Without vulnerability management reporting, vulnerability data becomes noise. Vulnerability management reports help teams gain clarity on the status of their vulnerability management programs, deduce actionable insights, and ultimately, execute the best remediation to protect their organizations.
Below, we have summarized eight components you could include in your vulnerability management reporting to make your reports as effective as possible.
What is a Vulnerability Management Report?
A vulnerability management report organizes and presents data as digestible, relevant, and actionable insights.
Vulnerability management reports can be tailored to IT security teams, or an organization’s executives. The former helps teams understand the status of their remediation efforts and plan ahead. The latter helps IT security leaders present the success of their vulnerability management strategies and demonstrate return-on-investment.
Why is a Vulnerability Management Report Important?
Vulnerability management reports ensure teams make data-led decisions that are backed up by the most important and current information, so teams can take the best course of action when planning and executing remediation.
Regularly reporting on vulnerability management also helps IT security leaders evaluate their vulnerability management programs, so they can easily identify what is successful and where improvements are needed.
A vulnerability management report is also helpful for demonstrating the success of a vulnerability management program to executives, and can help make a case for additional investment.
Ultimately, well-crafted vulnerability management reports provide teams with visibility and clarity of their remediation programs. With effective reporting, teams can be continuously aware of the status of their most important assets and critical issues, to keep their organizations secure.
What should a Vulnerability Management Report contain?
There is no single way to create an effective vulnerability management report, as the content of a report needs to be tailored to the readers and the goals of the organization.
We have suggested eight components for vulnerability management reports we think are most useful for IT security teams.
1. Outstanding issues: You could report on the number of outstanding issues within your estate, broken down by severity. This can be represented as a line graph, to show the number of outstanding issues within your estate on a monthly basis. This gives a good indication of how your remediation program is performing over time.
2. Exploitable issues: The number of exploitable issues within your estate, including how many of these have active exploits, is critical. This helps contextualize your vulnerability management data and highlights the issues that need immediate attention.
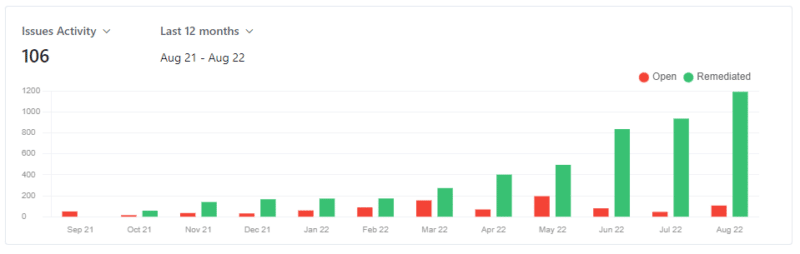
3. Open vs Remediated issues: You could track the number of open vs remediated within your estate on a monthly basis. This could be represented as a stacked bar graph to illustrate your remediation rate over time.
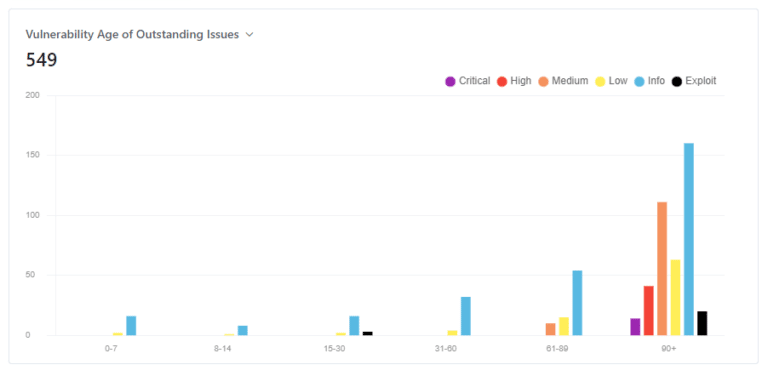
4. Vulnerability Age: You could report on how old your outstanding issues are in number of days, broken down by severity level. This will also help calculate your mean-time-to-remediate.
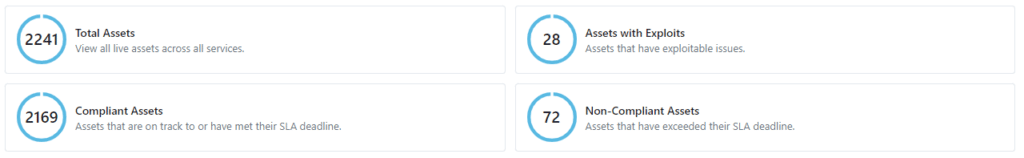
5. Compliance: Keeping track of your organization’s performance in relation to your Service Level Agreements (SLAs) will help you evaluate your remediation program and pinpoint any bottlenecks. You could report on how many assets are compliant and non-compliant with your SLAs.
6. Assets: As well as keeping an up to date asset inventory, you could report on how many of your assets have exploitable issues, as well as how many of your ‘priority’ assets are compliant.
7. System Owner Leader Board: Leader boards can be motivational reporting tools that showcase how well your system owners are performing their remediation duties. Your leader board could rank the number of open issues against an asset’s owner.
8. Most Reported Issues: By tracking which issues most commonly affect assets within your estate, you can more easily prioritize which vulnerabilities should be actioned first.
Automate Vulnerability Management Reports with The Rootshell Platform
The Rootshell Platform is our vendor-agnostic platform that helps you implement modern and effective vulnerability management programs, reducing mean-time-to-remediate by up to 61%.
Rootshell automates vulnerability management reporting by generating dashboards and metrics from your data, including each of the eight reporting components we have outlined above. Read more on vulnerability management metrics.
Rootshell maximises the actionability of your data, takes the legwork out of reporting and makes it effortless to ensure your decision making is backed up by the most important and current information.
As well as automating vulnerability management reporting, Rootshell:
- Centralizes security issues: Rootshell is vendor-agnostic, so you can use it to consolidate results from any vulnerability scanner or penetration testing vendor. Managing all your cloud vulnerabilities in one place, as well as non-cloud issues makes it seamless to continuously analyse, prioritize, and manage all issues across your estate.
- Aids intelligence-driven prioritization: Rootshell’s industry-leading Daily Exploit Detection alerts you to exploits for your issues on a daily basis, so you can gain the context needed to prioritize most effectively.
- Streamlines remediation: Rootshell modernizes vulnerability management programs and makes it easy for teams to deliver fast and effective remediation, by reducing manual processes, integrating with ticketing systems, and much more.
- Delivers real-time alerts: Rotoshell ensures you have real-time insight into your threat landscape, by providing you with live updates from tests and continuous cyber threat intelligence alerts tailored to your digital estate.