CMMC 2.0 requirements aim to strengthen cybersecurity for companies protecting national security information within the defence industrial base. Understanding the framework’s requirements is essential for government contractors and sub-contractors.
The Cybersecurity Maturity Model Certification (CMMC) model was a compliance framework designed for organizations dealing with Federal Contract Information (FCI) or Controlled Unclassified Information (CUI), aiming to fulfil stringent security requirements.
That model is now evolving into CMMC 2.0. The plan is to start the phased rollout in the third quarter of 2025 (but prime contractors will expect subcontractors to be compliant before that). This update necessitates a CMMC assessment for all involved, including defence contractors, to ensure they meet the updated security requirements.
Previously, contractors self-certified their cybersecurity posture under CMMC 1.0. Even though they had to follow NIST cybersecurity standards because of their contracts, they didn’t require an external party to verify their claims. However, CMMC 2.0 introduces third-party evaluations, significantly impacting DoD contractors by ensuring a higher standard of cybersecurity measures is met.
The CMMC framework changed this.
It introduced third-party evaluations to ensure a more robust defence against cyber threats and to offer transparency in compliance with DoD, ensuring that contractors meet CMMC standards. This significantly impacts contractors and subcontractors with defence contracts or those seeking business opportunities with the DoD.
How, exactly? Let’s take a look.
CMMC 2.0 Compliance Requirements
CMMC 2.0 simplifies the original model by reducing the number of maturity levels, making it easier for organizations of any size to understand and achieve CMMC compliance. This change is especially relevant for those aiming to reach or maintain CMMC level 2, which aligns with the protection of Controlled Unclassified Information (CUI), let’s break down the requirements:
Maturity Levels of CMMC
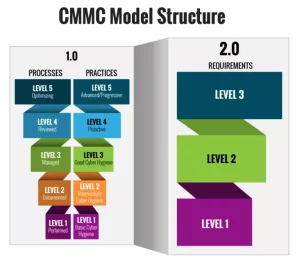
In the previous iteration, organizations had to navigate through five levels of cybersecurity requirements. CMMC 2.0, on the other hand, efficiently simplifies the process with only three maturity levels. This should provide a more straightforward pathway towards compliance, regardless of the organization’s size and requirements, especially for those needing to meet CMMC standards.
CMMC Certification Process
The certification process is now phased and will start in the latter half of 2025. It will consist of a series of rollouts designed to ease the transition for organizations. Contractors and subcontractors don’t need to rush as there is enough time to prepare, plan, and meet the CMMC 2.0 certification standards.
Cost Considerations
The costs of CMMC compliance should be factored into your strategy. The process includes assessment, implementation, licensing, migration, and scoping costs. Therefore, a thorough understanding of these components can prevent any unpleasant surprises down the line.
Compliance Steps
Achieving the required CMMC level necessitates a comprehensive approach to cybersecurity, aligned with the CMMC program’s guidelines. Meeting the CMMC 2.0 compliance requirements involves a strategic plan. You need to understand the applicable controls, implement the necessary safeguards, and prepare for the assessment. Remember, the focus should extend beyond achieving certification — the end game is to ensure sustainable and robust cybersecurity practices.
Levels of Cybersecurity in CMMC 2.0 Requirements
In consolidating the CMMC 2.0 framework, the previous five-level structure has been streamlined into three levels of cybersecurity. These are organized into 14 different cybersecurity domains, each with its guidelines and controls.
Here is a simplified breakdown of the three-level structure:
- Level 1 is the most basic cybersecurity level currently relying on 17 security controls derived from existing NIST SP 800-171 guidelines.
- Level 2 incorporates the total 110 security controls from NIST SP 800-171. This intermediate level is recommended for companies dealing with CUI.
- Level 3 adds additional controls from NIST SP 800-172. It’s aimed at businesses managing highly sensitive data or working directly on defense projects.
It’s important to remember that the levels are progressive. To achieve Level 3 certification, a business must demonstrate all practices (110 from NIST SP 800-171). It must also show the additional practices from NIST SP 800-172 that are required for Levels 1, 2, and 3.
This progression emphasizes the depth and rigor of cybersecurity capabilities, underpinning the comprehensive model that reinforces risk management practices.
Benefits of CMMC Compliance
Unlocking CMMC compliance comes with multiple benefits beyond just satisfying the federal government mandates. Let’s explore some key ones:
Enhanced Cybersecurity Measures
CMMC compliance ensures an organization has robust systems in place to detect, deter, and respond to cyber threats. Meeting the requirements for each level helps businesses become better at protecting sensitive defence-related data from data breaches and cyber-attacks.
