Welcome to the second post in my phishing series, in the first I briefly touched on some different types of phishing such as Spear-Phishing and Whaling which I’d recommend taking a look at if you haven’t already here: https://www.rootshellsecurity.net/phishing-inside-the-attackers-tacklebox/
In this second post, we’ll be looking at some simple tips and tricks that we think all users should know to set a basic foundation of awareness when it comes to phishing. Building on that, we’ll explore a few things that hackers are aware of and how we may use them against a target, before moving into common pitfalls we see even in the more mature organizations out there. Ultimately, bringing this post to a close with a short snippet of my take on the AI threat when it comes to social engineering.
Simple Tricks
Generic Phishing
So to jump right into it, I want to address the most common question I get when it comes to phishing from clients, friends, family and just about anyone else who has had the pleasure of listening to my phishing-centric rants:
“…but how do I know it’s a phishing email?”
The simple answer: a functional blend of awareness, curiosity, paranoia and software, and I include software last for good reason but we’ll get to that soon enough. Let’s talk awareness, curiosity and paranoia for now.
A few simple questions and a curious/paranoid mindset can foil many phishing attacks:
“Why is this person sending me this seemingly very important document to sign, yet I’ve never heard about it until now and why does it need to be done today?”
“Why is a company that spent nearly 50 years building the name Microsoft sending me an email from a domain called msoft.com?”
“Why does that URL link read https://rootshellsecurity.net/ but when I hover over it, it says www.rootshell-security.coom/?id=170497?”
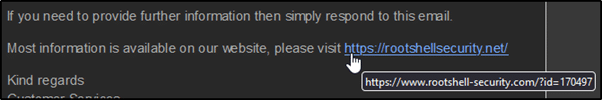
Let’s say you get an email telling you that your Office365 password has expired and you’re locked out of your account. Manually (not through a link) navigate to an official Microsoft owned site and log in, if you’re locked out then it will become very apparent and then you can action it.
If you consistently get emails from your manager, John Smith, then the emails from field will reflect this and not simply read as from: john.smith@msoft.com.
You likely have hundreds of legitimate emails in your inbox, play a bit of spot-the-difference with the suspicious email all the way down to a difference in font used:
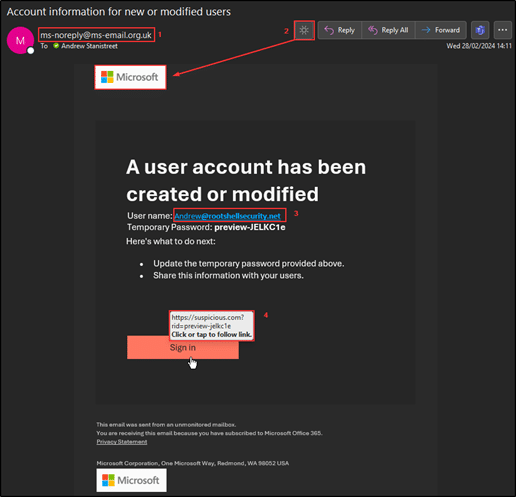
- No recognized ‘friendly name’ associated with sender (the real version of this template contains the from field: “From: Microsoft on behalf of your organization <ms-noreply@microsoft.com>”)
- Toggling dark mode highlights a static image for the MS logo compared to the real version:

3. The ‘unique username’ included in the target email address contains an inconsistency in the font/formatting of the text. The username isn’t in bold compared to the domain which may imply a tool has been used to find and replace the username depending on the target.
4. Again, investigating the link contained within the email reveals it would direct a target’s browser to a malicious page as opposed to a legitimate Microsoft site.
And if after all that something doesn’t feel right, you’ve done all your checks and now you’re not so sure, be paranoid and speak to someone responsible for figuring it out such as your Security Team, Manager, CISO… I know personally that I’d rather deal with a few paranoid reports of suspicious activity than deal with a breach because someone didn’t want to cause a fuss. Reward this diligence.
What We (Hackers) Know
So with all that said, let’s move on to what we as hackers know organizations, staff and software do to prevent these attacks.
Firstly we know when it comes to immature organizations that many users’ (especially new-starters) first instinct when facing a potential phishing attack is to either do what they’re told in the email or if they have an element of security awareness, forward the email to another member of staff to inspect at risk of spreading the infection.
With this small piece of information, we know that new starters who are yet to receive training are prime targets and that if we want to get an email in front of say an IT Team member this is often the path of least resistance. In our experience, even the simplest campaigns have a much higher chance of success when forwarded internally as opposed to us delivering them directly to a target in an IT Team for example.
