Vulnerability management is a critical part of any cybersecurity strategy. However, for larger organizations, the complexity of your systems and the sheer number of vulnerabilities can pose a significant challenge. Resource-intensive manual approaches won’t be up to the task – instead, you need an automated vulnerability management solution.
In this post, we’ll explain why automating your vulnerability management is an essential step to upgrading your cybersecurity efforts. We’ll take you step-by-step through how to implement it effectively and best practices you need to adopt.
What is Automated Vulnerability Management?
Automated vulnerability management continuously identifies, assesses and remediates potential security issues with minimal human input. As a result, it ensures that the identification and classification of vulnerabilities are not only consistent but also substantially quicker.
Automated vulnerability management incorporates the following key elements:
- Vulnerability Scanning: Automated vulnerability scanning tools work tirelessly, scanning web applications, and systems to detect potential weak points.
- Vulnerability Data Analysis: Post-scan, these vulnerability scanners aggregate data, ensuring security teams have actionable intelligence at their fingertips.
- Patch Management: Automation aids in identifying necessary patches, further expediting the vulnerability remediation process.
- Continuous Monitoring: The dynamic nature of today’s digital environment means new vulnerabilities can emerge overnight.
Why Automate Your Vulnerability Management?
With the growing complexity of today’s cybersecurity landscape, the role of automation in streamlining your vulnerability management efforts can’t be overemphasised. It can help you stay ahead of emerging threats and novel exploits even as your attack surface grows.
With vulnerability management automation, your security teams are freed from manual, repetitive tasks. This ensures that they can focus on strategic initiatives, enhancing the overall security posture of your organization. It also reduces the risk of human error commonly found in manual processes.
Further, vulnerability management tools can assess, prioritize and remediate vulnerabilities at pace. This helps you minimize the risk of a successful attack and contributes to meeting your vulnerability management SLAs.
Types of Automated Vulnerability Scanning
- Network Vulnerability Scanners: Aimed at identifying vulnerabilities within the organization’s network.
- Cloud Vulnerability Scanners: Aimed at identifying vulnerabilities within an organization’s cloud infrastructure.
- Web Application Scanners: Focus exclusively on web applications, identifying potential weak points that might be exploited.
- Database Scanners: Designed to find vulnerabilities within an organization’s database.
- Wireless Scanners: Focus on potential vulnerabilities within wireless networks.
How to Automate Your Vulnerability Management Processes
1. Evaluate Your Requirements
If you are looking to automate your vulnerability management program, there are a few things you need to consider before you begin:
- The size and complexity of your IT infrastructure. The more complex your IT infrastructure, the more difficult it will be to automate vulnerability management. This is because you will need to have a tool that can scan a wide range of assets and identify vulnerabilities in a variety of operating systems and applications.
- The maturity of your cybersecurity program. If your cybersecurity program is not mature, you may need to start with manual vulnerability management before you can automate the process. This is because you will need to have a good understanding of your vulnerabilities and how to prioritize them before you can automate the remediation process.
- The budget you have available. Tools can be expensive, so you need to make sure you have the budget to implement them. You also need to factor in the cost of training your staff on how to use the tool and the ongoing costs of maintaining it.
If you take these factors into account at the planning stage, you’ll be able to identify the appropriate scope for your automation project. As a result, you’ll be better placed to allocate the right resources to design and implement it effectively.
2. Choose the Right Tool
Once you have considered these factors, you can start to look for an automated vulnerability management tool. When choosing a tool, you need to consider the following factors:
- The features and functionality of the tool.
- The ease of use of the tool.
- The support offered by the vendor.
- The cost of the tool.
When evaluating these factors, you should refer back to the requirements you established in the first stage. For instance, your budget and the complexity of your infrastructure will determine which tool is the right fit for your needs.
3. Implement Effectively
Once you have chosen a tool, you need to implement it in your environment. This process will vary depending on the tool you choose, but it typically involves the following steps:
- Installing the tool on your network.
- Configuring the tool to scan your assets.
- Scheduling the tool to run scans on a regular basis.
- Reviewing the scan results and taking action to remediate vulnerabilities.
The implementation of a new tool is not always straightforward, so we’ve outlined some best practices to help you below.
5 Best Practices for Automated Vulnerability Management
- Implement risk-based vulnerability management. Prioritizing vulnerabilities based on their potential impact will help you focus on the most significant issues and avoid dedicating resources to fixing vulnerabilities that don’t pose a real-world threat to your organization.
