Continuous Vulnerability Management
Today’s threat actors work around the clock to quickly exploit changes in organizations’ systems.
By moving towards continuous vulnerability management practices, IT security teams can close the gaps between security assessments and significantly reduce risk.
The Rootshell Platform is a vendor-agnostic vulnerability management solution that makes it effortless to continuously monitor your threat landscape and remediate issues. It puts you at the centre of your IT ecosystem and equips you with the tools you need to successfully manage your vulnerabilities on an ongoing basis.
How to Implement Continuous Vulnerability Management
Here are just some of the ways our platform helps you implement continuous vulnerability management.
Centralize Your Vulnerabilities
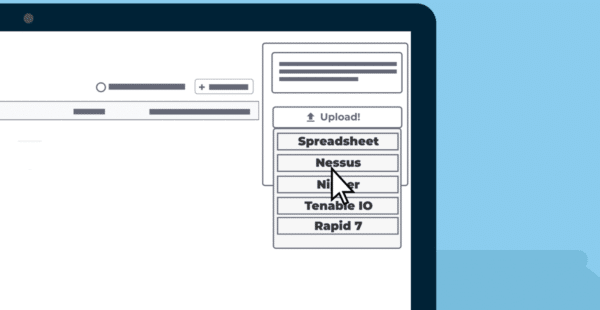
Our platform is vendor-agnostic, so you can use it to consolidate results from any scanner or vendor and manage your vulnerabilities in one place. This makes it seamless for you to continuously analyse, prioritize, and manage all issues across your estate.
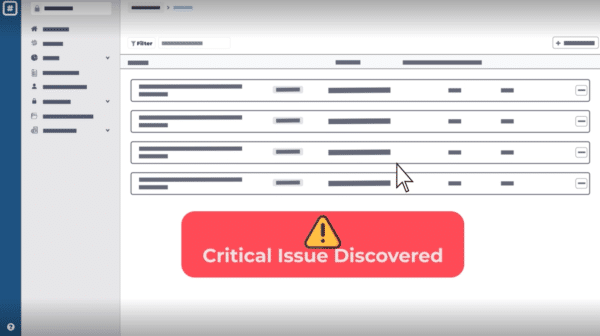
Close the Gaps Between Scans and Pen Tests
The time between vulnerability scans and penetration tests is the time when your organization could be at risk.
Our industry-leading Daily Exploit Detection alerts you to exploits for your issues on a daily basis, so you can close these gaps, monitor your threat landscape in real-time, and prioritize most effectively.
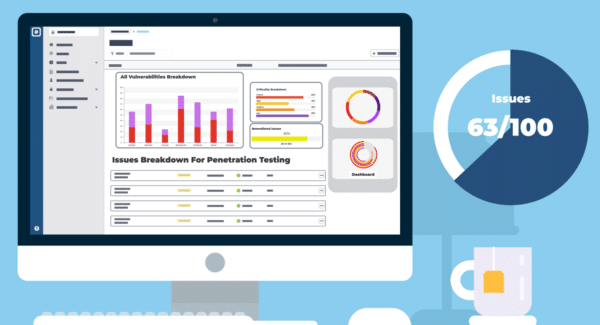
Automate Reporting and Analytics
The Rootshell Platform serves you important metrics from your vulnerability management programme. The platform’s insightful dashboards and automated reports help you continuously analyse your technical risk and measure compliance.
Up To Date Data
The Rootshell Platform ensures you are always referring to the most recent data from your vulnerability scans. The platform can compare scans on your behalf and mark resolved issues as remediated.
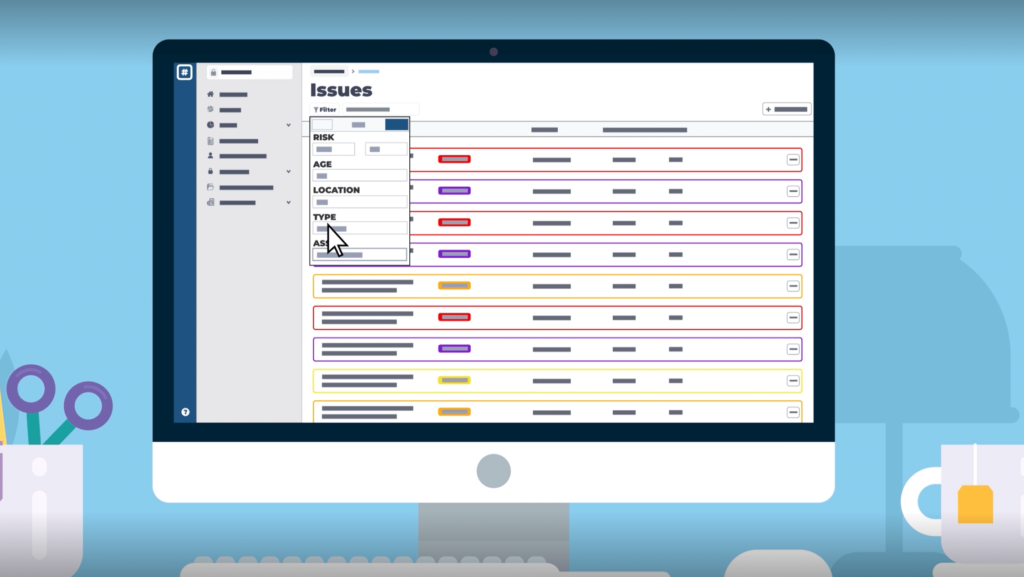
Track Critical Assets
Our platform makes manual asset management a thing of the past. You can assign priority ratings to your assets, making it easy to track and analyse those which are most critical to your organization on an ongoing basis.
