8 Generative AI Security Risks and How to Manage Them
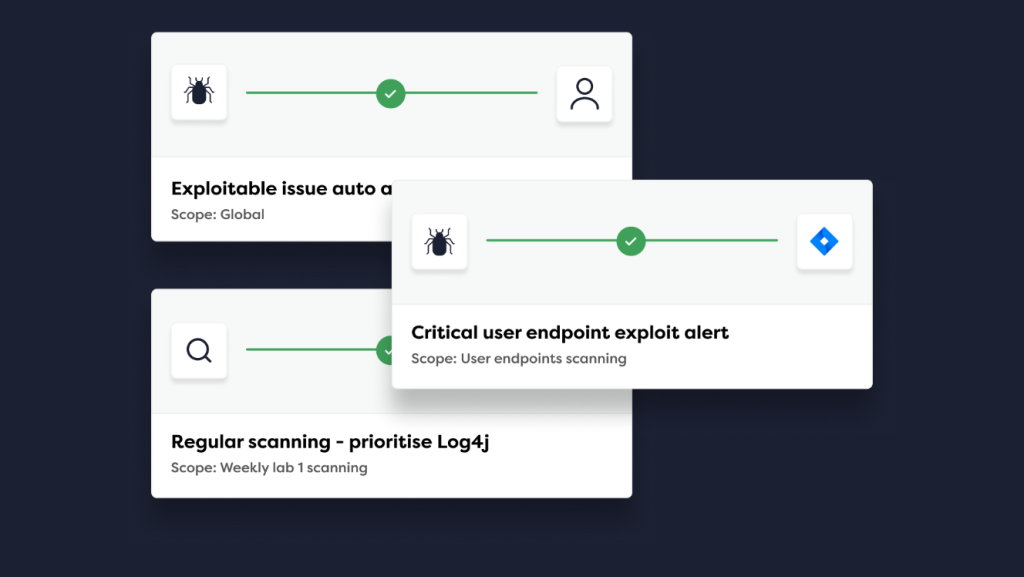
The Rootshell Platform continues to evolve — and this month’s update brings a series of improvements designed to make vulnerability management smarter, faster, and more transparent across every layer of your security operations.