Vulnerability and penetration testing services are two types of cyber security assessments. They differ in breadth, depth, scope, and serve different objectives to help organisations achieve their security goals. Read on to find out how vulnerability and penetration testing services can benefit your organisation and how they can work together to give you an essential advantage over an attacker.
What is vulnerability and penetration testing?
Vulnerability scanning is an automated service that uses software to analyse networks for security vulnerabilities. The software continuously scans for issues, which helps organisations identify and eliminate threats on an ongoing basis. Vulnerability scanning identifies a wide range of issues, including unpatched software, encryption issues, injection flaws, and broken authentication.
Vulnerability scanning can be conducted in-house or as a managed service. With a Managed Vulnerability Scanning (MVS) service, you can expect to receive optimal calibration, expert advice, and the dismissal of false positives, non-issues, and errors, which can waste in-house teams valuable time if they lack the experience needed to validate results.
Penetration testing combines both automated and manual techniques to assess an organisation’s networks, systems, and applications for security weaknesses. Also known as ‘ethical hacking’, a pen tester attempts to exploit vulnerabilities using the same methods as real-world threat actors to determine whether a vulnerability could enable an attack.
Penetration tests are project-based and focus on a specific area of an organisation’s digital infrastructure. For example, an organisation could conduct penetration testing cloud services or web application penetration testing services.
Penetration tests can also assess the resilience of your personnel to cyber attacks, who are especially vulnerable to being tricked by attackers into divulging confidential information. These types of pen tests are known as ‘social engineering’ and include phishing assessments and USB drops.
What is the difference between vulnerability and penetration testing services?
Vulnerability scanning is:
- A continuous assessment
- Broad rather than in-depth
- Automated using software
- Identifies as many issues as possible
- The end result is a list of security vulnerabilities identified
Penetration testing is:
- A project-based assessment
- In-depth
- Relies on a manual approach – a pen tester emulates how a real-world threat actor would attempt to exploit vulnerabilities
- Identifies issues within a specific system (e.g. a web application) and evaluates how they could be exploited in an attack
- The end result is an actionable report that provides remediation advice and recommendations on how to improve an organisation’s defences
What are the benefits of vulnerability and penetration testing services?
As vulnerability and penetration testing services differ in scope and objectives, they offer organisations different benefits.
Vulnerability scanning provides organisations with a way of continuously surveying for security issues. This gives year-round visibility of issues as they arise, which plays a crucial role in maintaining security in between project-based testing.
Penetration tests are most beneficial when an organisation requires an in-depth assessment of how resilient its systems are to an attack. Pen tests provide actionable results and remediation advice to help organisations reduce risk.
How can vulnerability and penetration testing services work together?
Rather than choosing one of the services, conducting both vulnerability and penetration testing services can provide your organisation with a stronger security solution that combines the benefits of both. Below you can see an example of what your annual security testing could look like with both services.
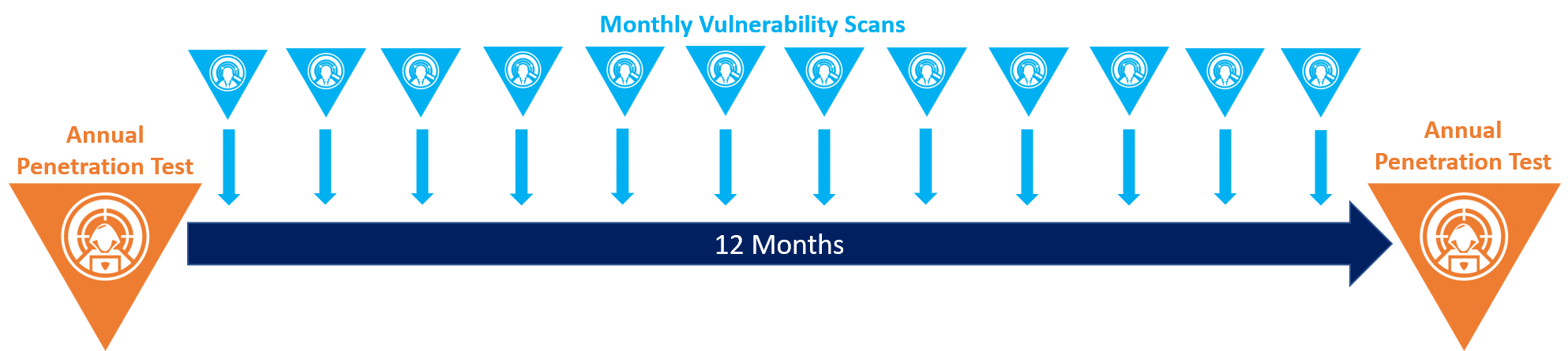
This ‘continuous’ approach provides far greater protection than relying on just an annual point-in-time penetration test, but also offers the depth that vulnerability scans alone cannot provide. Find out more about how continuous penetration testing could work for your organisation.
Rootshell Security’s vulnerability and penetration testing services
As the provider of managed vulnerability scanning and penetration testing services for some of the UK’s leading organisations, we can provide expert advice to help you implement the best security solution. Below are just some of the reasons our clients choose us as their security partner.
- CREST-certified testers: CREST is an internationally recognised accreditation for penetration testing services. Our CREST-certified testers work to the highest technical and ethical standards.
- Quality assured: We deliver our security services to industry standards, such as Open Web Application Security Project (OWASP) guidelines, the National Institute for Standards and Technology (NIST), and the Penetration Testing Execution Standard (PTES).
- Expert advice and support: Our highly experienced testers provide you with expert guidance and support throughout. You will receive clear reports and advice, along with step-by-step instructions, ensuring you know exactly how to remediate and reduce risk.
Harness the benefits of both vulnerability and penetration testing services with Rootshell Security’s Continuous Penetration Testing services.
Get in touch to discuss the best security solution for your organisation with our expert consultants.
Subscribe So You Never Miss an Update