- Integrate with your existing tools. Ensure your vulnerability management system seamlessly integrates with other tools in your security stack. This will limit the amount of manual intervention needed and ensure your vulnerability management process meshes with your other cybersecurity efforts.
- Regularly update scanners. Your vulnerability scanning tools need to be kept up-to-date in order to detect the latest vulnerabilities. Ideally, you should incorporate data from your threat intelligence feeds to stay ahead of emerging threats.
- Set up alerts and notifications. Your automated vulnerability management system should notify you of new vulnerabilities as soon as they are discovered. This will help you to take action to remediate them quickly and prevent them from being exploited by attackers.
- Review and refine. Vulnerability management is an ongoing process. You’ll need to regularly review your approach to ensure it aligns with the changing cybersecurity landscape and incorporates new technologies such as AI and machine learning.
- Implement risk-based vulnerability management. Prioritizing vulnerabilities based on their potential impact will help you focus on the most significant issues and avoid dedicating resources to fixing vulnerabilities that don’t pose a real-world threat to your organization.
Challenges of Automating Vulnerability Management
While the benefits of automated vulnerability management are extensive, they don’t come without challenges. You’ll need to consider the following:
- Upfront investment. Automating your processes will require an initial investment of time and money as you adapt your systems and secure the necessary tools.
- Training your teams. While automated vulnerability management requires less manual input, your teams will still need to learn how to manage the process effectively. You may need to provide formal training and increased oversight to avoid security lapses while they adapt.
- Managing false positives. Automated processes are more likely to identify apparent vulnerabilities that do not actually pose a threat. You will need to put verification processes in place to avoid spending resources fixing non-existent issues.
- Limiting downtime. Without proper scheduling, automated scanning can impact your systems, causing slowdowns that can impede service delivery.
These challenges can limit the effectiveness of your automated vulnerability management efforts, leading to unforeseen disruption or unexpected costs. However, with proper preparation and the right vulnerability management solution, these can be mitigated.
Automated Vulnerability Management with Rootshell Security
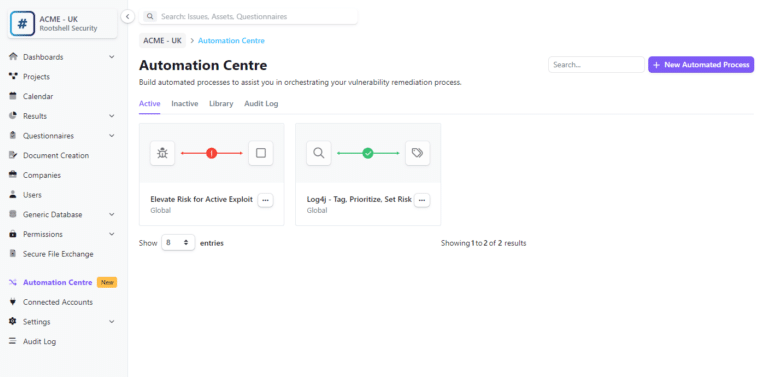
The Rootshell Platform is a vendor-agnostic vulnerability management solution. It enables you to manage results from vulnerability scans and other security assessments, such as penetration tests, in one central place. The automation center includes powerful triggers used to build rule sets that will allow you to effortlessly prioritize and manage your vulnerabilities.
Never Miss a Priority Vulnerability Again
Rootshell’s Automation Centre drives down the time it takes for organizations to receive, triage, and remediate results even further.
Users can create their own rules for how an issue should be delegated once it has been discovered. Vulnerabilities can be assigned to the appropriate colleague or team as soon as they are reported in the platform, with no manual effort required.
Rules can be set for vulnerabilities based on their priority status, such as issues affecting mission-critical assets that are being actively exploited. This will ensure the most critical issues will always be prioritized and assigned as soon as possible.
