Author: Andrew Stanistreet, Security Consultant Managed Services
Flavors of Phishing
In this first post of this blog series, I want to first set the scene when it comes to phishing including its various guises, it’s objectives, general targets, potential outcome and briefly where it sits in the cyber kill chain.
Generic Phishing
First and foremost, we have phishing at its most basic. A simple, quite generic email thrown at most, if not all, of an organisation’s workforce in the hopes that someone along the line at least gets curious. In my experience from both delivering these types of attacks and from research, this often takes the form of a well-known service such as DropBox, DocuSign or Jira to name a few, which in larger organisations are practically guaranteed to be used in some capacity. Additionally, their well-known branding is naturally trusted, even if the target user doesn’t use the service themselves.
Limited pre-attack information is needed in these cases due to how generic the campaign often is, a simple “please review this policy file on DocuSign” followed by a cloned landing page to harvest credentials rarely fails. Best of all, these types of campaigns are very easy to build and can be kept in an attackers back pocket and launched at their discretion.
While there is always the chance of getting lucky and a higher level member of staff falling for this type of attack, more often than not this line of phishing is used in the hopes of gaining a foothold inside an organisation by slipping through the cracks, thus giving an attacker a staging ground to further attack the organisation from within.
Personally, my most successful phishing engagement came in this form, with a generic email duping a new-starter at an organisation with a poor internal security posture. This ultimately allowed my team and I to gain access to every inbox in the organisation, repositories of C-Suite meeting notes, staff WhatsApp groups, internal practices, business strategies and in one instance, data which may well have spelt the end of the company. All thanks to a simple, generic email, which I could throw at any organisation with as little as 5 minutes preparation time, and that was on day 1 of a 5 day red-team campaign. And all it took was a simple email from a generic ‘internal helpdesk’ as seen below:
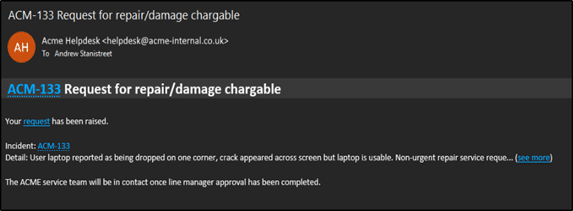
Just enough information to pique their interest and their interaction required to get the full story.
Spear-Phishing
Next on our list is Spear-Phishing, the scalpel in an attackers social engineering toolkit. This can be seen as the opposite of what we talked about above, here we trade generic for tailored-to-target themes and a phishing net for a hook.
What’s better than the assumption that a large organisation uses common services? Knowing what services they use and how they use them. To build on this, sometimes the biggest target isn’t the highest ranking person. In a well secured organisation, the CEO shouldn’t need access to certain elements of sensitive information or operations – so why target the C-Suite when a senior developer has access to their intellectual property in the form of the source code of a proprietary platform?
Let’s say we’re going to target an organisation which provides a proprietary platform to its clients. Chances are they will have some sort of support function which in most companies is pretty straight forward to get in touch with, paired with the fact that 9 times out of 10, they will provide some element of feedback to the user when a query is submitted. Often an automated email letting the client know their query has been received, we now know what ticketing system is in use internally.
Now we know what ticketing system they use, some basic open-source intelligence (OSINT) gathering on their staff is likely to reveal staff names, email addresses and job roles. We can use this to build a small list of developers senior and higher, those likely to have some elevated privileges. Now all we need is simple ticket email, branded as their known ticketing service provider to send and then sit back and wait for someone to click, sign into the cloned ticketing platform page and we now have access to the development team’s support board, internal patch-notes, product roadmaps etc – all because we chose our target specifically.
Whaling
So we’ve spoken about generic phishing and spear-phishing attacks targeted at different areas of a given organisation, now let’s talk whaling. Often the most professional branded campaign themes built upon high amounts of gathered intelligence given their target’s likely public presence.
Where generic phishing hits everybody and takes what it gets, or spear-phishing targets a given individual or individuals with a specific goal – whaling targets the big phish in the pond, hence the name. This is your C-Suite, your corporate directors, executive board or high-profile public figures.
As we alluded to in the section above, a well secured organisation should not have a C-Suite or executive team that has complete access to every piece of the business (see the principle of least privilege), it’s unnecessary. Yet while this isn’t always the case and some attackers may take advantage of this, in my experience whaling is often incentivised by one of two specific motivations.
Destructive – By attempting to gain access to a CEO’s account, an attacker is likely to obtain information they could use to cause large amounts of reputation damage and embarrassment to the target organisation.
Financial – By targeting the top of the tree, an attacker can attempt to trick the user into approving the release funds to an attacker-controlled account. Be it by simply manipulating their target directly or by using their access to the target’s systems to have another member of staff carry out the action for them, posed as the high-ranking individual within the organisation.
When all else fails, the more malicious attackers are not afraid to turn to simply blackmailing their target. This could be based on information they have exfiltrated or alternatively through the use of ransomware (though I won’t be delving into that topic in this series, more information can already be found here: https://www.rootshellsecurity.net/ransomware-assessment/).
Spray-and-Pray
Lastly we come to what is probably most people’s first exposure to phishing. This is where we see our classics:
“Click here to track that Amazon parcel you don’t remember ordering”
or
“You’ve inherited $33 million from a family member you’ve never heard of”
Often very simply campaigns targeting anyone and everyone they can find the email address of. The hope for the attackers being that one in a thousand users is gullible enough to believe a very generic, error filled email promising what is often too good to be true. These types of attacks are seen in the millions every day.
