Vulnerability management is essential to every modern cyber security strategy. However, it’s impossible to fix every issue discovered by vulnerability scans or penetration tests. A Vulnerability Management Process Flow Chart can guide IT security teams’ decision-making to ensure they take the best steps for the safety of their organizations.
Read on to learn about how a Vulnerability Management Process Flow Chart can benefit you.
What is Vulnerability Management?
Vulnerability management is the process of identifying, evaluating, prioritizing, and remediating security flaws within an organization’s network, systems, and applications.
The goal of vulnerability management is to ensure that organizations have complete visibility and control of weaknesses that exist within their IT estates on a continuous basis.
The terms ‘vulnerability management’ and ‘vulnerability assessment’ are oftentimes used interchangeably, but they have different meanings. Vulnerability management encompasses the end-to-end process of managing security issues, whereas a vulnerability assessment is a type of IT security test that discovers security issues within an organization’s network.
Why is Vulnerability Management Important?
Vulnerability management is an important part of an organization’s IT security strategy. Without an effective vulnerability management process, an organization’s data, personnel, and reputation could be at risk.
A successful vulnerability management process makes sure that IT security teams can find and fix security issues as quickly as possible. This helps reduce your organization’s attack surface and prevent cyberattacks, which could have serious consequences for your data, personnel, and reputation.
A well-structured vulnerability management process also helps you to allocate resources more effectively. Not all vulnerabilities pose the same level of risk, and so it’s more efficient for teams to prioritise issues based on severity so that you can focus on the most damaging threats first.
What is the Vulnerability Management Process?
Vulnerability management is a process that begins with discovering security issues and ends with validating that remediation has been successful. It encompasses all the actions an IT security team takes to identify, address, and manage vulnerabilities within an organization’s network.
A successful vulnerability management process should be continuous, intelligence-driven, and designed to allow teams to fix issues quickly, as new vulnerabilities can appear at any time.
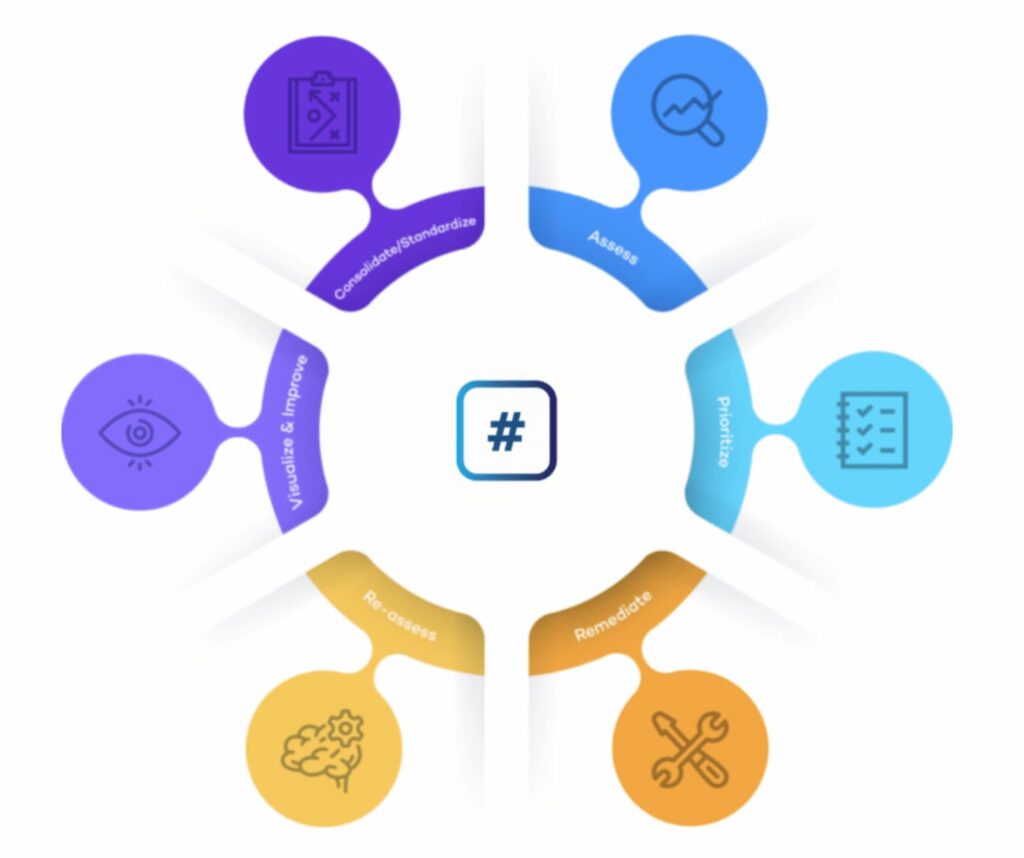
We have summarised the complete process of vulnerability remediation below.
