Cybersecurity has to adapt to evolving threats. You need fresh approaches, certifications, and frameworks to constantly keep up with emerging technologies and attack vectors. One such framework was CMMC, which was introduced in 2020. As needs evolved, it’s now about to be replaced with CMMC 2.0. The phased rollout begins in the third quarter of 2025, indicating a significant preparatory period for contractors to comply with the necessary security requirements, including third-party assessments.
This new model has been designed to amplify the cyber readiness posture of organizations working with governmental entities and requires prime contractors to need to comply with CMMC 2.0.
But first, what is CMMC 2.0?

Overview of CMMC 2.0
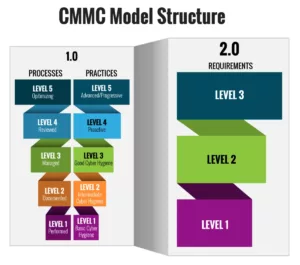
The term ‘DoD contractor’ becomes central when discussing access to sensitive information and the need for compliance with security controls and self-assessments outlined in the framework. “CMMC 2.0“ refers to the second iteration of the Cybersecurity Maturity Model Certification program. This program’s primary focus is on streamlining cybersecurity requirements into three distinct and well-defined levels. In essence, these levels are thoughtfully aligned with the established NIST cybersecurity standards.
Breakdown of the core aspects of the CMMC framework:
- It encompasses 14 cybersecurity domains.
- It consists of 110 practices, thoroughly detailed and structured.
- It is designed in a way that emphasizes the protection of sensitive information, particularly when shared with DoD (Department of Defense) contractors, ensuring that each contractor must adhere to the outlined security measures.
The underlying objective of the CMMC 2.0 framework is to ensure the security of Covered Defense Information (CDI) — encompassing Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
To draw a broad comparison, the CMMC 2.0 framework can be likened to internationally recognized standards like ISO 27001 and ISO 27002. While the former sets the guidelines for an information security management system, the latter provides practical guidance to implement the controls listed under the former.
At its core, however, CMMC 2.0 bears a close alignment with NIST SP 800-171 and introduces controls referenced in it as well. This strategic integration allows for a more comprehensive approach towards safeguarding specific types of unclassified information and implementing cybersecurity controls.
Bolstering this objective is a workbook that lays out these cybersecurity practices and CMMC assessment processes clearly for the Defense Industrial Base (DIB) sector’s contractors and subcontractors.
By following this workbook, these agencies can demonstrate their compliance with CMMC 2.0 requirements, streamlining their cybersecurity model in alignment with set guidelines, and reinforcing their cybersecurity framework competently.
Key Changes and Updates in CMMC 2.0
Several pivotal transformations have taken place in the second version of this cybersecurity model. The most notable being the condensing of maturity levels from the original five to now just three, significantly impacting DoD contractors by simplifying the compliance process. This restructuring is advantageous as it aligns the first two levels directly with the NIST SP 800-171 standard.
The third level also integrates NIST SP 800-172 controls, which notably were previously reserved for level 3 and higher in the initial CMMC model. Consequently, this streamlining of levels facilitates the continuous evolution of controls and requirements to align with emerging threats and challenges in the cybersecurity domain.
The other changes and updates are summarized below:
- Reprioritization of focus on the handling of FCI and CUI, highlighting the necessity to comply with CMMC at the appropriate level of CMMC compliance.
- Initiatives to revise and clarify the criteria for cyber incident reporting and how it impacts certification, reflecting an update in CMMC requirements and program requirements
- Potential adoption of other capabilities along with playbooks to augment security operations center capabilities, facilitate rule analytics, and mitigate cyber threats effectively. This points towards a broader scope of levels of cybersecurity within the CMMC 2.0 Program.
In providing these updates, CMMC 2.0 remains committed to ensuring that relevant entities incorporate appropriate risk management practices and adhere to the CMMC levels dictated by the DFARS clause concerning FCI and CUI data handling. The CMMC assessment process has been adjusted to reflect these changes, requiring entities to specify the required CMMC level for certification more clearly and align their cybersecurity practices with the updated CMMC 2.0 program requirements.
Implications for Government Contractors
To protect national security information, government contractors, including subcontractors working with the DoD and other federal entities, must now align with CMMC 2.0 levels. These levels comprehensively cover all three categories: FCI, CUI, and CDI. Therefore, demonstrating compliance with them requires operational adjustments in cybersecurity controls and risk management practices.
The certification level that a government contractor needs to achieve depends on the level of cyber risks associated with the information they handle. The three levels under CMMC 2.0 are as follows:
- Level 1: Basic Cyber Hygiene (focuses on safeguarding FCI)
- Level 2: Intermediate Cyber Hygiene (builds upon level 1 and focuses on protecting CUI)
- Level 3: Advanced Cyber Hygiene (further strengthens level 2 requirements and encompasses a portion of NIST SP 800-172 controls)
Remember, the certification process is quite meticulous. It involves:
- A comprehensive review of their current cybersecurity model capabilities
- Emphasis on the protection of sensitive data types such as FCI and CUI
- Ensuring seamless collaboration with government entities for sharing sensitive unclassified information
- Mandatory third-party assessments for higher levels, while allowing for self-assessments in lower levels.
Contractors have to reassess their current cybersecurity controls and infrastructure and make necessary modifications as required to align with the CMMC 2.0 requirements. Implementing analytics rules, safeguards for sensitive unclassified information, cyber incident reporting protocols, and other aligned practices are critical to achieving certification and maintaining compliance.
Achieve CMMC 2.0 Compliance With Rootshell
As we continue to grapple with evolving cybersecurity threats, frameworks like CMMC 2.0 play a vital role in fortifying the security infrastructure of government contractors and organizations that are part of the Defense Industrial Base (DIB). More than a compliance requirement, CMMC 2.0 serves as a strategic guideline for implementing secure practices to protect national security and sensitive data effectively.
Understanding the nuances of CMMC 2.0, its alignment with NIST standards, and the impacts on government contractors is essential to successfully navigate the complexities of cybersecurity. Fortunately, Rootshell is here to help you in your journey.
Rootshell Security can help you mitigate your cyber risks and comply with regulations.
How to Become CMMC Certified
To become CMMC certified, begin by identifying which of the three CMMC levels is required for your company, based on the types of Department of Defense (DoD) information you handle. This step is crucial as it helps to specify the required CMMC level. Following this, conduct a comprehensive gap analysis to compare your existing cybersecurity practices against the CMMC requirements for the identified level. Address any gaps found during this analysis by implementing the necessary cybersecurity measures. The next phase involves selecting an accredited CMMC Third Party Assessment Organization (C3PAO) from the list provided by the CMMC Accreditation Body. This organization will conduct the formal CMMC assessment process. Successfully passing this assessment will earn your company CMMC certification for the appropriate level, indicating that your cybersecurity practices are in full compliance with DoD requirements.
Does My Company Need to Be CMMC Certified?
If your company serves as a contractor or subcontractor to the U.S. Department of Defense (DoD) and manages Federal Contract Information (FCI) or Controlled Unclassified Information (CUI), then it is mandatory to obtain CMMC certification. This certification is a requirement set by the DoD to ensure that all contractors and subcontractors have implemented robust cybersecurity measures to protect sensitive defense-related information. By achieving CMMC certification, your company demonstrates that its cybersecurity practices are aligned with the stringent standards set forth by the DoD, thereby qualifying it to handle FCI and CUI as part of the DoD supply chain.
Subscribe So You Never Miss an Update