
A key component of modern cybersecurity strategies is attack surface management (ASM), a comprehensive approach that continuously identifies, classifies, and assesses vulnerabilities and potential attack vectors in an organisation’s digital environment.
In this article, we will delve into the concept of attack surface management and its critical role in safeguarding your digital assets. We will explore the various components of an attack surface, explain why ASM solution is essential, and highlight some of the best attack surface management tools available.
What is an Attack Surface?
Before diving into the specifics of ASM, it’s crucial to understand what constitutes an attack surface. Essentially, an attack surface encompasses all the entry points and potential vulnerabilities that threat actors could exploit to gain unauthorized access to an organisation’s digital assets. The attack surface is a dynamic entity that constantly evolves as an organisation’s digital footprint expands.
What Is The Attack Surface Made Up Of?
An organisation’s attack surface can be categorised into three primary components:
- Physical attack surface: The physical attack surface refers to the tangible assets and infrastructure that are vulnerable to physical attacks. This includes buildings, data centres, servers, and hardware devices. While the focus of ASM primarily revolves around digital aspects, overlooking physical security can have dire consequences.
- Social attack surface: The social attack surface pertains to the human element in cybersecurity. It includes employees, contractors, and other individuals who have access to an organisation’s systems and data. Malicious actors often exploit social engineering tactics to manipulate individuals into divulging sensitive information or performing actions that compromise security.
- Digital attack surface: The digital attack surface is the heart of ASM. It comprises all the internet-facing assets, web applications, cloud services, and network configurations that are potential targets for cyberattacks. This aspect of the attack surface is the most dynamic and extensive, making it a primary concern for security teams.
What Is Attack Surface Management (ASM)?
Attack Surface Management, or ASM, is a proactive cybersecurity practice that involves the continuous monitoring, assessment, and reduction of an organisation’s entire attack surface. ASM solutions are designed to provide real-time visibility into an organisation’s digital footprint, enabling security teams to identify potential vulnerabilities and attack vectors efficiently.
ASM solutions offer a range of functionalities, including:
- Asset Discovery: ASM tools help organisations discover and catalogue all digital assets, including those previously unknown, thereby minimizing blind spots.
- Vulnerability Management: ASM solutions assess potential vulnerabilities within an organisation’s digital infrastructure, allowing your team to prioritise remediation efforts effectively.
- Improve security posture: ASM solutions integrate with other security tools, automating tasks like patch management and remediation, streamlining your security workflow.
- Threat Intelligence Integration: Integrating threat intelligence feeds into ASM solutions enhances an organisation’s ability to stay informed about emerging threats and vulnerabilities.
- Continuous Monitoring: ASM tools provide real-time monitoring of the attack surface, enabling rapid response to any suspicious activities or security incidents.
Who Uses Attack Surface Management Software?
Attack Surface Management Software is an essential tool utilized by modern businesses to monitor and manage their expanding digital footprints. Predominantly, it’s leveraged by security operations teams within organisations that aim to identify and remediate security vulnerabilities promptly.
This software provides comprehensive exposure management by maintaining an up-to-date asset inventory, crucial in safeguarding against the increasing complexity of the modern attack surface. With a focus on application security, it helps in mitigating security risks associated with third-party integrations and the broader supply chain. By enabling companies to effectively manage and reduce their attack surfaces, it plays a pivotal role in preventing cyber attacks.
Effective attack surface management, thus, not only ensures robust protection against potential threats but also fortifies the overall resilience of an organisation’s security infrastructure.
Why Do You Need an Attack Surface Solution?
In today’s cyber landscape, the risks posed by an expansive digital attack surface are undeniable. Threat actors are constantly seeking new entry points and potential vulnerabilities to exploit, leading to a heightened risk of data breaches and other security incidents. This is where ASM solutions come into play.
Here’s why you need an ASM solution as part of your cybersecurity strategy:
- Visibility: ASM provides a comprehensive view of your organisation’s entire attack surface, including both known and unknown assets. This visibility is essential for effective risk management.