Business Opportunities
Being CMMC compliant opens up new contract opportunities in the Department of Defense. Additionally, compliance will result in a competitive edge. It demonstrates an organization's commitment to safeguard sensitive data. That will likely give them an advantage over non-CMMC-certified competitors.
Supply Chain Resilience
With CMMC 2.0 certification required for all subcontractors, organizations can create a secure supply chain. That will strengthen the overall cybersecurity posture of the defense supply chain.
Long-term Viability
By adopting the CMMC framework, organizations can prepare for the future. It would help them lay the groundwork for a culture of continuous cybersecurity improvement. This contributes to an organization's reputation, credibility, and long-term viability, especially within the highly sensitive and regulated defense sector.
Given the many benefits, it’s not surprising that over 200,000 aerospace and defense suppliers are expected to seek compliance. You are advised to go for early adoption to keep pace with prime contractors’ expectations. It will help you pave the way for new opportunities while mitigating the impacts of assessment backlogs.
The Cost of Implementing CMMC 2.0
Implementing the CMMC 2.0 framework requires investing in financial resources and organizational effort at multiple levels. Government contractors and subcontractors need to understand these costs to plan strategically for CMMC level 2 compliance and avoid unexpected financial burdens.
Initial Assessment and Gap Analysis
The first step towards CMMC 2.0 compliance involves conducting a thorough assessment of the current cybersecurity posture against CMMC requirements. External consultants or tools may come with initial costs that vary based on your organization’s size and existing cybersecurity maturity.
Remediation and Implementation Costs
Once the gap analysis is complete, the next significant expenditure is remediation. You’d need to invest in technology upgrades, software solutions, and cybersecurity infrastructure improvements to meet specific CMMC 2.0 requirements. Costs can escalate quickly, especially if you need substantial upgrades to achieve compliance.
Training and Awareness
A crucial aspect of CMMC 2.0 compliance is ensuring that staff are well-versed in cybersecurity practices. You’d need ongoing training and awareness programs, which add to the overall cost. The investment in education ensures that your workforce is capable of maintaining the cybersecurity standards required by CMMC 2.0.
CMMC Program Certification and Continuous Monitoring
The costs extend to the certification process itself, including fees for third-party assessment organizations (C3PAOs) to conduct the official evaluation. Once you get the certification, you must invest in continuous monitoring and compliance efforts to remain within CMMC standards affording a sustained level of compliance. However, that may require additional resources for regular internal audits and compliance checks.
Opportunity Costs and Strategic Investments
Beyond direct costs, you must consider the opportunity costs associated with reallocating resources towards CMMC compliance. Strategic investments in basic cybersecurity practices can, however, yield long-term benefits. You’d have a reduced risk of cyber incidents, improved operational efficiency, and enhanced competitiveness in securing DoD contracts.
Financial Assistance and Reimbursement
The Department of Defense understands that CMMC 2.0 compliance can be costly for small and medium-sized businesses. As such, there may be programs or initiatives aimed at assisting such organizations with compliance costs. That would include potential reimbursements or grants.
Is CMMC 2.0 replacing NIST 800-171?
No, CMMC 2.0 enhances the existing requirements by integrating NIST 800-171 guidelines and adding new elements to ensure robust compliance with CMMC for all defense contractors.
By integrating these keywords directly and succinctly, your blog post is optimized to address the specific interests of your target audience, providing clear, concise, and relevant information on CMMC 2.0.
How do I become CMMC certified?
- Identify Required Level: Determine which CMMC level (1-3) applies to your organization.
- Conduct Self-Assessment: Review and align your cybersecurity practices with the targeted level’s requirements.
- Remediate Gaps: Address any deficiencies to meet the necessary standards.
- Select a C3PAO: Choose a certified assessor from the CMMC-AB Marketplace.
- Undergo Assessment: Complete the formal evaluation by the C3PAO.
- Achieve Certification: Receive your certification upon passing the assessment
Cybersecurity Compliance With Rootshell
Implementing CMMC 2.0 compliance is more than just a necessity. It’s a strategic advantage for government contractors, especially if you’re working with the Department of Defense.
If you adhere strictly to the certification levels and stringent requirements outlined by the CMMC 2.0 framework, you can unlock opportunities and enhance your competitive position in the defense supply chain. That’s on top of protecting sensitive information.
In essence, the CMMC 2.0 compliance journey is more than just a cybersecurity requirement — it’s a step towards securing the future of these organizations and the nation.
Find out how Rootshell can help you reach that level of security.