Discover: Identify vulnerabilities within your organization’s network by carrying out vulnerability scanning.
Consolidate: Centralise your assessment results in one place with tools such as The Rootshell Platform. This could involve transferring results from PDFs to a standardised database.
Assess: Analyse your vulnerabilities to establish their severity, the likelihood that they will be exploited, and what impact they could have on your organization.
Prioritize: Assign severity scores to your assets in line with your analysis and other factors such as resource availability.
Remediate: The vulnerability management remediation phase involves implementing your remediation program to resolve vulnerabilities in line with your organization’s priorities.
Re-assess: Verify whether your remediation efforts have been successful. Ultimately, your vulnerability management process should reduce the risk of your organization being compromised.
Visualize and improve: Continuously improve your vulnerability management process; resolve any bottlenecks and ensure compliance with your organization’s service level agreements. For example, could you reduce your time-to-remediate (TTR)?
Vulnerability management solutions like The Rootshell Platform help organizations modernize their vulnerability management processes and improve remediation from start to finish.
Best Practices for your Vulnerability Management Process
Continuous Vulnerability Management Processes
The time between security assessments is the time when your organization could be at risk. Your vulnerability management process should be an ongoing process to close these gaps.
Intelligence-Led Approach
An intelligence-driven approach to vulnerability management enables IT security teams to gain context of their issues, prioritize most effectively, and accurately evaluate risk.
Streamlined Processes
Bottlenecks within threat and vulnerability management processes can lose you precious time. Processes should be simplified, giving your team the tools to address issues quickly and efficiently.
Collaboration Across Teams
Encourage collaboration between IT, security, and business teams. Sharing insights and responsibilities means that vulnerabilities are addressed quickly and in alignment with organizational priorities.
Metrics and KPIs
Establish key performance indicators (KPIs) to measure the effectiveness of your vulnerability management process, such as mean time to remediate or number of vulnerabilities addressed per month.
Policy and Compliance Alignment
Ensure your vulnerability management process aligns with organizational security policies, industry standards, and regulatory requirements. Compliance helps mitigate risk and protects against legal or reputational consequences.
Vulnerability Management vs. Vulnerability Assessment
Vulnerability assessment and vulnerability management both aim to identify and address security weaknesses, but they function differently. Vulnerability assessment provides a snapshot of the current security posture, while vulnerability management delivers continuous, real-time insights, reporting, and guidance for ongoing remediation.
Feature | Vulnerability Assessment | Vulnerability Management |
Definition | The process of identifying and reporting vulnerabilities | The ongoing process of finding, fixing and monitoring vulnerabilities |
Purpose | To find and report potential security weaknesses. | To continuously reduce risk by addressing vulnerabilities and improving overall security. |
Scope | Point-in-time evaluation of systems or networks. | Continuous, lifecycle-based approach covering detection, remediation, and verification. |
Frequency | Conducted periodically or before major updates. | Continuous and cyclical, adapting to new vulnerabilities as they arise. |
Outcome | List of identified vulnerabilities with severity ratings. | Fixed vulnerabilities and metrics on remediation effectiveness. |
Tools Used | Vulnerability scanners, penetration testing tools. | Vulnerability management platforms, dashboards, tracking systems, and integration with IT workflows. |
Responsibility | Performed by security analysts or penetration testers. | Managed by IT security teams with oversight from security management. |
Goal | To understand the current security weaknesses. | To reduce exposure to threats and maintain long-term security resilience. |
How to Choose the Best Vulnerability Management Tools
Vulnerability management tools can help IT security teams improve a wide range of processes within vulnerability management, from data analysis and reporting, to project management and collaboration, and much more.
Many different tools can aid specific parts of the vulnerability management process, such as ticketing systems to assign remediation tasks and spreadsheets to track open issues.
