Rootshell Security Research and Development Lead, Dr. Neil Kettle, writes working exploit for Windows DNS vulnerability … and no, you can’t have a copy.
Microsoft is warning of a 17-year-old critical Windows DNS Server vulnerability that the company has classified as ‘wormable.’
‘Wormable’ mean that attackers could potentially create malware that executes code on Windows servers, create malicious DNS queries, and could even lead to a organisation being breached.
Microsoft Principal Security Program Manager, Mechele Gruhn, went to on to say, that “’while this vulnerability is not currently known to be used in active attacks, it is essential that customers apply Windows updates to address this vulnerability as soon as possible.”
The vulnerability, originally discovered by Sagi Tzaik of Check Point (CVE-2020-1350), could allow attackers to execute arbitrary code remotely on Windows servers through malicious DNS responses that could even eventually lead to a company’s infrastructure being breached.
Rootshell Security Head of Research and Development, Dr. Neil Kettle, explains: “The issue arises from an integer overflow in the calculation of the amount of memory to allocate while parsing a SIG resource record from a malicious DNS response. In this case the author of the code utilises an unsigned short (2-byte) integer to calculate the number of bytes to allocate.”
“However, in certain circumstances it is possible for a SIG record to require more than 2^16 bytes of storage and as such this calculation may overflow leading to insufficient memory being allocated.”
Rootshell has developed a proof-of-concept exploit for the issue which returns malicious DNS responses to remote DNS servers upon a request being received.
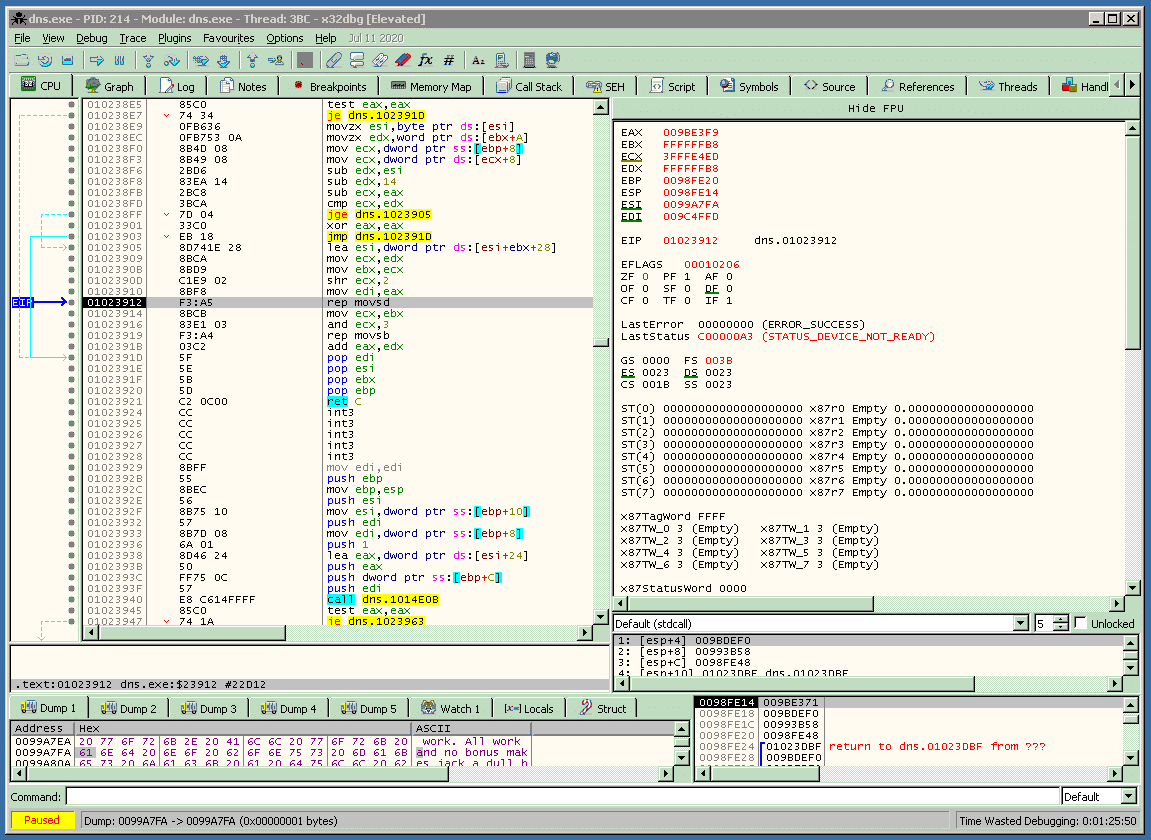
The above screenshot demonstrates the result of a vulnerable DNS server receiving a malicious response from the proof-of-concept exploit.
The crash in this case is the result of the ‘dns.exe’ process attempting to write to un-paged memory since the DNS response causes the ‘dns.exe’ process to allocate an insufficient amount of memory into which it attempts to copy the SIG record returned in the response.
A working exploit has been constructed that targets Microsoft Windows 2003 systems with work continuing to improve the stability of the methods used to achieve arbitrary code execution remotely and their adaption to later versions of Microsoft Windows.
The result of running the proof-of-concept a system that runs an unpatched DNS server is the following:
[tcp-14481] starting listener, 53/tcp.
[udp-14480] connection accepted from 213.165.242.17:1107
[tcp-14481] connection accepted from 213.165.242.17:1109
[tcp-14481] received question [0889] for: 88.shelltun.ev6.net. [21-bytes][tcp-14481] creating poison buf…
[tcp-14481] adding bing @72… bing @129… bong @132… #adnw
[tcp-14481] name len: 121, sign len: 65464, total: 65585…
Rootshell’s VP of Threat Services, Shaun Peapell, “We believe that exploring vulnerabilities to the fullest extent gives us the best chance of understanding the ways threat actors may use these flaws against our clients, and the IT industry as a whole.”
“We may even release a video of the exploiting achieving remote SYSTEM…”, teased Dr. Kettle.
Subscribe So You Never Miss an Update



