Continuous Attack Surface Management (CASM)
In an era where digital threats are constantly evolving, managing your attack surface effectively is critical. A comprehensive CASM solution provides visibility over your full range of assets and helps you guard against emerging threats.

Join 1,000+ leading companies who trust Rootshell Security
What is Continuous Attack Surface Management (CASM)?
Continuous Attack Surface Management is an advanced cyber security strategy that focuses on the continuous monitoring and analysis of your organization’s digital footprint. This process involves monitoring traditional network and security elements alongside cloud services, internet-facing assets, and even your external attack surface.
Unlike traditional static approaches to managing your attack surface, CASM gives you real-time visibility into potential threat targets. This enables you to proactively remediate key vulnerabilities and optimize your incident response plans. As a result, you’ll be able to strengthen your security posture while reducing your overall security costs.
How Does Continuous Attack Surface Management Work?
CASM continuously discovers, assesses, and mitigates potential attack vectors and vulnerabilities across your entire attack surface. This includes your organization’s digital, physical, and human elements, as well as any third-party suppliers or vendors you work with. From asset discovery to risk management, CASM provides a comprehensive and highly automated approach to securing your organization.
What is an Attack Surface?
An attack surface encompasses all the possible points where an unauthorized user can try to enter or extract data from your environment. This includes any digital assets, systems, and networks that could be exploited by threat actors.
As your attack surface expands through the expansion of your digital capabilities, the potential points of entry increase – and so do the risks your organization faces. With 90% of organizations now engaged in digital transformation, the challenges of attack surface management continue to grow. Only a comprehensive and proactive approach to maintaining visibility will suffice – and that’s exactly what CASM offers.
Four Types of Attack Surfaces
Digital Attack Surface
The digital attack surface encompasses your full range of cyber assets, including software and web applications, cloud environments, network assets such as firewalls and routers, and data storage systems.
Human Attack Surface
Physical Attack Surface
The physical attack surface refers to any physical locations or hardware that attackers can use to breach your systems. This includes the full range of endpoint devices, from laptops and desktop computers to USB drives and on-prem servers or data centres.
Vendor Attack Surface
Your attack surface isn’t confined to assets directly controlled by your organization. If you work with third parties to provide software solutions or APIs, any vulnerabilities in their systems could expose your infrastructure, too.
Hear why the world’s top companies trust us for external penetrating testing

Boost your cybersecurity with Continuous Attack Surface Management
Benefits of CASM for Your Organization
Implementing CASM in your organization offers significant advantages for your cyber security, including:
- Real-time assessments and faster responses to cyber attacks.
- Enhanced security posture and attack surface reduction.
- Improved risk management and cyber risk identification.
- Increased ROI on your security investments.
- Better compliance with regulatory requirements and standards.
- Enhanced visibility into the modern attack surface, including unknown assets and sensitive data.
Differences Between CASM and Other Solutions
CASM vs. Managed Vulnerability Scanning (MVS)
Managed vulnerability scanning focuses on identifying and remediating vulnerabilities within a defined scope. These scans are usually periodic, taking place at monthly or quarterly intervals. CASM, by comparison, takes a more holistic, continuous approach. Unlike MVS, it aims to provide comprehensive, real-time visibility over all potential entry points into your systems.
CASM vs. Continuous Vulnerability Management
While both CASM and Continuous Vulnerability Management move beyond a punctual approach to security testing, CASM provides a broader scope. It includes not just vulnerabilities but all aspects of your attack surface, aiming to map a full range of potential attack vectors and ensure all your assets are identified and properly categorised.
Key Considerations for Choosing a CASM Solution
When selecting a CASM solution, there are several critical factors to consider to ensure it aligns with your organization’s security needs and objectives. Rootshell Security’s Platform solution exemplifies these key considerations:
- Continuous monitoring. The cornerstone of any effective CASM solution is its ability to provide round-the-clock surveillance of your attack surface. The Rootshell Platform offers real-time monitoring so that any changes or emerging threats can be promptly identified and addressed.
- Shadow IT discovery. With the proliferation of unauthorized and unmanaged software and devices, identifying shadow IT is crucial. The Rootshell Platform excels in uncovering these hidden elements of your attack surface, which are often overlooked yet pose significant security risks.