In my opinion, while the exposure of a password is without doubt a huge risk, I do personally believe the disclosure of a personal email address or phone number to be just as much of a risk. It takes a minute to change a password but it’s unlikely that most people would be willing to change their email address or phone number, even when they have clearly become included in attackers target lists somewhere along the line.
As an interesting home-project, take advantage of your email providers alias capabilities. Many allow users to create extra addresses such as name.1@outlook.com, name.2@outlook.com. Using this, sign up to various services with these different email addresses and see which of those addresses eventually receive these phishing attacks, you’ll soon learn your data is never truly safe in the hands of others which is why I personally believe ensuring your own awareness to these attacks and first securing yourself is of utmost importance!
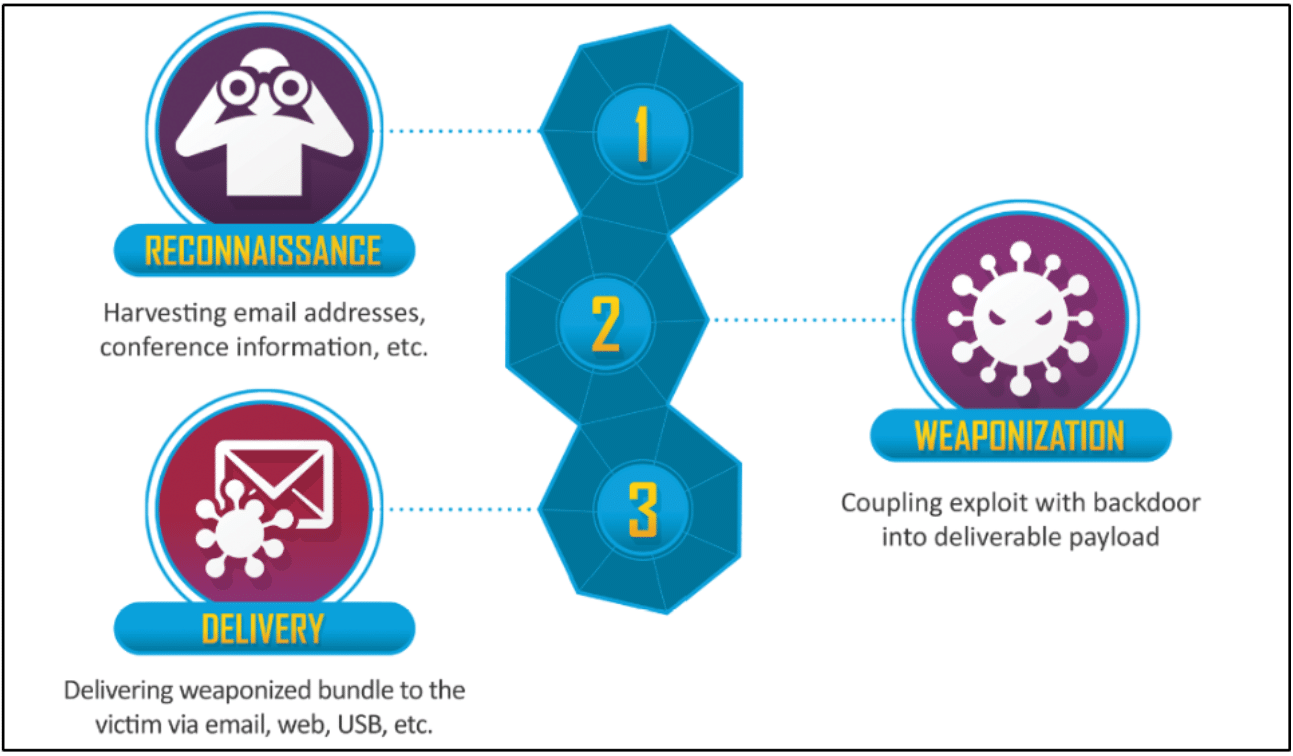
Phishing In The Attack Chain
Phishing sits at step 3, Delivery, within the Cyber Kill Chain following 1 Reconnaissance and 2 Weaponisation.
Most sophisticated attackers will first go through their reconnaissance phase of their attack, gathering information about their target such as harvesting target users information through open-source means such as public breach data lists, social media such as LinkedIn or simply the target’s corporate website. The more information they have, the more they can play on this to build their understanding of their target as well as leverage this information to build some trust in their target.
Next comes the weaponisation which in this instance would involve building their phishing campaign, setting up necessary infrastructure to deploy their attack, obtaining relevant domains required and even creating malicious payloads / exploit code which they may decide to deliver via an email attachment containing their payload or a simple link to a web-page containing a small piece of JavaScript which will hook their targets browser, giving the attacker remote control of browser functionality such as plugins, password autofill or simply the capability to trigger a authentication pop-up on their target’s screen.
Then we finally reach phase 3, delivery. The attacker chooses their time and date of attack, inputs their target’s details, hits the launch button and waits for their loot.
Looking Forward
In the next post of this series, we’ll look at how users can use some simple tricks to foil these attacks and bolster their confidence in protecting their organisation and colleagues by first protecting themselves through awareness.
We’ll explore a bit of what attackers are aware of when it comes to how organisations defend themselves against such attacks and why this information often can allow them to bypass those very defences.
Common pitfalls users fall into by not recognising this threat primarily targets humans, not software.
And lastly the topic on everybody’s mind, AI in cyber security – is it as big of a threat as it’s made out to be when it comes to phishing? I don’t believe so.
Subscribe So You Never Miss an Update