Vulnerability Assessment and Penetration Testing Services
The security of your organization’s data and systems is of paramount importance. Rootshell Security is committed to delivering top-tier vulnerability assessment and penetration testing services to help you safeguard your business.

Join 1,000+ leading companies who trust Rootshell Security
What is vulnerability assessment and penetration testing?
It is a multi-step process designed to evaluate the security of your network, applications, and systems. It is divided into two main components:
- Vulnerability Assessment
Here, the focus is on identifying security gaps, weaknesses, and areas of non-compliance in your digital landscape. This is achieved through a series of automated scans and manual testing, with the aim of creating an inventory of all potential vulnerabilities.
- Penetration Testing
This stage goes beyond merely identifying vulnerabilities. Our team of expert penetration testers actively exploit these weaknesses to understand their potential impact. This involves simulating real-world cyber-attacks to assess how resilient your security measures really are. Read more on PTaaS.
Why Do You Need Vulnerability Assessment and Penetration Testing Services?
In today’s digital landscape, cyber threats are escalating at an alarming rate, putting organizations at unprecedented risk. Cyber security is no longer a luxury but an absolute necessity for safeguarding your network, applications, and business infrastructure. Vulnerability Assessment and Penetration Testing (VAPT) are critical services that can fortify your organization’s defenses against cyber threats. Rootshell Security offers top-notch vulnerability assessment and penetration testing services aimed at identifying and mitigating security vulnerabilities, thereby minimizing the risk of data breaches and unauthorized access to your systems.
There are many reasons why organizations need VAPT. Some of the most common reasons include:
- To comply with industry regulations. Many industries, such as financial services and healthcare, have regulations that require organizations to have a program for this in place.
- To protect sensitive data. These services can help organizations identify and fix security vulnerabilities that could be exploited to steal sensitive data, such as financial information or customer records.
- To reduce the risk of cyber attacks. These services can help organizations identify and fix security vulnerabilities that could be exploited by attackers. This can help to reduce the risk of a successful cyber attack.
- To improve overall security posture. Assessments and testing can provide organizations with a comprehensive view of their posture and identify areas where improvements can be made. This can help to improve overall security and reduce the risk of attack.
The value of vulnerability assessment and penetration testing
These services serve as a preventive healthcare check-up for your organization’s digital assets. By identifying weaknesses before they can be exploited and testing your organization’s response capabilities, VAPT can save you from the enormous costs and reputational damage associated with data breaches. Moreover, this comprehensive service can help you maintain customer trust, meet regulatory compliance requirements, and secure competitive advantages by ensuring the robustness of your security measures.
What should organizations consider when selecting a VAPT provider?
Selecting the right provider is crucial. Factors to consider include the expertise and qualifications of the team, the range of services offered, and whether the provider can customize their services to suit your specific needs. Compliance with industry standards, as well as positive customer testimonials, can also be strong indicators of a reliable provider.
Our vulnerability assessment and penetration testing services:
Rootshell Security offers a comprehensive service that includes both vulnerability assessment and penetration testing. Our services are tailored to the specific needs of each organization, and we work with you to develop a plan that will meet your security goals.
These services include:
- Vulnerability assessment
- Penetration testing
- Red Team operations
- Web application penetration testing
- Pen testing as a service (attack surface management)
We offer cyber threat intelligence (CTI), managed vulnerability scanning (MVS), phishing assessments, penetration tests, and red team assessments as part of a combined Penetration Testing as a Service security package. These are offered as a series of recurring monthly, quarterly, and yearly undertakings to fortify your organization year-round.
Our Penetration Testing as a Service (PTaaS) packages are tailored to meet your objectives, risk appetite, and budget. Below, you can see an example of a fully managed PTaaS package. We can help you choose the services that best fit your organization.
The benefits of Penetration Testing as a Service
Bolster your security strategy and ensure year-round protection with Penetration Testing as a Service (PTaaS).
Year-round protection
A lot can happen between annual penetration tests. Our Penetration Testing as a Service tests your digital infrastructure year-round, so you can ensure your cybersecurity health is maintained and improved on an ongoing basis.
Prepare for a real-world attack
Penetration tests are one of the most effective ways to evaluate your security level. By emulating the tactics, techniques, procedures used by hackers, our services truly put your organization’s defences to the test.
Uncover critical vulnerabilities
As the risk of cyber-attacks continues to increase, it’s crucial you have complete visibility of your organization’s vulnerabilities. Our Pen Testing as a Service identifies any vulnerabilities, from low to high risk, so you can take action.
Effectively remediate risk
Penetration Testing as a Service provides you with the data you need to resolve vulnerabilities. Our penetration testers offer expert support so you can remediate as quickly and effectively as possible.
Comply with security standards
Carrying out penetration testing is essential for meeting a number of different regulatory standards. Our CREST-certified pen testing will ensure your organization is compliant.