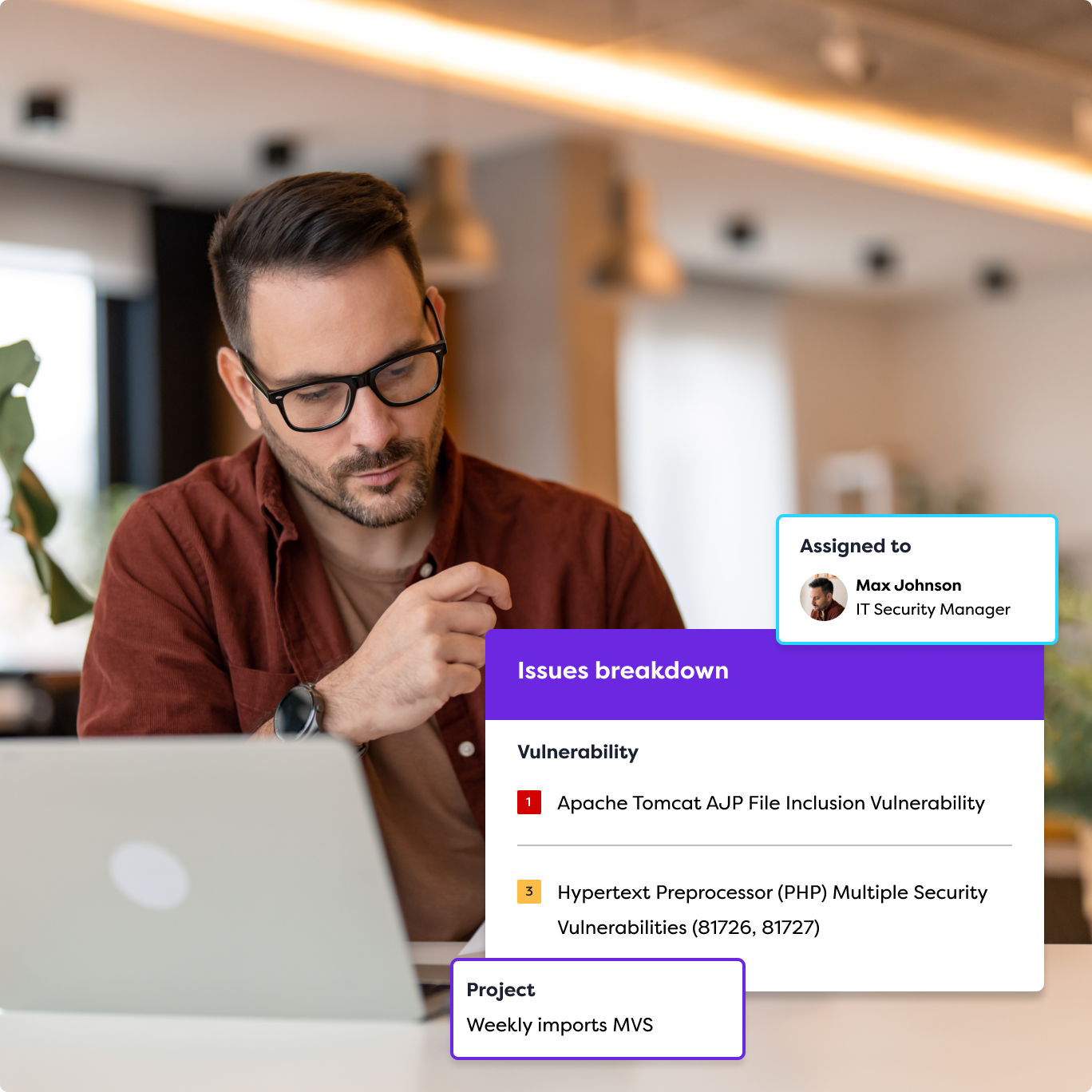
- Risk-based prioritization. The ability to prioritize vulnerabilities based on their potential impact is essential. The Rootshell Platform provides an intelligent risk assessment framework, enabling your security teams to focus their efforts on the most critical issues first.
- Integration with other security solutions. A CASM solution should not exist in isolation. The Rootshell Platform is designed to seamlessly integrate with your existing security infrastructure, enhancing your overall security posture without disrupting current operations.
- Black-box reconnaissance. An effective CASM solution should include advanced black-box reconnaissance capabilities to simulate how an external attacker would view your digital assets. Rootshell Security employs sophisticated techniques to provide this external perspective, offering invaluable insights into potential vulnerabilities.
- Comprehensive asset discovery and management. A thorough understanding of all your digital and physical assets is fundamental for effective attack surface management. Rootshell’s team excels in comprehensive asset discovery, ensuring that every known component of your attack surface is accounted for and secured.
- Scalability and adaptability. As your organization grows, so does your attack surface. The Rootshell Platform is scalable and adaptable, capable of evolving with your organization to continually provide robust protection.
- Regulatory compliance and reporting. With the growing importance of compliance in cybersecurity, choosing a CASM solution that aids in meeting regulatory requirements is vital. Rootshell’s services not only help in maintaining compliance but also provide detailed reporting for audit and review purposes.
- User-friendly interface and support. Ease of use and quality of support are essential for any security tool. The Rootshell Platform offers a user-friendly interface and dedicated support, making it simple for your security teams to utilize the system to its full potential.
- Proactive threat intelligence. Staying ahead of cyber threats requires proactive threat intelligence. Our Platform incorporates advanced AI-led threat intelligence capabilities, allowing your team to anticipate and prepare for potential threats before they impact your organization.
What Can Rootshell’s ASM Platform Do for You?
The Rootshell Platform offers a comprehensive solution to safeguard your digital assets against cyber threats. This robust framework integrates a full range of attack surface management solutions, ensuring you can stay ahead of potential risks.
Our approach combines the best of innovative technology with the irreplaceable insights of seasoned professionals to offer bespoke, effective cybersecurity solutions. To learn more about how we can help, book a tailored demo of the Rootshell Platform today.
