In its simplest form, a vulnerability management program will consist of running scans, distributing results, and remediating issues.
Although this is far better than nothing, a vulnerability management program needs to be as robust, continuous, and optimized as possible to ensure IT security teams can respond to threats fast and efficiently.
In this article, we discuss best practices for vulnerability management programs, and share our insights for how you can optimize yours.
Vulnerability Management Cycle
A Vulnerability Management Cycle provides guidance on how to effectively plan, manage, and execute remediation.
It sets out best practice processes and illustrates that vulnerability management needs to be continuous, rather than project-based, for complete visibility.
In our experience, mapping your processes to a Vulnerability Management Cycle ensures your program is set up for success.
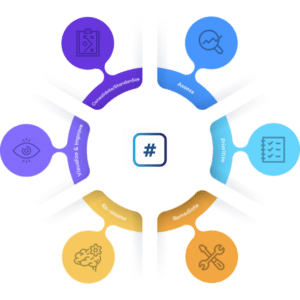
Our definition of a Vulnerability Management Cycle is as follows:
- Assess: Identify vulnerabilities within your organization’s network by carrying out vulnerability assessments.
- Consolidate: Centralize your assessment results in one place. This could involve transferring results from PDFs to a standardized database.
- Prioritize: Analyse your vulnerabilities to establish their importance for prioritization. This includes referencing threat intelligence, as well as considering the business-context of your assets.
- Remediate: Implement your remediation program to resolve vulnerabilities. This could also involve accepting risks and dismissing false positives.
- Re-assess: Verify whether your remediation efforts have been successful by rescanning your estate.
- Visualize and improve: Evaluate and improve your vulnerability management processes, such as resolving bottlenecks and ensuring compliance with service level agreements.
From Basic to Modern Processes
Vulnerability scans often result in lots of noise and data. Without modern processes in place, programs can become incredibly challenging to manage, as well as difficult to scale.
Below, we suggest how basic processes can be improved to better support IT security teams.
Integrate with Intelligence
Many teams still rely solely on CVSS (Common Vulnerability Scoring System) scores to evaluate the severity of an issue, but these scores are static and often lack important context. If you prioritize vulnerabilities using CVSS scores alone, your team could be wasting time on issues that don’t matter, or worse, leaving others open that need remediating immediately.
Instead, vulnerability management should be intelligence-led, helping you accurately evaluate risk and prioritize based on real-world context. One way of doing this is by integrating exploit resources with your processes, such as Exploit DB or Zero Day Initiative.
Asset-based Prioritization
Vulnerability data is difficult to action if it is not contextualized to your organization’s assets – a highly rated vulnerability may not actually be a top priority if it doesn’t affect a mission-critical system. That’s why asset-based prioritization is essential to ensuring your program is set up to protect your organization most effectively.
Keeping an up-to-date asset inventory, organized by priority-level, is key. Ensuring these priorities are clearly communicated with your team will help ensure every remediation action is aligned to your organization’s objectives.
Effective Frameworks
A study by the Ponemon Institute found that 51% of security teams spend more time navigating slow, manual processes than responding to vulnerabilities. As threat actors become more and more sophisticated, this is time that no team can afford to waste.
In particular, many IT security teams still manage their vulnerability management programs using spreadsheets, or delegate remediation tasks over email. Utilizing a dedicated vulnerability management framework will help streamline and accelerate your processes.
Processing Data
Many organizations utilize multiple scanning tools to gain the coverage they need. This can inundate teams with data. A lack of consolidation could prevent your team from identifying trends and understanding the bigger picture of your threat landscape.
We recommend implementing a process that integrates your scanning data, creating a centralized database. In our experience, clients who consolidate their scanning results, as well as other assessment reports, such as penetration tests, benefit from greater visibility and situational awareness.
In conclusion
Mature vulnerability scanning processes take time to develop. Continuously evolving your program over time is a more realistic approach for busy teams, rather than attempting to establish a polished program from day one.
Processes are the foundation of any highly effective vulnerability management program. Without proper consideration being given to the frameworks and procedures that will govern your program, hiring great people and buying the market-leading scanning tools will all be in vain.
Join Rootshell’s Director of Managed Services, Nathan O’Hare, in a webinar on 10th November, to find out more about what makes a highly effective program.
Subscribe So You Never Miss an Update