- Prioritisation: With ASM, security teams can prioritise security efforts by identifying and addressing the most critical vulnerabilities and attack vectors first.
- Rapid Response: Real-time monitoring capabilities enable organisations to detect and respond to threats quickly, reducing the time to mitigate security incidents.
- Compliance: ASM solutions help organisations meet regulatory compliance requirements by ensuring a proactive approach to security.
Top ASM Solutions
- io: Tenable.io is a renowned ASM solution known for its extensive vulnerability management capabilities. It offers continuous asset discovery, scanning, and real-time monitoring of an organisation’s digital attack surface. Tenable.io provides comprehensive reports and dashboards, making it easy for teams to identify and prioritise vulnerabilities effectively.
- Expanse: Expanse specialises in external attack surface management. It excels in mapping an organisation’s complete digital footprint, including internet-facing assets, domains, and subdomains. Expanse’s strength lies in its ability to provide visibility into the external attack surface and identify shadow IT assets, making it an excellent choice for organisations seeking to reduce their digital risk exposure.
- Qualys: Qualys offers a robust ASM solution that combines asset discovery, vulnerability assessment, and threat intelligence integration. It stands out for its scalability and the ability to assess vulnerabilities across on-premises, cloud, and mobile environments. Qualys provides detailed insights into an organisation’s attack surface, empowering security teams to proactively address vulnerabilities and secure their digital assets.
While these ASM solutions have their strengths, it’s essential to consider the unique features and benefits of Rootshell Security’s ASM service. We deliver all of these capabilities seamlessly through our cutting-edge Vulnerability Management platform, enriched with AI Active Exploit Intelligence. Our comprehensive approach, vigilant external asset discovery, continuous penetration testing, and advanced AI-driven threat insights make us a compelling choice for organisations seeking top-tier attack surface management solutions.
Important Features of Attack Surface Management Software
ASM Software, a crucial component in modern cybersecurity strategies, offers a suite of important features designed to enhance organisational security. Central to its capabilities is effective attack surface management, which involves continuous monitoring and management of digital assets to identify and remediate security vulnerabilities.
A comprehensive asset inventory feature ensures that all components of the modern attack surface, including on-premises and cloud-based assets, are accounted for and secured. In the realm of application security, this software aids in assessing and mitigating security risks, especially those stemming from third-party integrations and the supply chain.
Exposure management tools within the software enable businesses to proactively address potential security gaps, significantly reducing the likelihood of a cyber attack. Collectively, these features form the backbone of robust security operations, empowering organisations to safeguard their digital environments effectively.
How To Evaluate The Best Attack Surface Management Software
When evaluating the best Attack Surface Management Software, it is crucial to consider several key factors to ensure robust and effective attack surface management.
Firstly, assess the software’s ability to monitor and manage the full scope of your digital assets, ensuring it provides a detailed and dynamic asset inventory. This is vital for understanding the breadth of your modern attack surface and the potential security vulnerabilities within it.
Another important feature is exposure management, which should offer comprehensive insights into both internal and external threats.
The software should also excel in application security, providing tools to mitigate security risks from third-party integrations and supply chain vulnerabilities. Additionally, evaluate the software’s capacity to integrate seamlessly with your existing security operations, enhancing rather than complicating your security posture.
Lastly, consider the software’s user interface, support services, and scalability to ensure it can grow and adapt with your organisation, effectively protecting against cyber attacks in an ever-evolving digital landscape.
