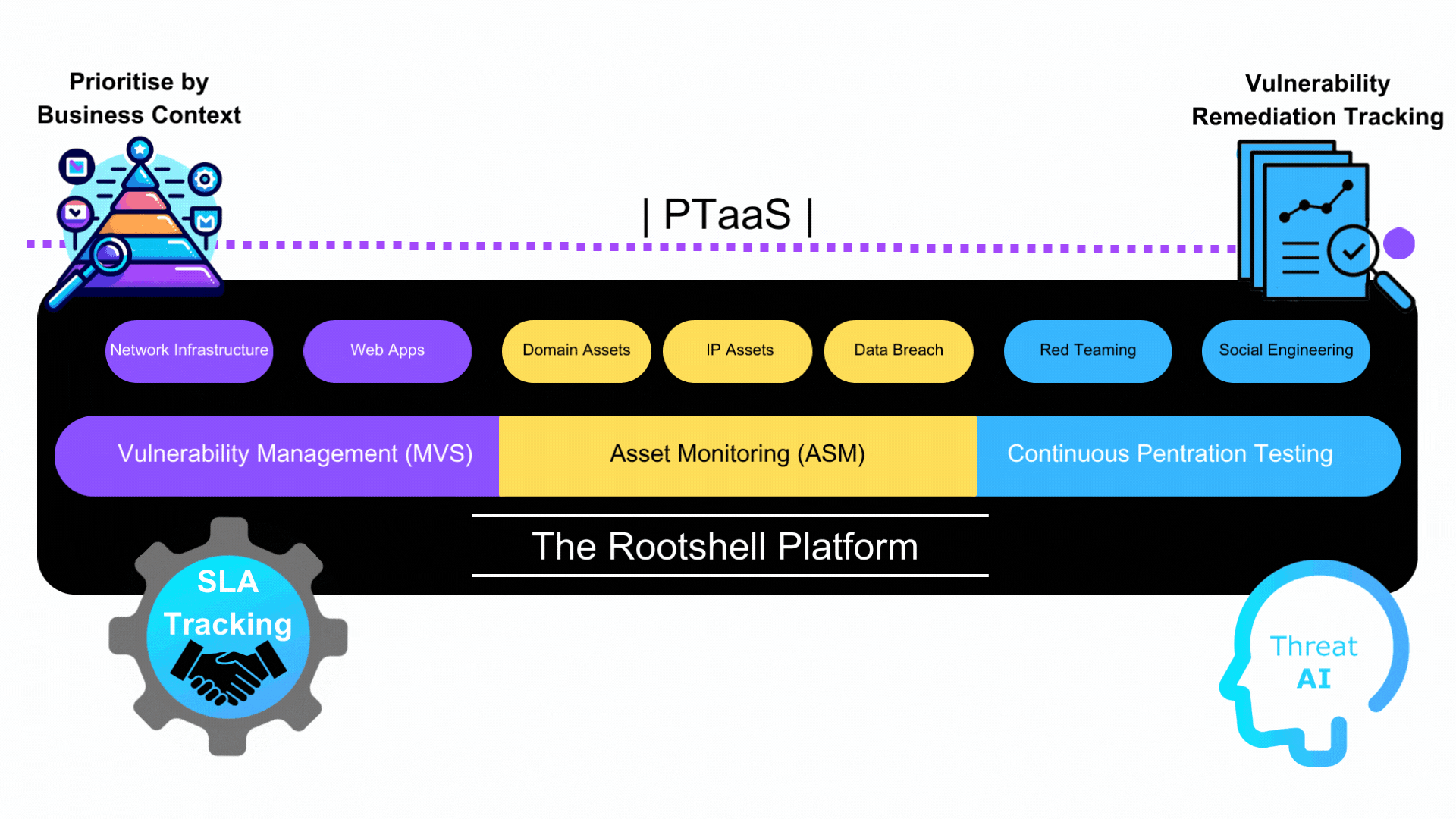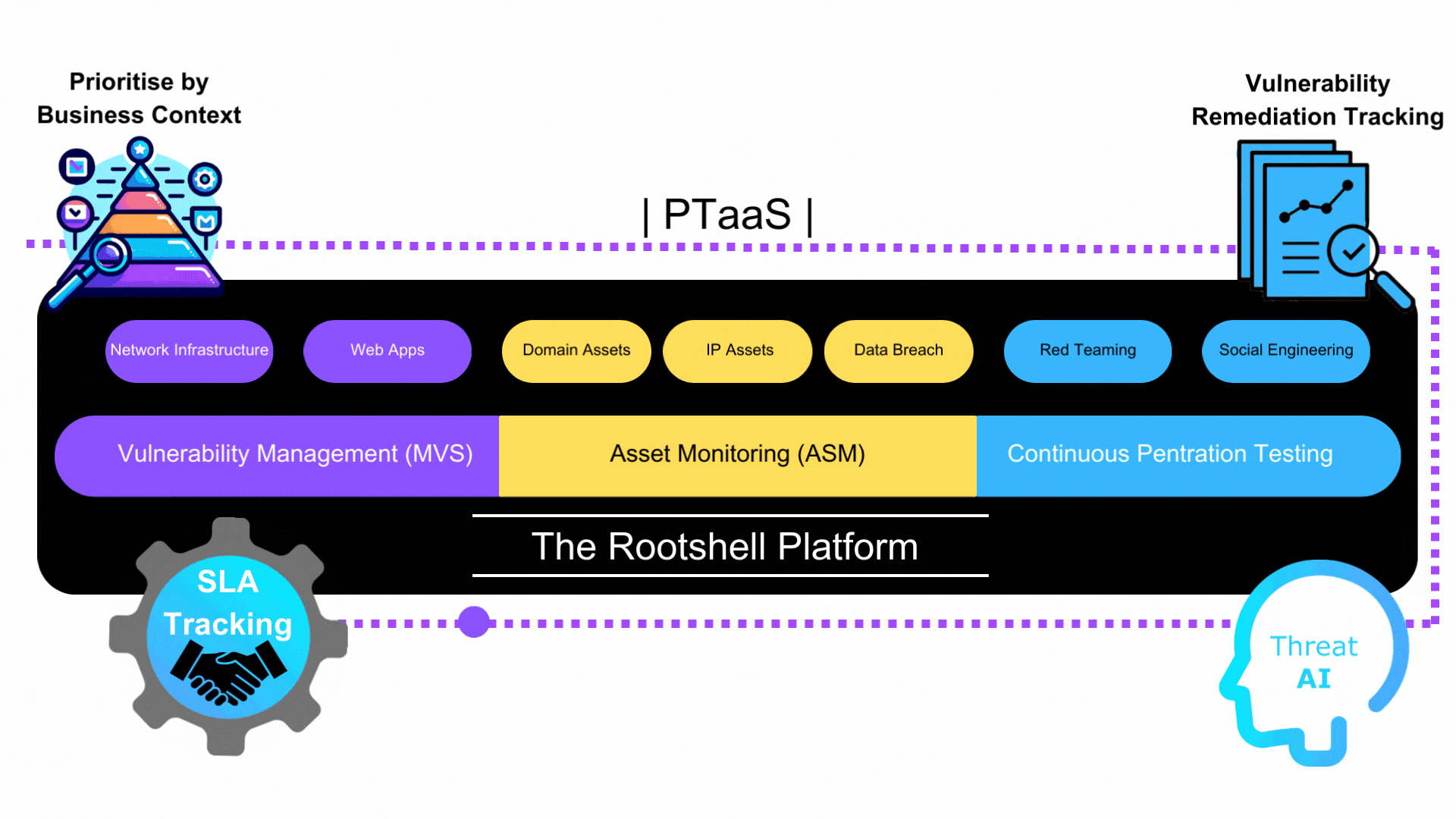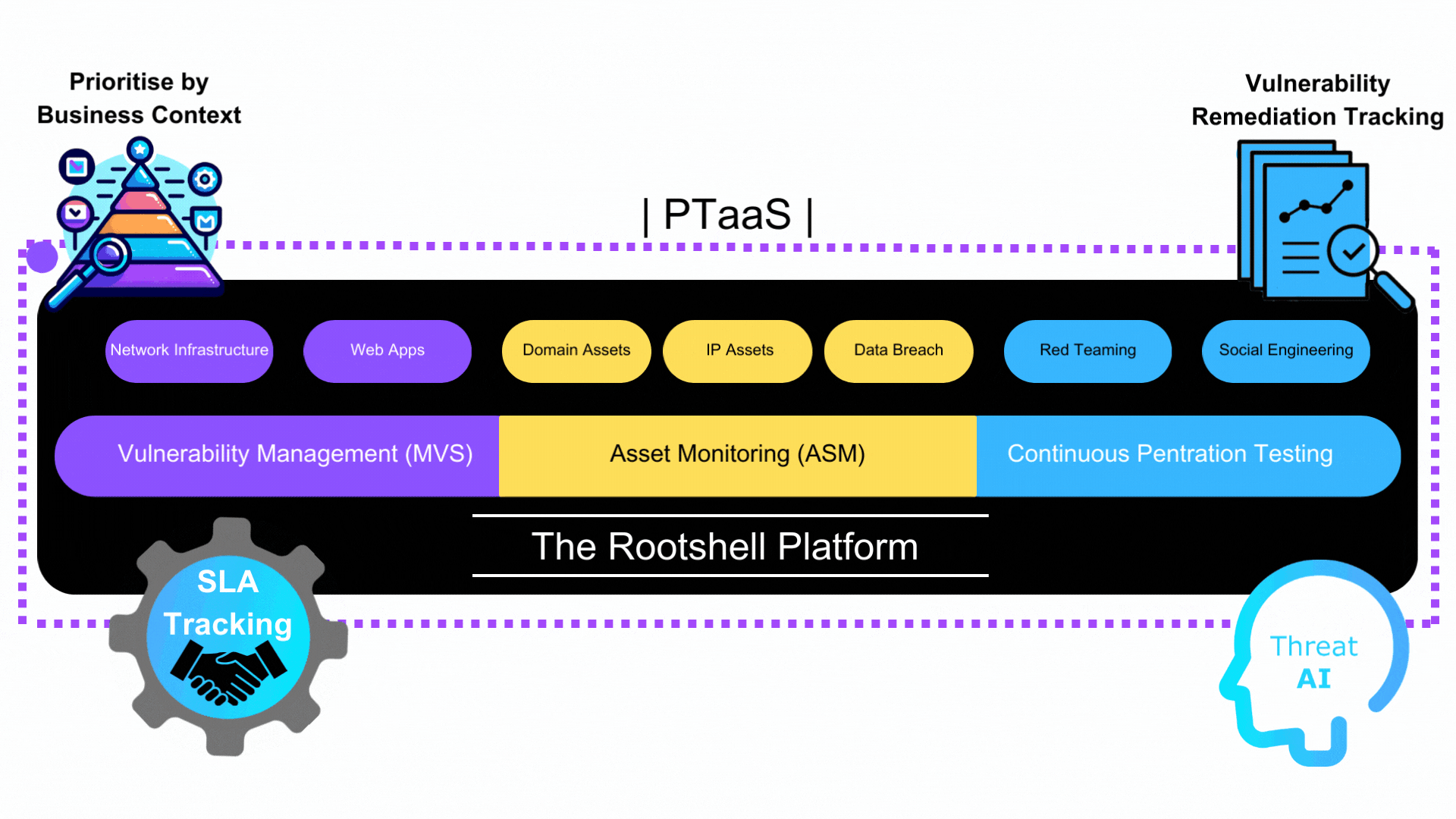
Types of Pentest
Rootshell’s PTaaS offers various types of penetration tests, each targeting different aspects of an organization’s digital infrastructure. This includes testing of web applications, networks, continuous and even cloud-based systems. Each test type is designed to simulate real-world attacks, identifying and assessing vulnerabilities in everything from simple applications to complex network systems.
We offer a range of penetration testing services. Our security consultants can help advise which types of pen testing services your organisation needs.
-
- Infrastructure Security Testing
