In today’s ever-evolving cyber landscape, Vulnerability Intelligence has emerged as an indispensable pillar of any robust vulnerability and threat management strategy. By offering an in-depth dive into potential risks and threats, it acts as the compass that security and IT teams need to navigate the treacherous waters of cyber threats.
Vulnerability Intelligence is not just a buzzword. It’s the backbone that enables organizations to gain insights into the real-world context of a threat or risk, which in turn ensures that remediation efforts are laser-focused and effective.
What Exactly is Vulnerability Intelligence and Why is it Crucial?
Vulnerability Intelligence can be succinctly defined as the data that provides context about security risks within an organization’s IT estate. It goes beyond mere CVEs or Common Vulnerabilities and Exposures. Think of it as a more specialized form of threat intelligence, specifically tailored to vulnerabilities.
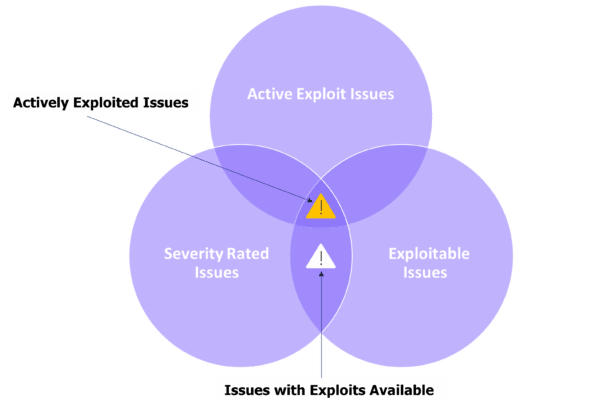
While it’s true that every organization may encounter thousands of threats and issues, it’s also a fact that only a fraction of these ever get exploited. This is where the capability of Vulnerability Intelligence shines. It allows teams to filter through the overwhelming data to pinpoint those vulnerabilities that pose the greatest risk.
For instance, understanding exploit availability, or learning if specific vulnerabilities are being actively leveraged by attackers in real-time, is essential. It offers a lens through which one can view and prioritize vulnerabilities based on real-world threat scenarios. Integrating such intelligence into the threat and vulnerability management cycle becomes the key to effective vulnerability prioritization.
Sourcing Comprehensive Vulnerability Intelligence: Steps to Success
The value of Vulnerability Intelligence lies in its integration. But the question arises – how does one gather this intelligence? A risk-based approach is paramount. And sourcing from multiple platforms ensures a holistic view.
There’s a plethora of sources that organizations can leverage for this intelligence. From official governmental agencies to non-profit archives, the reservoir is vast.
- Cybersecurity and Infrastructure Security Agency (CISA): CISA remains a benchmark for threat intelligence. Informed by US intelligence and corroborated by real-world events, it offers indispensable insights into cyber threats.
- Zero Day Initiative: This initiative is a reservoir of 0-day vulnerabilities, contributions courtesy of a diverse global community of research experts.
- Exploit DB: An invaluable tool in the threat intelligence toolkit, it’s a non-profit archive that offers the latest in exploit vulnerability intelligence. The data is a compilation from direct submissions, mailing lists, and a variety of other publicly known sources.
By cross-referencing the intelligence from these sources with an organization’s vulnerability data, teams can spot potentially exploitable issues. This is the essence of using vulnerability intelligence to prioritize.
The Rootshell Platform’s Vulnerability Intelligence
The Rootshell Platform is our next-generation vulnerability management tool, designed to redefine processes from inception to culmination. One of its standout features? Automated, real-time AI- led threat intelligence, personalized to cater to an organization’s unique needs.
But it’s not just about intelligence; it’s about actionable insights. With features like industry-leading Active Exploit Detection, The Rootshell Platform doesn’t just identify issues; it zeroes in on those vulnerabilities in software that are being actively exploited.
This continuous monitoring capability ensures that teams always have an edge, turning point-in-time vulnerability intelligence into a continuous intelligence service.

In Conclusion
The cyber world is fraught with vulnerabilities. Yet, with the right Vulnerability Intelligence, organizations can transform these vulnerabilities from potential points of entry for attackers into fortresses of defense. Every single alert, every piece of data, and every intelligence service offering contributes to crafting a safer, more secure digital realm.
By understanding and leveraging the power of Vulnerability Intelligence, organizations can ensure they are not just reacting but proactively shaping their security strategy for the future.
Subscribe So You Never Miss an Update