Rootshell’s ASM Service

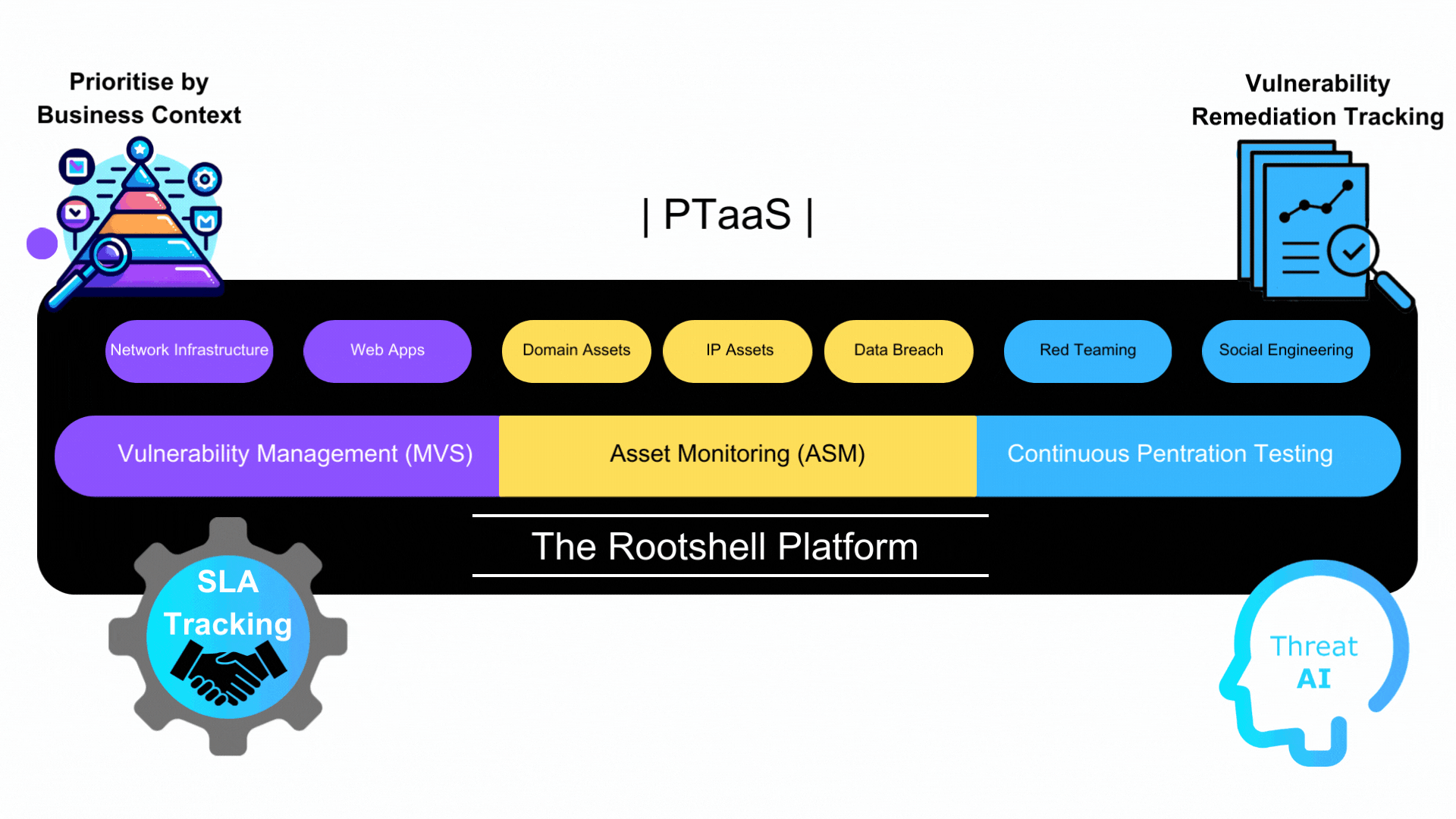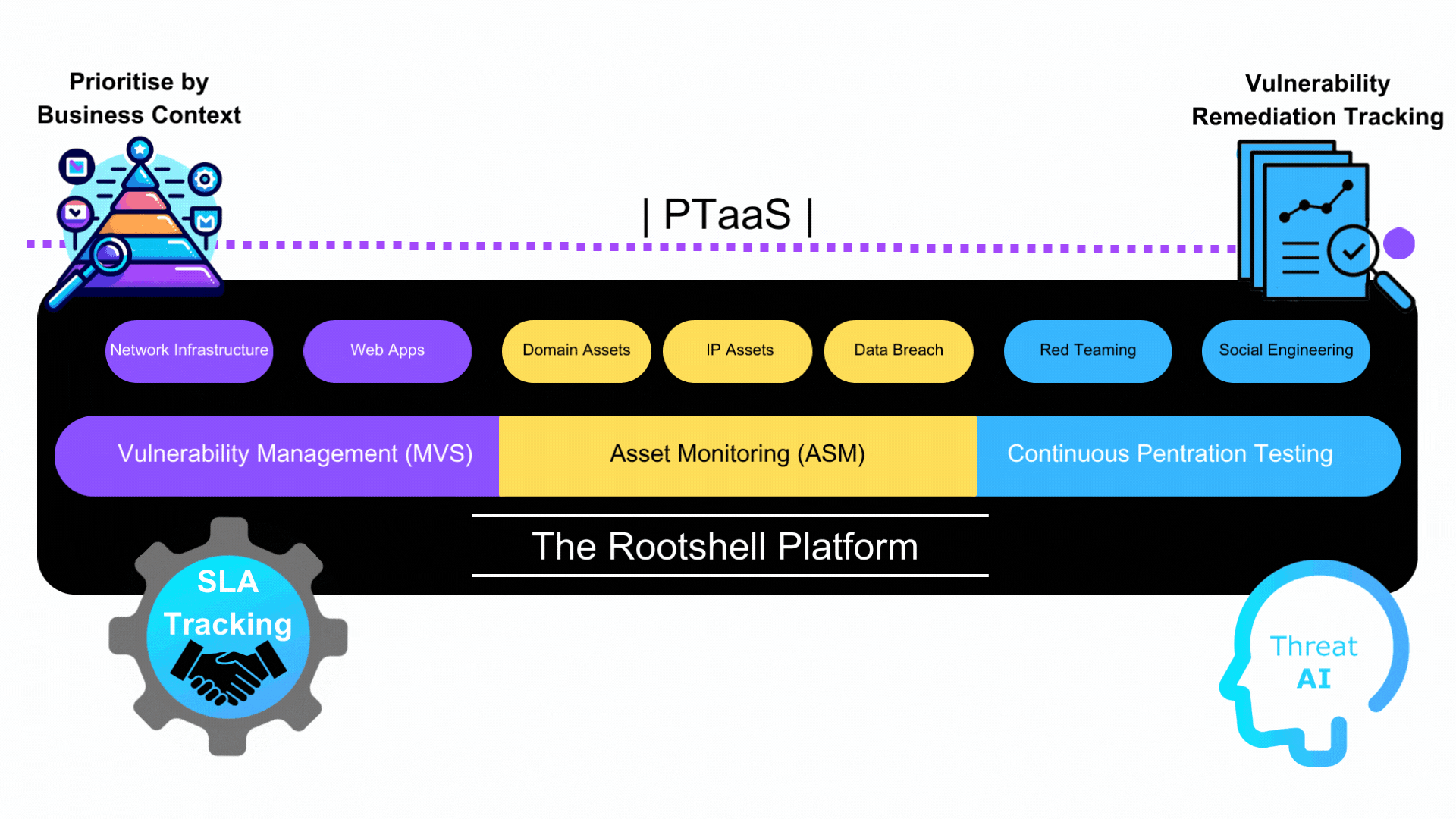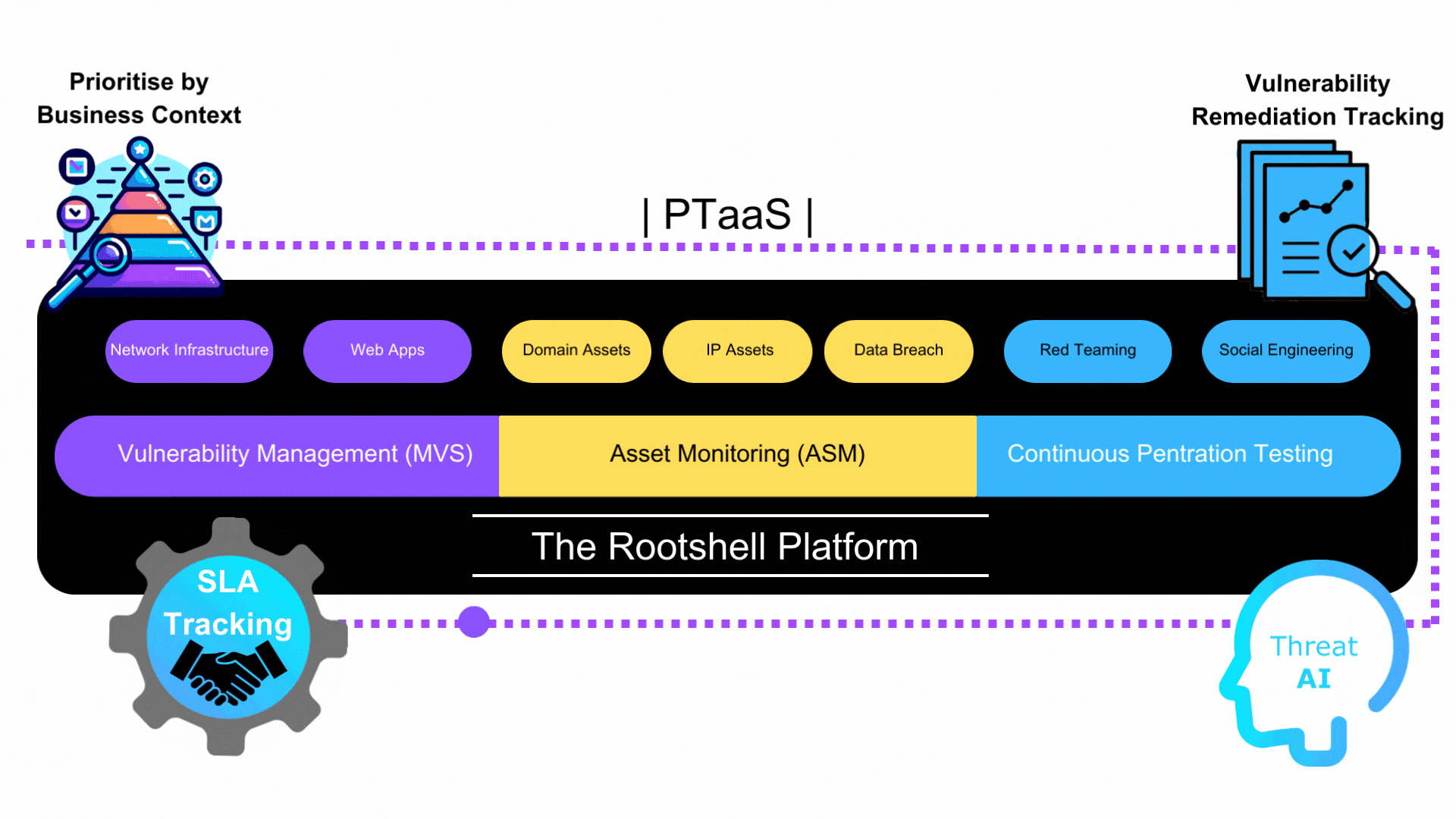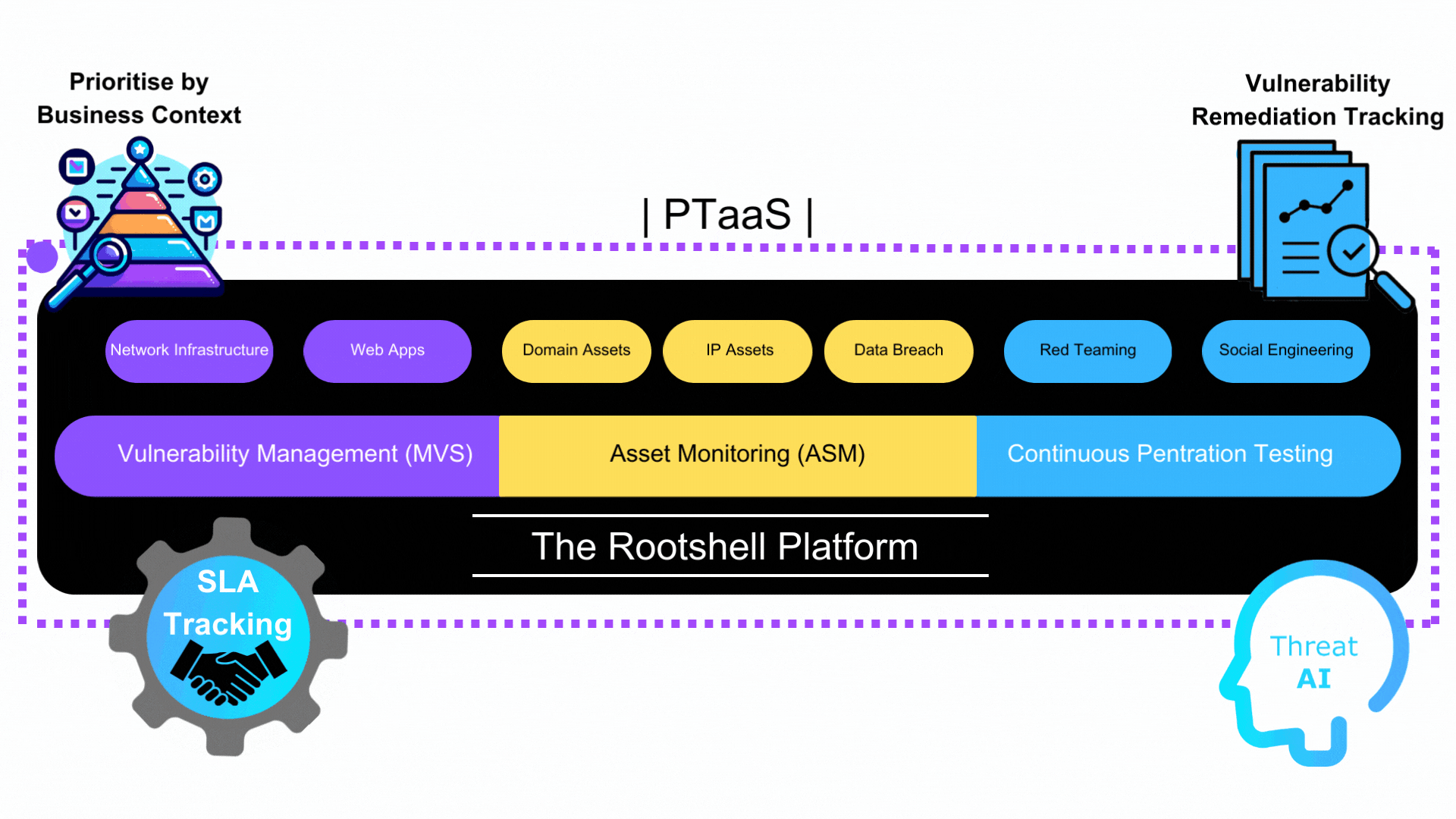
At Rootshell Security, we understand the evolving cyber risk faced by organisations today. Our Attack Surface Management (ASM) service, in conjunction with Continuous Penetration Testing, offers a robust approach to identifying and managing vulnerabilities. We take pride in providing comprehensive solutions that empower businesses to fortify their security posture effectively.
Vulnerability Management (VM) Excellence
Our ASM service includes a comprehensive Vulnerability Management process that ensures thorough assessment and mitigation of potential risks within an organisation’s attack surface. We leave no stone unturned when it comes to safeguarding your digital assets. Our team of experts is equipped with cutting-edge tools and methodologies to identify and prioritise vulnerabilities efficiently.
External Asset Discovery
One of the cornerstones of our ASM service is external Asset Discovery. We go beyond the surface, providing you with a detailed overview of potential risks within your organisation’s attack surface. Our Asset Discovery feature is particularly vigilant, monitoring for various elements that can pose threats:
- Typosquat Domain and Subdomain Alterations: We keep an eye on typosquatting attempts and alterations in domains and subdomains to prevent attackers from exploiting common typographical errors that users might make while typing URLs.