- Web Application Services Penetration Testing
- Penetration Testing Cloud Services
- Firewall Audits
- Phishing Simulation Assessments
- Physical Security Assessments
- Social Engineering Assessments
- Wireless Security Assessments
- Operating System Build Reviews
- Hardware Device Security Reviews
- VOIP Security Testing
- SCADA Security Testing
- OWASP Mobile Application Testing
- Simulated Attack Assessments
- White Label Penetration Testing
Benefits of using a Penetration Testing as a Service solution
We’re proud to be a trusted provider of PTaaS for some of the UK’s largest organisations.
- Adopting Rootshell’s PTaaS brings a multitude of benefits to an organization’s security infrastructure. Notably, it offers an in-depth vulnerability assessment, analysis and Penetration testing, delivered by Roothshell’s automated and manual services, which is crucial for modern organizations that rely heavily on web applications and network systems. With Penetration Testing as a Service, businesses can expect:
- Year-round protection: A lot can happen between annual penetration tests. Our Penetration Testing as a Service tests your digital infrastructure year-round, so you can ensure your security posture is maintained and improved on an ongoing basis.
- Prepare for a real-world attack: Penetration tests are one of the most effective ways to evaluate your security posture. By emulating the tactics, techniques, procedures used by hackers, our services truly put your organisation’s defences to the test.