Selecting the right vulnerability management (VM) tool can help you to maintain a strong security posture. Here are some factors to consider when evaluating vulnerability management tools:
1. Coverage
A good vulnerability management tool should be capable of scanning all of your assets. It should also support multiple platforms and be able to integrate data from other security assessments, such as penetration tests.
2. Accuracy and Reliability
Look for tools that don’t show false positives and provide clear severity ratings for vulnerabilities. Accurate detection means that your team focuses on real threats rather than wasting time on less important issues.
3. Ease of Use
The tool should have an intuitive interface, easy-to-understand dashboards, and reporting features. This means that your security team can quickly interpret findings and take action without unnecessary complexity.
4. Automation and Integration
Automation capabilities, such as scheduled scans, automated reporting, and workflow integration with IT ticketing systems, can reduce manual work.
5. Prioritisation and Risk Assessment
Not all vulnerabilities pose the same risk. The best tools provide contextual insights, helping you prioritise vulnerabilities based on business impact and exploitability.
6. Remediation Support
Look for tools that offer actionable guidance on remediation steps, track remediation progress, and validate that vulnerabilities have been successfully addressed.
7. Reporting and Metrics
Make sure your vulnerability management tool can generate reports tailored for different audiences, including technical teams and executive leadership.
Rootshell’s Vulnerability Management Process Flow Chart
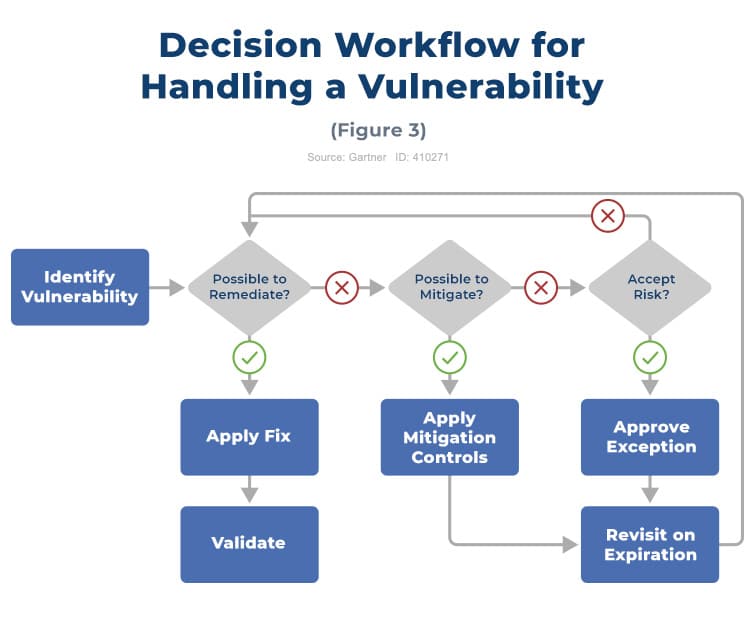
Now we’ve covered the Vulnerability Management Process, what about the process of handling specific vulnerabilities? Not all vulnerabilities are managed the same way – for example, a patch may not be available, or your organization may not have enough resources to fix every ‘medium’ issue.
A Vulnerability Management Process Flow Chart is a useful way of considering how to remediate vulnerabilities on a case-by-case basis.
Next Generation Vulnerability Remediation
The Rootshell Platform is a vendor-agnostic vulnerability remediation solution. It enables you to manage results from any type of IT security assessment, including penetration tests, giving you the unique advantage of analysing different assessment results alongside each other, in one standardized format.
The Platform’s unique features help you with every stage of the vulnerability remediation process, improving efficiency from start to finish.
How The Rootshell Platform Improves Every Stage of Vulnerability Remediation
- Consolidate Your Assessment Data: Import results from any penetration testing vendor or security service provider into a single, centralized hub.
- Integrate and Standardize: Create a unified database for all assessment results, eliminating silos and enabling comparative analysis across different assessments.
- Contextualize and Prioritize: Gain real-time insights to understand issues in context and focus on the most critical vulnerabilities first.
- Streamline Remediation Workflow: Speed up remediation with third-party integrations, collaboration tools, and live updates from testers.
- Track and Validate Results: Measure remediation efforts against SLAs and key metrics, such as monthly remediation rates, to ensure accountability.
- Visualize and Analyse Risk: Access holistic dashboards and automated reporting to analyse technical risk across your entire organization effortlessly.
Learn more about vulnerability remediation management tools and see how the Rootshell Platform can improve your security operations.



