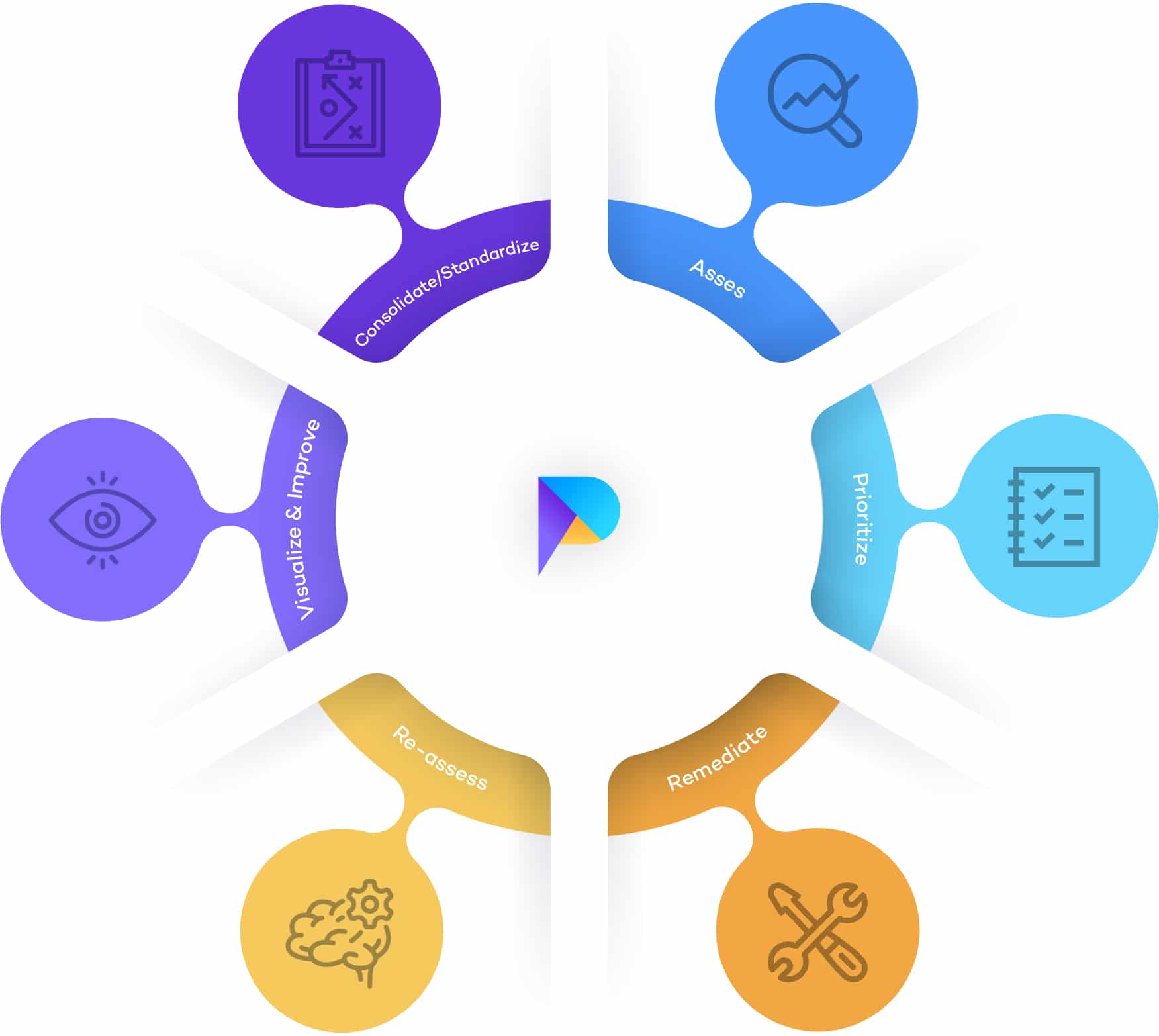
6 Vital Ingredients of Modern Vulnerability Management
You’ve received results from your security testing provider – what happens next?
Effective vulnerability management is essential to ensuring organizations can defend against the latest threats, yet many IT security teams still rely on outdated processes.
Below, we explore six strategies that are vital to modern, successful vulnerability management.
1. Integrated Data
It’s common to analyse results from different types of assessments, such as vulnerability scans and penetration tests, in silos. But this could be preventing teams from identifying trends and gaining a fuller understanding of their threat landscapes.
Consolidating results from different assessments into one database enables IT security teams to view their vulnerability data more holistically, so they can make the best decisions for their organizations and stay ahead of attackers.
2. Asset Prioritization
Many organizations possess an inventory list of their assets; the next step is to create a prioritization system for these assets. Generally, important assets could be any that are business-critical, internet-facing, or contain sensitive data.
Prioritizing your assets will serve as a good guide for navigating the hundreds, if not thousands of issues discovered by vulnerability scans. Your team will be more focussed, resources will be more efficiently allocated, and your business will be better protected.
3. Exploit Monitoring
Did you know only 20% of all vulnerabilities* have exploits available? If monitoring exploits is not part of your vulnerability management process, your team could be wasting time on issues that don’t matter, or worse, leaving others open that need remediating immediately.
A modern vulnerability management program should be intelligence-led, so teams can accurately evaluate risk and take action based on real-world context. One way of doing this is by integrating exploit resources, such as Exploit DB or Zero Day Initiatives, with your processes.
*Tenable study
4. Time-to-Remediate
Are you measuring how long it takes your team to remediate issues? Tracking your mean-time-to-remediate (MTTR) will help you establish which aspects of your vulnerability management program are working, and what could be improved.
The best way to calculate your MTTR is by risk level, on a monthly basis. This makes it easier to identify bottlenecks and establish how your team is performing over time. Using a tool that calculates and reports on this metric for you will save significant effort.
5. Easy Collaboration
If you’re still delegating issues over email and tracking remediation in spreadsheets, think again – there are much better ways to collaborate.
Live chat, ticketing systems, and automated email alerts are just some of the ways you can ensure ease of collaboration, and save you the time it takes to request status updates and track progress. A vulnerability management solution can provide all the tools you need to collaborate on remediation in one place.
6. Tools and Automations
A study** found that 51% of security teams spend more time navigating manual processes than responding to vulnerabilities. As threat actors become more and more sophisticated, this is time that no team can afford to waste.
There are a number of ways you can streamline vulnerability management. For example, you could use dashboards to automate reporting, or replace spreadsheets with dynamic databases. Utilizing a solution that combines these useful tools will immediately modernize and accelerate your processes.
**Ponemon Institute study
Upgrade to Modern Vulnerability Management
Modern vulnerability management is essential to protecting your organization in the most efficient and effective ways possible. A vulnerability management platform can take the legwork out of upgrading your processes by providing a one-stop solution.
Rootshell is a next generation, vendor-neutral platform that supercharges vulnerability management from start to finish, including improving collaboration, tracking assets, detecting exploits, and much more.