Vulnerability management as a service provides teams with the expertise of a dedicated, managed scanning service. Some vendors will also provide a vulnerability management solution, to support in-house teams from scanning to remediation.
In this article, we discuss the benefits of vulnerability management as a service, as well as the role of a vulnerability management system.
What Is Vulnerability Management As a Service?
Vulnerability Management As a Service, also known as VMaaS, delivers the end-to-end process of vulnerability scanning to organizations, as well as assistance with vulnerability management, which is usually provided using a platform, tool, or system.
Vulnerability management as a service typically involves the following:
- Planning and scoping vulnerability scans
- Tuning and configuring scanning platforms
- Scheduling, executing, and managing the vulnerability scans
- Prioritizing and validating vulnerabilities
- Delivering reports and remediation guidance
- Access to a vulnerability management system
The Benefits of Outsourcing Your Vulnerability Management
Validation & Manual Reviews
One of the biggest benefits of vulnerability management services is that the provider will manually review vulnerability data before it is delivered to clients.
This confirms the accuracy of reported vulnerabilities, reduces the number of false positives, and ultimately provides teams with a list of actionable issues, instead of an exhaustive list of potentially irrelevant vulnerabilities.
Therefore, teams are equipped with better quality data, which leads to better decisions and outcomes for the organization.
Subject Matter Expertise
Security teams can also benefit from their provider’s in-depth knowledge and experience. Providers of vulnerability management as a service are exposed to issues across a wide range of environments daily, so they can give the best context and advice to their clients, such as how a vulnerability might be taken advantage of by a threat actor.
Optimal Configuration
Vulnerability management as a service providers will also have the best understanding of how scanners should be configured to give accurate and reliable results, saving internal teams the time and effort of learning new tools, managing licences, and tracking scanners. And the efficiency of providers means that results can be delivered fast, reducing the time between the detection and remediation of issues.
Additionally, providers will have access to a range of different tools, so they can select the best option for a given scope. Organizations may not be able to be as flexible due to scanner licensing terms.
Access to a Vulnerability Management System
Providers of vulnerability management services may also provide access to a vulnerability management system.
Vulnerability management systems help security teams better manage their results from vulnerability assessments, including prioritizing, delegating, reporting, and more. The best vulnerability management tools support other threat assessments too, such as penetration tests.
A vulnerability management solution is usually far more effective than relying on internal systems, such as spreadsheets and email, as the best platforms are optimized to accelerate and streamline the end-to-end process of vulnerability management.
What is The Rootshell Platform?
The Rootshell Platform is a vendor-agnostic vulnerability management solution.
Rootshell’s unique features help you accelerate every stage of the vulnerability management process, reducing mean-time-to-remediate by up to 68%, and enhance efficiency from start to finish.
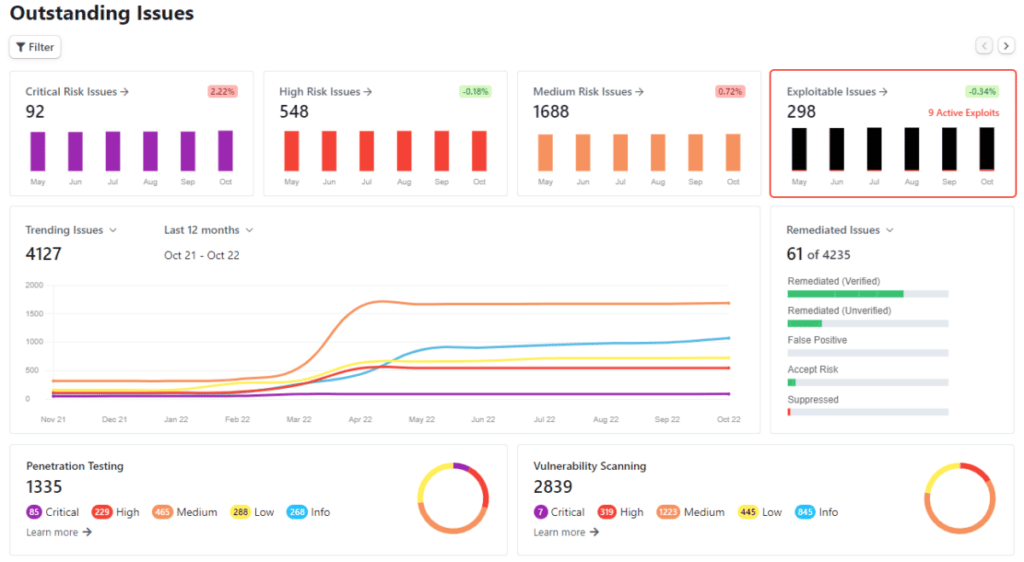
The Rootshell Platform’s Vulnerability Management as a Service Features
- Centralizes security issues: Rootshell is vendor-agnostic, so you can use it to consolidate results from any assessment type. Managing all your vulnerabilities in one place makes it seamless to continuously analyse, prioritize, and manage all issues across your estate.
- Aids intelligence-driven prioritization: Rootshell’s industry-leading Active Exploit Detection automatically alerts you to active exploits for your issues on a daily basis, so you can gain the context needed to prioritize most effectively.
- Streamlines remediation: Rootshell modernizes vulnerability management programmes and makes it easy for teams to deliver fast and effective remediation by reducing manual processes. This includes bi-directional integrations with popular ticketing systems, automated importing for vulnerability scans, and much more.
- Visualize Technical Risk: Rootshell helps you gain a clear understanding of your global threat landscape and makes it effortless to continuously analyse your technical risk, with insightful dashboards and automated reporting.
Subscribe So You Never Miss an Update




