Rootshell Platform’s latest update gives teams powerful new tools to prioritize more effectively than ever before, by offering improved ways to review and manage automatically updated vulnerability statuses.
In addition, the team continues to deliver on our promise to regularly add new integrations for the most popular cyber security products on the market, welcoming Sentinel One and Horizon3.ai to our growing list.
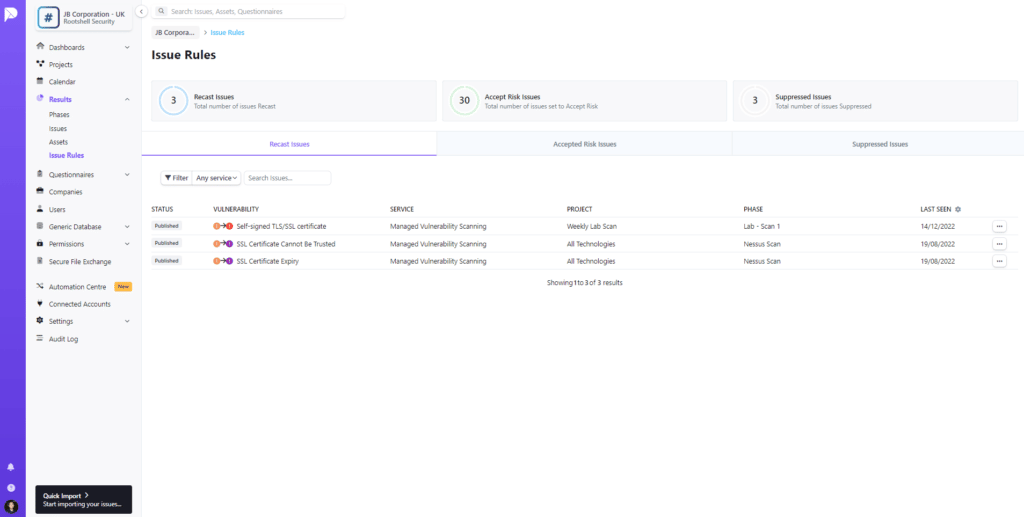
Recast Issues to Improve Prioritization Based on Business Context
This update adds the ability for Rootshell users to easily review and manage vulnerabilities that have had their status changed automatically based on user-defined settings.
As an example, users can change the status of vulnerabilities that exist on particular assets, or those with certain names, to be automatically marked as accept risk, supressed, or even choose to recast their risk rating.
This can be useful in situations where, for example, a UAT environment has an out of date certificate. An organisation may want to reduce the risk rating as this is not a live environment, and may be deemed less important based on business context.
Conversely, an out of date certificate discovered on a production environment may warrant the risk rating being recast higher, as this could be seen by an organization as a more pressing issue.
Rootshell’s Platform now integrates with Sentinel One and Horizon3.ai
The list of Rootshell Integrations continues to grow, with Sentinel One and Horizon3.ai (previously known as NodeZero) added to the lineup.

Sentinel One provides Extended Detection and Response (XDR) capabilities with their Singularity XDR Platform encompasses AI-powered prevention, detection, response, and threat hunting across user endpoints, containers, cloud workloads, and IoT devices.

Horizon3.ai enables organizations to continuously assess the security posture of their enterprise across many attack surfaces.
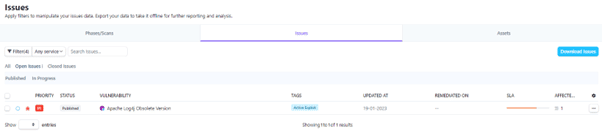
Enhanced Asset Visibility Makes it Easier to Prioritize Remediation Efforts
Rootshell now reports your issues with the added context of asset prioritisation across all vulnerability view types.
As with the inclusion of the exploit and active exploit bug icon, the priority asset badge (The P1, P2 logos) is now also included to make it even easier for clients to prioritise their remediation efforts.
This addition now makes it possible for clients to filter to a desired dataset that fits their current business priorities, for example, users can ask Rootshell:
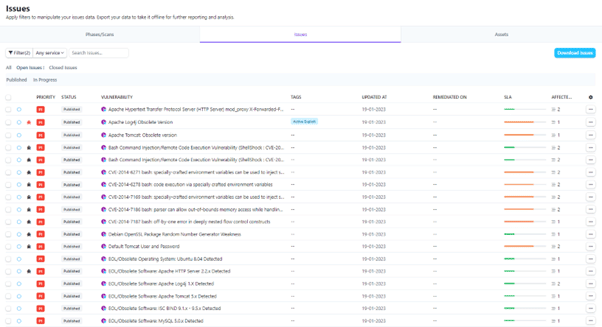
Show me all P1 assets with Critical issues:
Show me P1 assets with Critical Issues, that have exploits available:
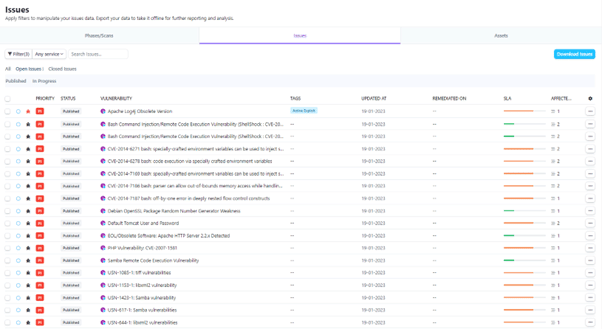
This can be drilled down even further still. Show me any of the remaining issues then have active exploits:
Improved Support for Legacy Reporting Methods
For those that still want to be able to export reports in PDF format, the platform is now able to produce a PDF report grouped by asset. This marks a distinct improvement from the general penetration testing industry standard for PDF reports, which are ordered by vulnerability severity.
Asset-ordered PDF reports will be grouped by Asset first, with all the vulnerability data included in this section in the normal Critical, High, Medium, and Low rated vulnerabilities fashion.
Tighten Up Automatic Imports to Gain Further Clarity
For imports that the Rootshell Platform handles automatically, users are now able to define which severity levels should be included or excluded. This gives users the power to omit vulnerabilities that they may not be interested in, such as informational or advisory issues that an organization may decide are superfluous.
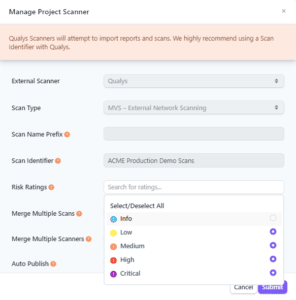
For example, an organization such as a University, College, or School may not want to include informational issues, as most scans are going to give them thousands and thousands of lines of informational vulnerabilities whenever a student plugged in a USB device (USB device added to host).
Some teams see informational vulnerabilities as ‘just noise’; this is should be wholly based on organizational preference and business context, but others want all the data added to their environment so it can be interrogated, analysed or reviewed at a later date.
Get in touch to find out more about how Rootshell can benefit your organization.
Subscribe So You Never Miss an Update