Author: Liam Romanis (Principal Security Consultant)
In previous reports for customers whose Microsoft 365 (M365) configurations have allowed Gifs and Memes, it has been recommended that these are blocked via configuration because malware could be shared using this content via Teams meetings. Although, malicious content in images, videos, and gifs have been well known for some time.
GIFShell is a new attack scenario whereby attackers can deliver malicious files, commands, and perform data exfiltration via GIFs. It demonstrates a type of exploitation of poorly configured Teams Software. Microsoft may not be releasing a patch for this, but it should be possible to block it via diligent configuration and defence in depth.
This blog will focus on M365 defences. However, it should be noted that this type of attack would work against on-prem networks.
Customers could prevent external users from accessing teams calls or prevent external and anonymous users from connecting with their M365 subscription and from connecting with Teams calls. However, this is a moot point, because many customers use Teams to communicate with third parties. Although, this could still be permitted in a more controlled manner by preventing low privilege users from inviting external users and by configuring M365 to prohibit email verified users.
The malicious Gif could be disseminated via email. Most customers use an external email content provider to block egress and ingress malicious content. Therefore, many customers do not consider the M365 configuration options for blocking malicious content important.
However, many Advanced Persistent Threats (APTs), such as APT29 (Cozy Bear) subvert a single account and then use it to send malicious content to other users. So, it is recommended that customers apply all M365 content security as well. This will be covered in more detail in another blog article. In the meantime, please go here for further information on APT29 and their Tactics, Techniques and Procedures.
How to defend against GIFShell
The main defence against GIFShell, and other attacks via Teams, is to prohibit the sharing of files, memes, and Gifs via Teams.
The first step should be to determine whether Teams allows Gifs and Memes. We could run the following PowerShell command:

Ideally, the global and default policies should show:

To configure Teams to block this content, the following PowerShell commands could be used:

Or

Another attack vector, which has already been used by APTs, is Teams P2P File Sharing.
To determine whether the M365 subscription is vulnerable we can perform the following PowerShell query:
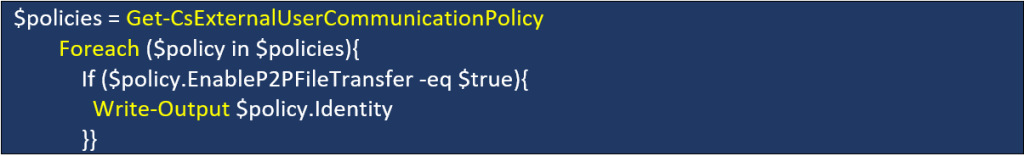
If configured correctly, the following values should be displayed:

By default, Microsoft Teams enables and allows P2P file transfers for all internal and external users and guests.
Microsoft’s P2P file sharing allows or blocks file transfers for users whether they are transferring files to a user who is within the same organization or to a federated user from another organization. Setting this option to ‘false’ allows only internal file transfers, while leaving it enabled allows for file sharing outside the organization.
Many organizations block common P2P traffic protocols, but allow Microsoft IP’s, protocols, and domains through their organization’s firewalls. Microsoft Teams provides a native, usually unmonitored method of data exfiltration to external parties. This may be configured globally or on a per-user basis.
To defend against GIFShell and similar attacks, it is recommended that all External User Communication Policies are configured to Block. Please visit this Microsoft web page for further information.
Setting the following should block P2P file transfers from external users:

However, internal users will still be able to send potentially malicious Gifs and Memes via Teams.
As APTs are known to use compromised user accounts to attack other users, it will also be important to block internal users from using P2P file transfers.
We can do this by applying the rule to all users. We can start by creating a new policy which blocks P2P file transfers:

Then we can assign users to this policy:

Other vectors of course exist. Defence in Depth and monitoring are key to maintaining a manageable level of assurance.
Get in touch to find out how we can improve your defences
Subscribe So You Never Miss an Update