In a somewhat similar vein of behavioural observations, many organizations in the UK at least are quite timid in their approach to introducing social engineering testing and as a result, we often see organizations up for phishing engagements but so long as we don’t target finance, HR, executives or a given part of the organization known to likely have poor security awareness for fear of opening a can of worms. Thanks to this common trend, these are exactly where I’d look to target an organization since in my experience, they are the least prioritised when it comes to social engineering training whilst being some of the most targeted areas of any given business when it comes to social engineering.
Moving into the more software-based area, many vendors are more than happy to flex their stuff when it comes to what they do to protect their clients and thanks to this we have a list of things to avoid when building a phishing campaign, for example:
- Domain Reputation Checking
Building domain reputation is a standard pre-launch element of our phishing engagements - Email Header Analysis
Even the more basic phishing toolkits provide the feature of being able to apply custom headers - In-Email Banners / Alerts
A simple Google search reveals plenty of examples showing the types of banners vendors add to emails to alert users to something dangerous – as such it’s easy to replicate these with our malicious links embedded - Keyword Analysis (Often ‘AI-Driven’)
Thanks to all our phishing engagements being manually built start-to-finish, it’s easy to lead a target towards what we want them to do/disclose without triggering keyword detection - URL Checking
Most software implementing these checks spend 0-3 seconds running their checks, so a 4-second delayed redirect from a legit website to our malicious one slips right past - URL Rewriting
Staff are trained to identify that if a link contained within an email has been rewritten to https://secure-email-sandbox.com it’s been analysed and secured. Knowing this, we can register https://secure-email-sandbox.co.uk and throw that at them
It is important though to note that whilst we can list these various methods we’ve successfully employed when running our phishing services, we are by no means suggesting these various solutions are not worthwhile and have proven to be a thorn in our side many times when trying to phish a target.
Pitfalls
With all of that out of the way, let’s look at common pitfalls when it comes to an organization’s approach to defending against a phishing threat.
In my opinion, the single biggest issue I’ve seen time and time again is an organization’s willingness to purchase defensive software and expect that to be their gates closed, often without any configuration. It goes without saying that buying security software without configuring it is like having locks on your house without ever actually locking them but the key issue is the assumption of safety.
This is especially true when this is taken to the next level of telling staff that a given software is so good that they don’t need to worry about the threat of phishing anymore so when an attacker bypasses their defences (and I use the word when intentionally) users often are so mislead in their sense of security that they would never think twice if an email was a bit strange.
Second to this issue comes office culture, far too many organizations operate in a way that has staff almost fearful of incorrectly reporting a phishing attack – sometimes the threat of being phished at risk of punishment can actually cause users to be more susceptible to being phished. It seems to be human nature that if someone, for example, is told enough times to be careful and not spill their drink they actually become more likely to due to their nerves and fear of doing wrong.
At Rootshell we firmly believe that positive reinforcement is the only appropriate approach and that no member of staff should be shamed or punished for falling victim to social engineering – it is often the best lesson they will ever receive when it comes to social engineering.
Security software is vital in any given defensive process but it’s important to remember that social engineering targets humans, not software. No software is perfect and when many of them fall back on an admin approving the release of an email to users, it’s still a human pressing the button, a human that can be influenced.
Finally, though not necessarily phishing in a sense, it’s important to remember that the digital attack vectors of social engineering don’t stop at phishing – just because an email says you will receive a text message and you do doesn’t mean it’s legitimate. SMiShing and Vishing, though independent methods of attack, can and are used in parallel to phishing.
The AI Threat
And on that note, we move to our final element of this piece. AI. The big topic on everybody’s lips. Many paint AI as the big bad of phishing. Capable of putting together comprehensive scripts in seconds tailored to any given scenario based on tone, language, industry, etc…
AI is a great support to social engineering but in my eyes, that is just what it is, support. Ultimately an AI isn’t a human brain capable of opinions, preferences or quirks. The very things that social engineering hinges on to be successful. The exact things that only the human mind can compute in such a unique way that enables humans to write an email in the precise way needed to have their target take action as directed.
AI definitely enhances the threat of social engineering as a whole, Rootshell is actively researching AI and its applications in various scenarios to this end. I’m personally working on voice-based generative AI and it’s potential use in vishing however when it comes to email-based phishing, it’s just as much a tool in my kit as the keyboard I’m using the write this article, yet I’m sure few people are afraid of keyboards.
Looking Forward
In the third and final post of this series, we’ll take a look at Rootshell’s approach to phishing as a service.
We’ll look at how we’ve helped our clients both, big and small, reach high levels of maturity in the social engineering arena with anywhere between 15 and 3000 users within the scope of their respective service.
Why we believe a regular phishing service isn’t just smart but necessary in the modern security landscape.
And to tie it all off, a testimony from one of our longest-standing and biggest phishing clients!



