Vulnerability Management Solutions
Vulnerability Remediation Management Tools help IT security teams gain more insight from their data and streamline processes, resulting in faster and more effective remediation.

Join 1,000+ leading companies who trust Rootshell Security
What is Vulnerability Management?
Vulnerability management is the cyclical process of identifying, evaluating, prioritizing, and remediating security flaws within an organization’s network, systems, and applications.
Effective vulnerability management helps IT security teams make sure that vulnerabilities are discovered, analysed, and fixed as quickly and efficiently as possible. This helps to reduce the attack surface and prevents future cyberattacks, which could have devastating consequences on your organization’s data, personnel, and reputation.
The goal of vulnerability management is to make sure that organizations have complete visibility and control of weaknesses that exist within their IT estates on a continuous basis. Continuously monitoring and prioritising vulnerabilities based on their risk and level of threat means that security teams can focus their resources on addressing the most severe threats first.
Vulnerability management is not to be confused with a vulnerability assessment. Vulnerability management encompasses the end-to-end process of managing security issues, from discovery to remediation. On the other hand, a vulnerability assessment is a type of IT security test that discovers security issues within an organization’s network.
According to the Edgescan Vulnerability Statistics Report, In 2024, a record-breaking 40,009 Common Vulnerabilities and Exposures (CVEs) were published, marking a 38% increase from the 28,818 CVEs published in 2023. The growing volume of vulnerabilities reinforces the necessity of a strong vulnerability management program to quickly pinpoint and resolve security issues
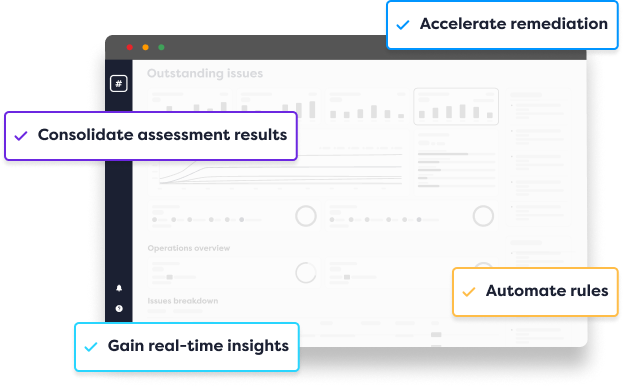
The Benefits of Vulnerability Remediation Management Tools
Vulnerability remediation management tools empower IT security teams to implement vulnerability management best practices by providing the following benefits.
Better Visibility
Vulnerability Remediation Management tools enable you to combine threat and vulnerability management by consolidating different types of assessments alongside each other. This helps you gain greater visibility of the threats you could be exposed to
Vendor-Agnostic Tools for Consolidated Results
The best Vulnerability Remediation Management tools don’t tie you to a specific vendor, allowing you to consolidate results from different suppliers.
Addresses Vulnerabilities in Real-Time
As soon as a vulnerability is discovered, time is of the essence. Vulnerability Remediation Management tools can facilitate the delivery of your assessment results in real-time, so you can address high-priority issues as soon as they are identified.
Offers Continuous Visibility
Between security assessments, your organization could be at risk. Vulnerability Remediation Management tools ensure you are gaining continuous insight into your threats and remediating on an ongoing basis.
Combines Threat Intelligence with Vulnerability Data
Vulnerability Remediation Management tools integrate threat intelligence with your vulnerability data. This helps teams gain greater context of their issues so they can prioritize most effectively and accurately evaluate risk.
Streamline’s Processes and Saves Time
Vulnerability Remediation Management tools cut out countless manual and time-consuming tasks from your processes, from data handling to project management, freeing up essential time for what’s most important.
Vulnerability Management Best Practices
Regularly Conduct Vulnerability Assessments
Frequent vulnerability assessments help identify new and existing security flaws across your network, systems, and applications.
Prioritise Vulnerabilities Based on Risk
Not all vulnerabilities carry the same threat level. Use a risk-based approach to prioritise issues, focusing on those that could cause the biggest impact if exploited.
Maintain an Up-to-Date Inventory
Keep an accurate and current inventory of all assets, including hardware, software, and cloud services. This allows security teams to track vulnerabilities effectively and make sure nothing is overlooked.
Implement Continuous Monitoring
Vulnerability management is an ongoing process. Continuous monitoring allows you to find and respond to new vulnerabilities in real time, reducing the window of opportunity for attackers.
Integrate with Remediation Workflows
Link vulnerability findings with remediation workflows, ticketing systems, and patch management processes. This makes sure that vulnerabilities are addressed and tracked until resolution.
Document and Report Progress
Maintain clear records of vulnerabilities, remediation actions, and security metrics. Regular reporting helps demonstrate compliance, measure program effectiveness, and guide future improvements.
Consolidate Data with the Rootshell Platform
The Rootshell Platform puts you at the centre of your IT security ecosystem. It consolidates results from any scanner or penetration testing provider, giving you a unified view of vulnerabilities across your organisation.
With real-time exploit detection, integrations with tools like JIRA and ServiceNow, and automated reporting dashboards, the platform simplifies workflows by eliminating manual processes.