- Uncover critical vulnerabilities: As the risk of cyber attacks continues to increase, it’s crucial you have complete visibility of your organisation’s vulnerabilities. Our Pen Testing as a Service identifies any vulnerabilities, from low to Critical risk, so you can take action.
- Effectively remediate risk: Penetration Testing as a Service provides you with the data you need to resolve vulnerabilities. Our penetration testers offer expert support so you can remediate as quickly and effectively as possible.
- Comply with security standards: Carrying out penetration testing is essential for meeting a number of different regulatory standards. Our certified pen testing experts will ensure your organisation is compliant.
Challenges of PTaaS
While this service offers significant benefits, it’s important for organizations to be aware of the potential challenges associated. Understanding these challenges is key to effectively implementing and getting the most out of a PTaaS solution. The primary challenges include:
- Third-Party Restrictions and Compliance Issues: One of the notable challenges in PTaaS is navigating third-party restrictions. This can include limitations set by cloud service providers or other external partners. Organizations must ensure that their PTaaS activities are in compliance with these third-party agreements, which can sometimes limit the scope and depth of penetration testing. Additionally, there may be industry-specific compliance requirements that need to be addressed, such as those pertaining to data protection and privacy.
- Sensitive Data Handling and Privacy Concerns: PTaaS involves probing into an organization’s systems and networks, which may contain sensitive or confidential data. The handling of this data during the penetration test process is a critical concern. Ensuring that the PTaaS provider has robust data handling and privacy protocols is essential to prevent any data breach or unauthorized access during the testing process.
- Budget Limitations and Cost Management: While PTaaS can be cost-effective in the long run, initial budget constraints can be a challenge for some organizations, particularly small and medium-sized enterprises. Allocating funds for PTaaS requires understanding its value proposition compared to traditional penetration testing methods. Organizations need to balance the immediate costs with the long-term benefits of improved security posture and reduced risk of cyber incidents.
- Integration with Existing Security Tools and Processes: Integrating PTaaS into an existing cybersecurity framework can be complex. Organizations must ensure that the PTaaS solution works seamlessly with their current security tools and processes. This integration is critical for maintaining a consistent security approach and for the effective utilization of PTaaS findings in the broader security management strategy.
- Skill Gaps and Expertise Requirements: PTaaS requires a certain level of expertise, both from the provider’s side and within the organization. Understanding the results and implementing the recommended remediation strategies may require skills that the internal team may not possess. Ensuring that the organization has or can access the necessary expertise is crucial for maximizing the benefits of PTaaS.
- Scaling and Adaptability Challenges: As organizations grow and evolve, their Pentesting as a Service solution must be able to scale and adapt accordingly. This includes being able to handle increased data loads, more complex network environments, and evolving security threats. Selecting a provider that can scale and adapt its services to meet changing needs is essential for long-term cybersecurity effectiveness.
What to look for in a PTaaS Provider?
When selecting a PTaaS provider, organizations should consider:
Human, Hands-On Approach: A provider that offers a blend of automated and manual testing ensures a thorough assessment.
Dedicated Expertise: Look for a team with deep expertise in various pen testing methodologies and cybersecurity challenges.
Useful Reporting Capabilities: Comprehensive and understandable reports are vital for actionable insights and effective remediation.
Support for DevSecOps Teams: A Pentesting as a Service provider that aligns with DevSecOps principles can better integrate security into the software development lifecycle.
Securing your digital landscape with Rootshell:
Rootshell’s Penetration Testing as a Service stands as a cutting-edge solution, offering a dynamic, comprehensive, and adaptable approach to cybersecurity. Here’s why we’re proud to be a trusted provider of PTaaS for some of the UK’s largest organisations.
- Powered by our platform: You will receive your PTaaS data through Rootshell’s Platform, which accelerates and streamlines every remediation workflow through automation, to help you resolve critical issues faster than ever before.
- Certified pen testing: CRESTCyberScheme are internationally recognized accreditations for penetration testing services. Our certified testers work to the highest technical and ethical standards.
- Quality assured: We deliver Penetration Testing as a Service to industry standards, such as Open Web Application Security Project (OWASP) guidelines, the National Institute for Standards and Technology (NIST), and the Penetration Testing Execution Standard (PTES).
- Expert advice and support: Our highly experienced testers provide you with expert guidance and support throughout. You will receive clear reports and advice, along with step-by-step instructions, ensuring you know exactly how to remediate and reduce risk.
- Remote penetration testing: Our pen testing devices enable our testers to remotely access your organisation from our secure Security Operation Centre (SOC). This allows your organisation to operate as normal whilst we carry out your testing.