- Changes in Public IP Port/Protocol Configurations: Any unauthorized changes in public IP port and protocol configurations are detected promptly, helping you maintain control over your network infrastructure.
- Credential Leakage Detection: Our vigilant monitoring system identifies any signs of leakage, ensuring a proactive defence against evolving cyber threats. By monitoring for leaks, we help you mitigate the risk of unauthorized access and data breaches.
We understand that proactive defence is crucial in today’s cybersecurity landscape. Our Asset Discovery feature is designed to stay one step ahead of potential threats, allowing you to fortify your security posture effectively.
Continuous Penetration Testing
In addition to ASM, our Continuous Penetration Testing services provide ongoing testing of your organisation’s security measures. Our team of certified ethical hackers conducts regular penetration tests to simulate real-world attack scenarios and identify vulnerabilities that may not be apparent through traditional testing methods. This proactive approach allows you to stay ahead of potential threats and continuously enhance your security measures.
By combining Attack Surface Management, VM, External Asset Discovery, and Continuous Penetration Testing, Rootshell Security offers a comprehensive suite of services that empower organisations to proactively defend their attack surfaces against evolving cyber threats.
Conclusion
As organisations rely increasingly on digital assets and online presence, the attack surface expands correspondingly, providing threat actors with more potential entry points and vulnerabilities to exploit. To mitigate these risks effectively, organisations must embrace proactive cybersecurity practices, with Attack Surface Management (ASM) at the forefront.
ASM isn’t just another cybersecurity buzzword; it’s a strategic imperative. It involves continuous monitoring, assessment, and reduction of an organisation’s entire attack surface, encompassing physical, social, and digital components. It is the cornerstone of modern cybersecurity, offering a proactive defence against an ever-expanding threat landscape.
In this article, we’ve explored the concept of ASM, its significance, and the vital role it plays in safeguarding sensitive data and maintaining a robust security posture. We’ve highlighted the importance of identifying and managing vulnerabilities, attack vectors, and the constant need for visibility into an organisation’s attack surface. The benefits of ASM solutions, including real-time monitoring, VM, and integration with other security tools, have been underscored.
While we’ve discussed the importance of ASM in the broader context of cybersecurity, it’s equally crucial to recognise the contributions of Rootshell Security in this domain. Rootshell’s Attack Surface Management services go beyond the ordinary, offering a comprehensive suite of solutions tailored to meet the unique needs of today’s organisations.
Our ASM service, in conjunction with Continuous Penetration Testing, provides a robust approach to identifying and managing vulnerabilities. It includes a comprehensive VM process and external Asset Discovery, providing a detailed overview of potential risks within an organisation’s attack surface. What sets Rootshell apart is our Asset Discovery feature, which is particularly vigilant. It monitors for Typosquat domain and subdomain alterations, changes in public IP port/protocol configurations, and any signs of leakage. This ensures a proactive defence against evolving cyber threats, a crucial aspect of modern cybersecurity.
Furthermore, we deliver all of these capabilities seamlessly through our cutting-edge Vulnerability Management platform, enriched with AI Active Exploit Intelligence. This AI-driven technology empowers our clients with real-time threat insights and helps them stay one step ahead of potential threats.
In conclusion, Attack Surface Management is not merely an option; it’s a necessity in the digital age. Organisations must adopt ASM as a fundamental component of their cybersecurity strategy to effectively address the evolving cyber risks, protect sensitive data, and maintain a strong security posture. Rootshell Security stands ready to assist organisations in this critical endeavour, offering top-tier ASM services backed by cutting-edge technology, expert guidance, and a commitment to proactive cybersecurity.
It’s not a question of if, but when, your organisation will face cyber threats. Be prepared, take the proactive step, and partner with Rootshell Security to safeguard your digital assets from the ever-present threat landscape. Your cybersecurity future begins here.


