Security assessments can inundate teams with data. Translating your data into insightful vulnerability management metrics can make it more useful and actionable. In this article, we have suggested eight vulnerability management metrics for implementing an effective, data-driven remediation program.
Why is Vulnerability Management Important?
Vulnerability management is an essential part of an organization’s IT security strategy.
Vulnerability management helps IT security teams ensure that critical issues are discovered, analysed, and remediated as fast and efficiently as possible. This is critical to preventing cyberattacks, which could have devastating consequences for an organization’s data, personnel, and reputation.
Vulnerability management also helps organizations allocate resources more effectively. Not all security vulnerabilities pose the same risk, and many may not even need to be remediated. Effective vulnerability management provides a framework for security teams to assess and prioritize vulnerabilities, so organizations can ensure that resources are allocated to the most critical issues.
Another reason why vulnerability management is so important is because an organization’s threat landscape is ever-changing. The cyclical process of vulnerability management helps security teams assess and measure their security posture on a continuous basis so that there is very little opportunity for critical issues to be left unaddressed.
Vulnerability Management Best Practices
A vulnerability management program plan should empower IT security teams to remediate as effectively and efficiently as possible. Consider these vulnerability management best practices when building a vulnerability management program.
- Continuous: The time between security assessments is the time when your organization could be at risk. Continuous vulnerability management closes these gaps.
- Data-driven: IT security teams should be led by relevant vulnerability management metrics, helping to effectively plan, prioritize, and evaluate remediation efforts.
- Streamlined: Bottlenecks within a vulnerability management program can lose your team precious time. Processes should be streamlined, empowering teams to address issues fast and efficiently.
8 Vulnerability Management Metrics to Measure
Here are eight vulnerability management metrics that could be relevant to your remediation program:
- Monthly remediation rate (the number of remediated issues versus outstanding issues).
- The number of exploitable issues within your estate (corroborated by intelligence feeds), as well as how many of these exploits are active.
- The percentage change in the number of issues within your estate per month, for each severity score.
- The number of outstanding issues within your estate shown over time. This can be expressed as a graph to reveal any trends.
- The age of outstanding security issues, broken down by severity level.
- Mean-time-to-remediate (MTTR), broken down by severity level. This can also be expressed as a graph to show trends over time.
- There are a number of metrics you could measure relating to your assets:
a. The number of assets with exploits
b. The number of compliant assets (with regards to your SLAs)
c. The number of non-compliant assets - The number of outstanding issues per system owner. This can be expressed as a leader board to assist with remediation follow-up.
The Rootshell Platform generates all these metrics for you, presented in clear Dashboards.
Effortlessly Track Vulnerability Management Metrics with The Rootshell Platform
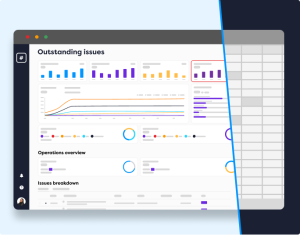
The Rootshell Platform is our vendor-agnostic platform that helps you implement modern and effective vulnerability management programs, reducing mean-time-to-remediate by up to 61%.
Rootshell automates vulnerability management reporting by generating dashboards and metrics from your data, including each of the eight vulnerability management metrics we have outlined above.
Rootshell maximises the actionability of your data, takes the legwork out of reporting and makes it effortless to ensure your decision-making is backed up by the most important and current information.
As well as automating vulnerability management metrics, Rootshell:
- Centralizes security issues: The Rootshell Platform is vendor-agnostic, so you can use it to consolidate results from any vulnerability scanner or penetration testing vendor.
- Aids intelligence-driven prioritization: Rootshell’s industry-leading Active Exploit Detection alerts you to active exploits for your issues, so you can gain the context needed to prioritize most effectively.
- Streamlines remediation: Rootshell modernizes vulnerability management programs and makes it easy for teams to deliver fast and effective remediation, by reducing manual processes, integrating with ticketing systems, and much more.
- Delivers real-time alerts: Rootshell ensures you have real-time insight into your threat landscape, by providing you with live updates from tests and continuous cyber threat intelligence alerts tailored to your digital estate.
Read about outcome-driven metrics for cybersecurity.