Save Valuable Time by Automating Triage
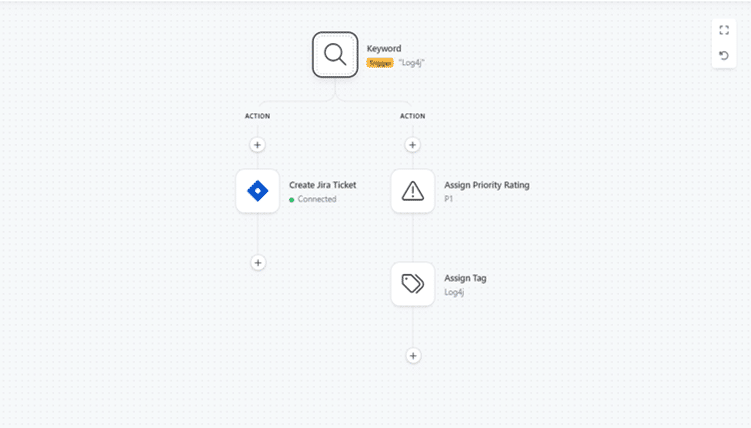
After managing the most critical issues discovered by a test, sorting through the hundreds of ‘high’, ‘medium’, and ‘low’ vulnerabilities can be arduous and time-consuming. To avoid this, users can set up automations that enable the platform to sort through the noise on their behalf.
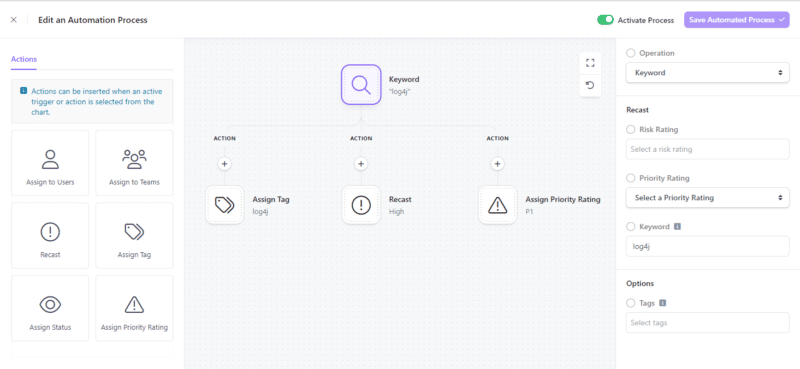
Rules can be created to reflect how teams would usually evaluate the new issues found in their estates. For example, an automation could add a customizable tag that says ‘to be triaged’ to any medium issue found on a priority asset containing ‘log4j’ in its name.
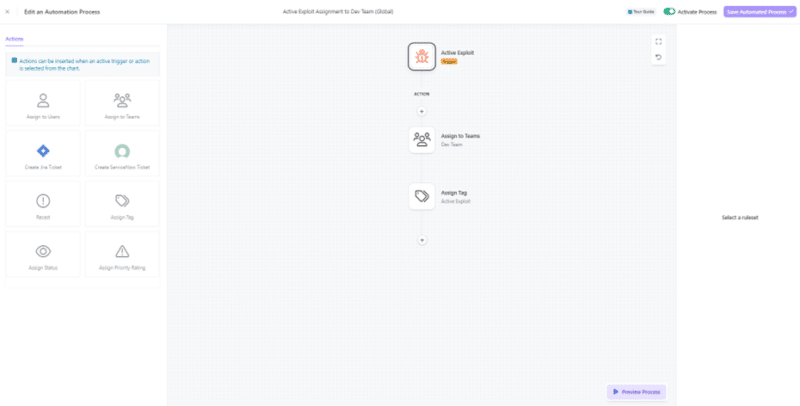
Automate Based on Business Context
CVSS scores only tell part of the story of an issue’s severity. Without contextualizing vulnerabilities in line with an organization’s unique situation, teams can find themselves overloaded with issues to remediate with no sense of what to prioritize.
Rootshell’s Automation Centre enables teams to create automations that contextualize their issues, filtering their vulnerability data and aiding prioritization.
Users can create automation rules for specific internal projects, adjusting the severity score of vulnerabilities up or down, assigning users and adding tags for easy tracking throughout the Rootshell Platform.
Adjusting risk ratings based on business context helps teams identify and focus on the issues that are the highest risk to them.
Easily Automate Repetitive Tasks
Rootshell allows users to easily automate a range of vulnerability management activities, reducing time-consuming repetitive tasks and ensuring important issues are never missed.
Create service desk tickets automatically and assign them to users or teams. Vulnerability severity scores can be adjusted to reflect new information or changing business context. Tags can be assigned to better organize your data.
Your team will be able to recoup significant time to reinvest in mission-critical tasks.
Explore the Rootshell Platform
Don’t let vulnerabilities dictate your organization’s security narrative. With Rootshell Security’s vulnerability management solutions, you can take charge of your cybersecurity efforts. Get in touch today to arrange a fully personalized guided demo with one of our experts.



