Protecting your computer systems and the data they store is extremely important. Sectors such as e-commerce, healthcare, and government are frequent targets for criminals looking to steal sensitive information and disrupt operations.
One way to protect IT systems and sensitive data from cyber threats is through penetration testing, also known as “pen testing.” This approach identifies security weaknesses before attackers can exploit them.
In the following article, we’ll take a closer look at what penetration testing involves, explore the different types available, and help determine which approach is best suited for your business.

What Is Penetration Testing?
Penetration testing is a type of cybersecurity assessment designed to find and fix weaknesses within an organisation’s networks. It uses the same tactics, techniques, and procedures (TTPs) as hackers to mimic a real-world cyberattack, allowing businesses to assess whether their existing security measures can withstand threats. The amount of prior knowledge the tester has about the target environment depends on the objectives of the test. These determine whether the assessment is classed as black box, white box, or grey box testing.
Types of Penetration Testing
Several types of penetration testing exist, each helping address specific needs. Here’s a look at a few different penetration testing methods you can use:
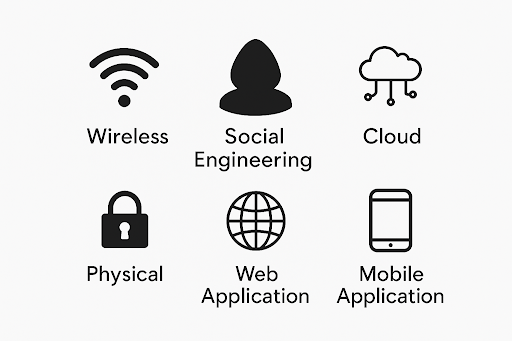
External Testing
External Testing iImitates attacks from outside the organisation, targeting public-facing assets. The goal is to find weaknesses in websites, email servers, and domain name servers (DNS). These tests mimic the behaviour of hackers who have no internal access and are attempting to breach remotely.
Internal Testing
Internal Testing mimics an insider threat or an attacker who has already gained access to the network. This approach assesses how much damage an attacker could do once inside the network, such as accessing sensitive data, escalating privileges, or moving across systems. It’s particularly useful for evaluating internal controls, employee access levels, and how well an organisation could detect and respond to an internal breach.
Web Application Testing
Web Application Testing targets vulnerabilities within web applications. These tests target vulnerabilities such as SQL injection, cross-site scripting (XSS), broken authentication, and insecure APIs. Given how important web apps are for user interaction and business operations, this type of testing protects customer data, maintains uptime, and ensures compliance with data protection regulations.
Wireless Network Testing
Wireless Network Testing assesses the security of Wi-Fi networks, identifying issues like weak encryption, rogue access points, and insecure configurations. This type of testing helps make sure that attackers cannot exploit wireless connectivity to infiltrate the network, intercept sensitive data, or disrupt operations. It also evaluates the effectiveness of network segmentation, access controls, and the strength of authentication mechanisms used on wireless networks.
Social Engineering
Social Engineering tests human defences by imitating phishing attacks, phone scams (vishing), or physical intrusion attempts. These may include phishing emails that trick employees into revealing credentials, phone scams (vishing) where attackers pose as legitimate personnel, or physical intrusion attempts aimed at bypassing access controls. The goal is to identify how susceptible staff are to manipulation and to strengthen security awareness across the organisation.
Physical Security Testing
Physical Security Testing looks at the effectiveness of physical security controls, such as building access restrictions, surveillance, and server room protections. This type of testing also helps review the effectiveness of security guards, keycard systems, visitor protocols, and physical barriers in place. Weaknesses in physical security can result in data theft, system tampering, or hardware sabotage.
Cloud Security Testing
Cloud Security Testing examines cloud-based infrastructure and services for weaknesses and data exposure risks. This type of testing makes sure that cloud environments are properly secured, compliant with best practices, and do not inadvertently expose sensitive data or services to the public.
Mobile Application Testing
Mobile Application Testing reviews mobile apps for vulnerabilities in code, data storage, and communication channels. The focus here is on identifying improper data handling, weak authentication, vulnerable third-party libraries, and unencrypted communications. This type of testing helps prevent data leaks and app exploitation.
Penetration tests are typically a little more intrusive than standard vulnerability scans and can lead to service disruptions. You may choose to schedule these tests in advance and notify staff beforehand to minimise operational impact. However, if the objective is to evaluate how effectively the internal security team detects and responds to an active threat, prior notice would compromise the results.
For instance, red team exercises are often conducted without alerting employees to replicate real-world attack scenarios and assess response capabilities under realistic conditions.
How Often Should Pen Testing be Conducted?
Penetration testing should be conducted at least once a year, but it just depends on the nature of your organization, industry regulations, and the complexity of your IT environment. Businesses handling sensitive data or operating in high-risk sectors, such as finance or healthcare, may require more frequent testing to stay compliant and reduce risk. It’s also important to perform a penetration test after any major changes to your systems, such as software updates, infrastructure upgrades, or migrations, as these can introduce new vulnerabilities.
Why Are Penetration Tests Performed?
Penetration tests are performed to identify and fix security vulnerabilities before attackers can exploit them. They simulate real-world cyberattacks on your systems, networks, or applications to uncover weaknesses in a controlled environment.