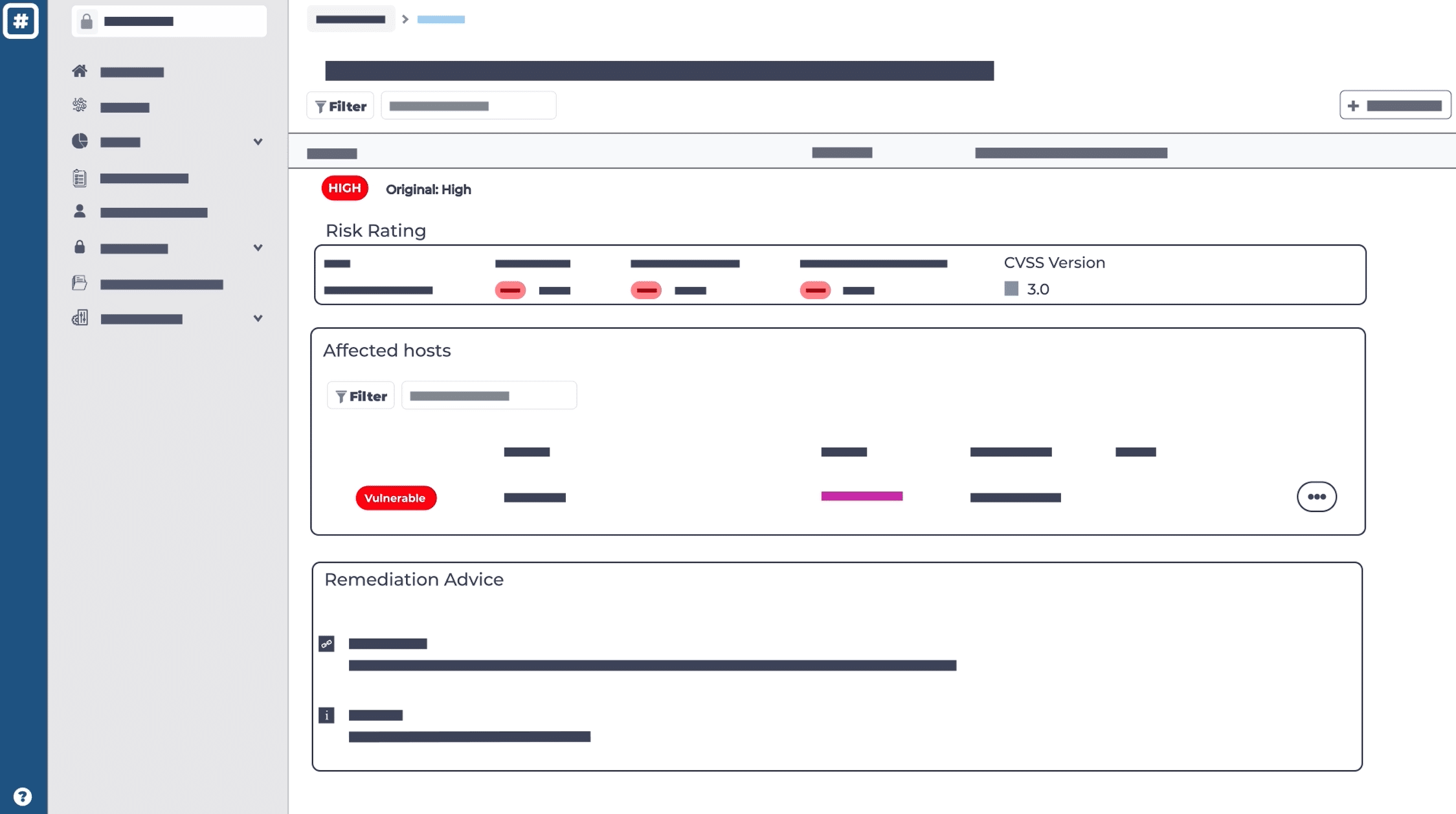
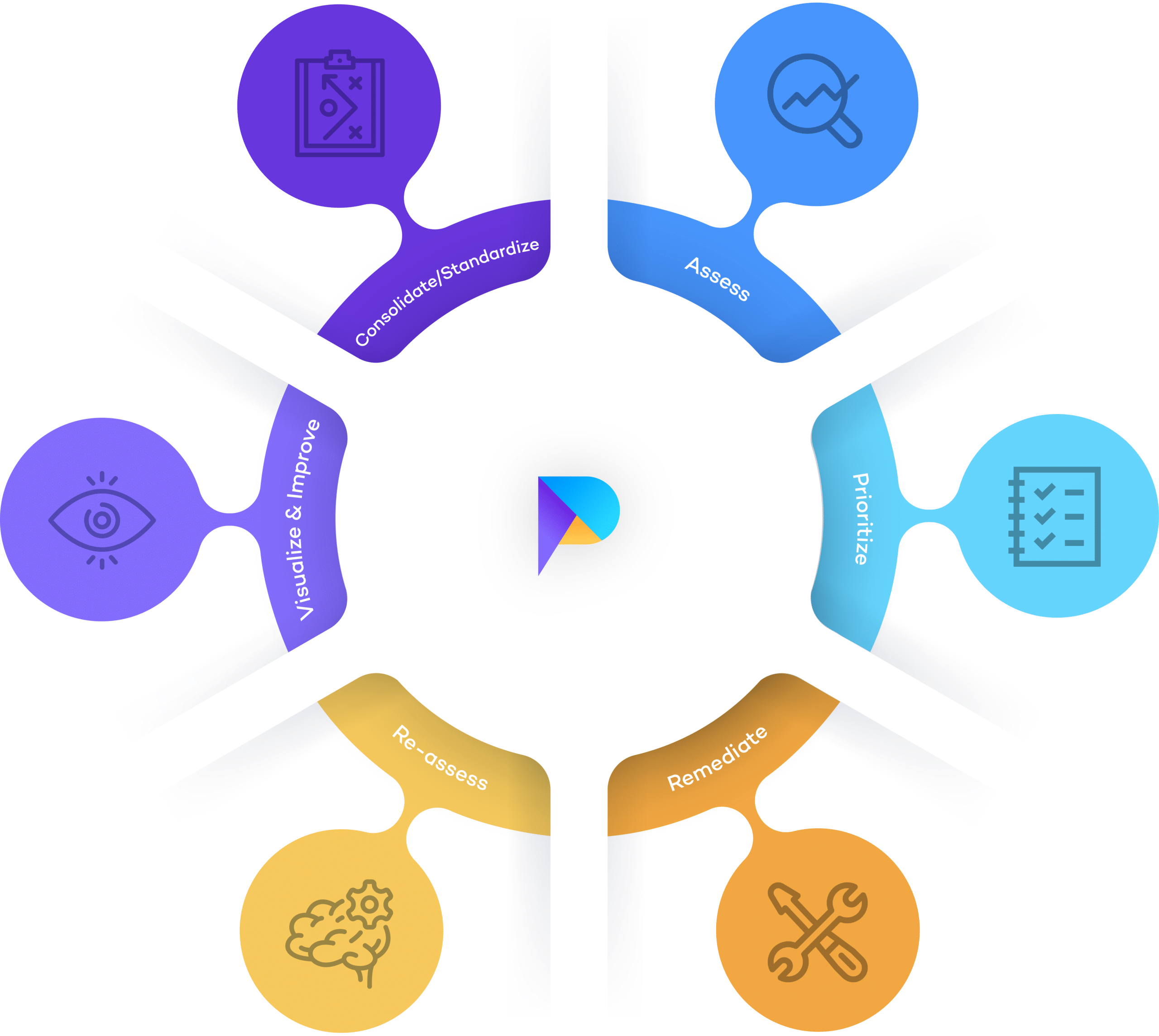
Best Practice Continuous Vulnerability Management
We have aligned The Rootshell Platform with the Gartner® Vulnerability Management Cycle, making it effortless for IT Security Teams to adopt best practice continuous vulnerability management processes.
- Consolidate your suppliers’ assessment data
- Integrate and standardize your assessment data
- Contextualize and prioritize your assessment data
- Streamline your remediation workflow
- Track and validate your remediation results
- Visualize and analyse technical risk across the whole organization