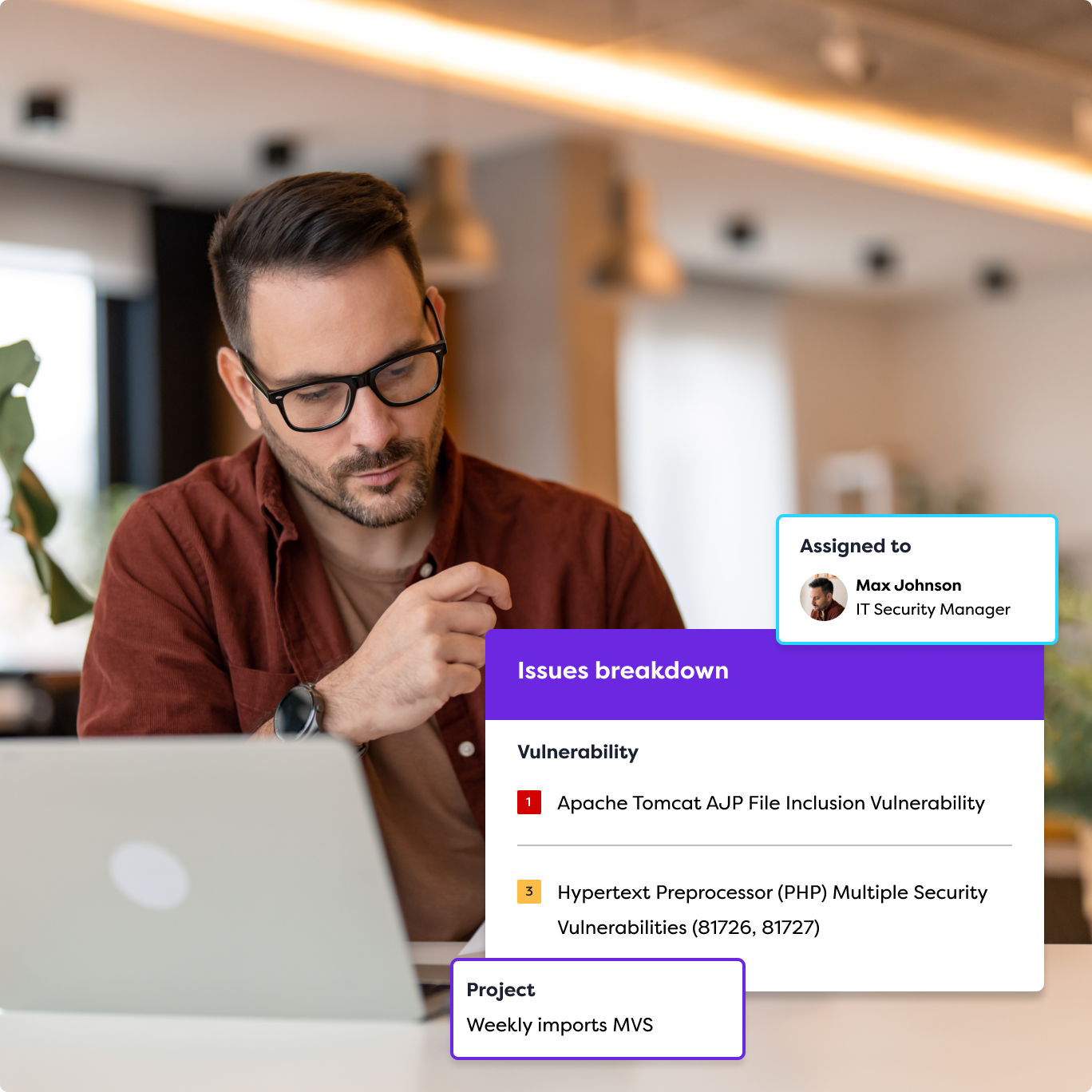
Types of Pen Testing
We offer a range of penetration testing services. Our security consultants can help advise which types of pen testing services your organization needs. Some of the most common types of penetration testing that we offer include:
Red Teaming
This type of testing simulates a real-world attack on an organization’s systems and networks.
External Penetration Testing
External penetration testing focuses on the security of an organization’s external-facing assets, such as its website, web applications, and email servers.
Internal Penetration Testing
This type of testing focuses on the security of an organization’s internal networks and systems.
Wireless Penetration Testing
This type of testing focuses on the security of an organization’s wireless networks.
Social Engineering Testing
This type of testing focuses on the human element of security by testing how susceptible employees are to social engineering attacks.
Other
We also offer a variety of other penetration testing services, such as: Cloud penetration testing, Mobile penetration testing, IoT penetration testing, Industrial control systems penetration testing
Hear why the world’s top companies trust us for external penetrating testing

Boost your cybersecurity with penetration testing
Our vulnerability assessment and penetration testing process
Our process is designed to be efficient and effective. We start by understanding your organization’s security needs and goals. We then develop a plan that will meet those needs and goals.
Once the plan is in place, we execute the assessment and testing phases. We then provide you with a detailed report that outlines our findings and recommendations.
How this helps organizations protect their systems and data?
Our services offer a multi-layered approach to security, providing robust protection against various forms of cyber threats. This is achieved through a rigorous process that includes identifying security vulnerabilities, actively testing these vulnerabilities, and advising on how to effectively mitigate them. By being proactive, you can significantly reduce the likelihood of suffering a data breach or unauthorized access, thereby safeguarding both your systems and data.
Why choose Rootshell Security as your VAPT provider?
Rootshell Security is revolutionizing Vulnerability Management with our Rootshell Platform. By consolidating penetration testing results, vulnerability scanning, and integrating AI-Led Active Exploit intelligence, we make traditional processes redundant and transform results into prioritized, actionable insights.
We have a team of experienced security professionals who are experts in vulnerability assessment and penetration testing. We also have a proven track record of success, having helped organizations improve their security architecture.
Here are some of the reasons why you should choose Rootshell Security as your vulnerability assessment and penetration testing provider:
Expertise
Our team of security experts has extensive experience in vulnerability assessment and penetration testing. We have a deep understanding of the latest security threats and vulnerabilities.
Process & Reporting
We have a proven process for conducting VAPT assessments and testing. This process is efficient and effective, and it ensures that we meet your security needs. We also supply detailed, real-time reports that outline our findings and recommendations. These reports are easy to understand and actionable.
Qualifications
Our team is certified by leading security organizations, such as CREST, CHECK, FSQS registered, ISQ 23001 and ISQ 9001 registered. See below.
Support
We offer 24/7 support to our clients. We are always available to answer your questions.