Penetration testing (or pen testing) is a simulated cyberattack used to improve the security of systems, networks, and applications. But why is it so widely used by organisations across industries? Below are the main reasons businesses invest in regular penetration testing.
1. Find Security Gaps Before Attackers Do
One of the main reasons penetration tests are performed is to proactively find vulnerabilities before malicious actors do. These vulnerabilities might include unpatched software, insecure configurations, weak passwords, exposed ports, or logic flaws in applications.
Instead of waiting for a breach to happen, a pen test mimics real-world attack techniques to uncover risks in a safe and controlled way. This allows your security team to patch holes before they’re exploited.
According to IBM’s 2024 Cost of a Data Breach Report, organisations that detect and contain breaches in under 200 days suffer an average of $4.88 million in costs, compared to $5.46 million when the lifecycle exceeds 200 days.
2. Validate the Effectiveness of Security Controls
Firewalls, antivirus software, endpoint protection, and multi-factor authentication are all important tools in your defence stack, but how do you know if they work under pressure?
Penetration testing evaluates whether these existing controls are properly configured and functioning. For example, a test might reveal that your firewall allows traffic on a risky port or that MFA can be bypassed due to poor implementation.
This kind of validation helps ensure that your security investments are providing real-world protection, not just compliance checkboxes.
3. Meet Compliance & Regulatory Requirements
Many industry regulations mandate or strongly recommend regular penetration testing as part of broader cybersecurity standards. These include:
- PCI DSS requires regular testing for businesses that handle cardholder data.
- HIPAA mandates risk assessments, including technical vulnerabilities, in healthcare.
- ISO/IEC 27001 encourages testing as part of information security risk management.
- GDPR encourages technical measures to protect data, which often includes testing.
- DORA requires financial entities to conduct regular threat-led penetration testing
- CMMC includes requirements for vulnerability management and security testing to protect controlled unclassified information.
Failing to meet these standards could lead to costly fines, reputational damage, or even lawsuits.
4. Reduce Business Risk
Cybersecurity isn’t just an IT concern; it’s a business risk issue. Data breaches, ransomware, and downtime can cost companies millions in revenue, legal costs, and reputational damage.
Identifying and fixing security flaws through pen testing means that businesses can reduce their exposure to threats. Penetration testing is often part of a broader risk management strategy that includes regular vulnerability management, security awareness training, and incident response planning.
5. Improve Incident Response Preparedness
A penetration test doesn’t just evaluate technical defences, it also tests how your organisation responds to a potential breach. Can your security team detect suspicious activity? How quickly can they respond? Do escalation and communication protocols work?
The insights from a pen test can help you improve your detection and response processes. Many businesses use the findings to conduct “tabletop exercises” or red team exercises to refine their incident response plans.
White Box vs Black Box vs Grey Box Pen Testing
Penetration testing can be carried out using different approaches depending on how much information is provided to the tester. The three main types are white box, black box. The table below compares these testing methods to help you understand their differences and determine which is most suitable for your needs.
| Aspect | White Box Testing | Grey Box Testing | Black Box Testing |
| Tester Knowledge | Full knowledge of systems, architecture, and source code | Partial knowledge (e.g. user credentials, system overview) | No prior knowledge of internal systems |
| Perspective Simulated | Insider (e.g. developer or system admin) | Semi-insider (e.g. trusted user with limited access) | External attacker with no internal access |
| Depth of Testing | Deep testing of all layers | Moderate depth; focuses on known components and areas | Surface-level, focused on discovering entry points |
| Testing Efficiency | High with full access, vulnerabilities are easier to find | Balanced, targeted testing based on available info | Low, more time needed to discover and exploit issues |
| Use Cases | Code audits, compliance testing, and secure development reviews | User-role testing, web app tests, internal network checks | Perimeter security assessments, real-world threat simulation |
| Setup Complexity | Requires internal access and documentation | Requires limited access and documentation | Minimal setup — tester starts from scratch |
| Risk of Disruption | Low (more controlled) | Medium | Higher risk of disruption (due to blind probing) |
| Realism | Less realistic (not how external attackers operate) | Balanced realism | Highly realistic (mimics actual attacker behaviour) |
Why Is Penetration Testing Important?
Penetration testing is important because cyber attacks are growing in severity, frequency and hackers are targeting businesses of all sizes. Threats such as ransomware, phishing, cross-site scripting (XSS), and SQL injection pose risks to sensitive data and business operations. Penetration testing adopts a hacker’s perspective to find and reduce these risks before they are exploited.
Unlike automated scans or basic security assessments, penetration testing identifies real, proven vulnerabilities and demonstrates their potential impact on the business. This allows IT and security teams to prioritise and address issues. Ethical hackers also bring creativity and real-world tactics to the process, often combining multiple attack vectors to expose hidden weaknesses, just as a malicious attacker would.
Choosing the Right Pen Test Provider
Now that you have a clearer understanding of the different types of penetration testing, you’re in a stronger position to improve your organisation’s security and maintain compliance with industry standards. Choosing the right testing approach can be complicated, but that’s where Rootshell Security can help. Our expert-led penetration testing services are designed to find vulnerabilities before attackers can exploit them. Book a demo today and take the first step toward a more secure future.