The Rootshell team have discovered a flaw within miniDLNA; a server software that exchanges media files, such as music, images, and videos, between clients on a network. This is the second bug the team have discovered in miniDLNA’s software.
The team identified a remotely exploitable stack corruption issue, occurring in different places within the same code. ‘Stack’ is a memory location that stores information on a temporary basis. It becomes corrupted when its contents are modified due to a programming error. In this case, the program is attempting to use memory beyond that which has been allocated, i.e. an out-of-bounds access issue.
The bug occurs in the parsing of Notify SSDP requests in the SSDP parser; data parsing is a method of converting a string of data into a different format. This process notifies the server that a new device has joined the network.
The root cause of the issue is due to a lack of proper validation of several loops iterating over the input from the network socket. The code assumes the presence of certain characters (namely newline/carriage return) in the buffer and does not terminate upon hitting a NULL character (code that denotes the end of a character string). Therefore, it can be made to parse data outside the allocated buffer.
The issue can also be exploited to cause a Denial of Service (DoS) attack on the remote service or a stack overflow error.
Below, Rootshell’s Head of Research and Development, Dr Neil Kettle, demonstrates how the issue can be found in the ‘minissdp.c’ file:
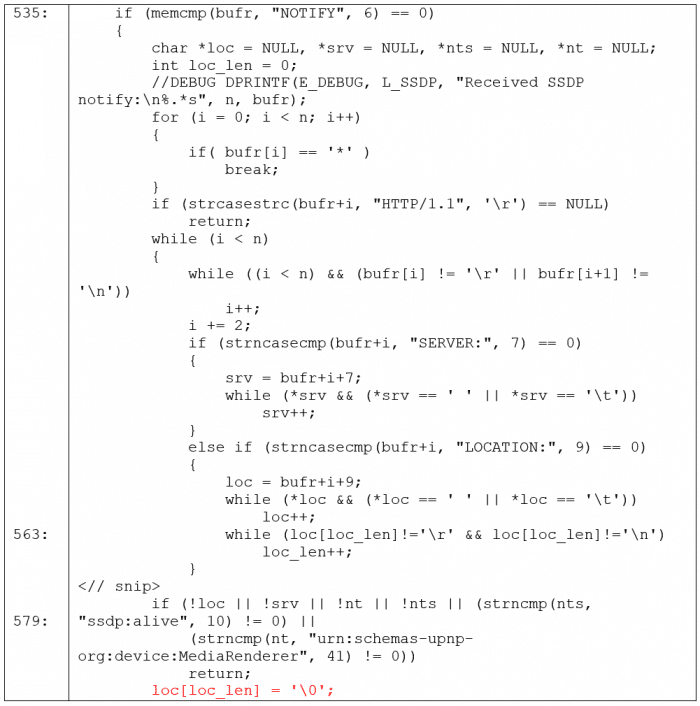
The code fails to check for a NULL byte on line 563. Therefore, the loop can be made to increment ‘loc_len’, such that ‘loc_len’ is greater than the size of the buffer ‘loc’ (and thus ‘bufr’, a length of 1500-bytes).
Below, you can see an example of an exploitation attempt:
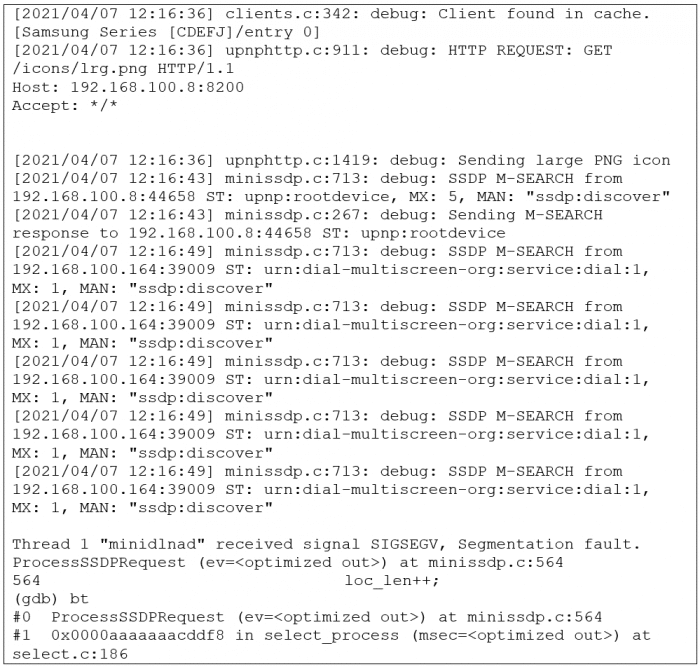
The Rootshell team have developed a proof-of-concept exploit, which results in a DoS attack via an invalid memory dereference and/or memory corruption.
This is the latest discovery of Rootshell’s R&D work, which is committed to encouraging software vendors to address bugs and uphold the security of their products for the safety of users.
In line with our Bug Disclosure Policy, we gave the vendor 90 days’ notice before disclosing the bug. This issue currently remains unfixed and has since been catalogued as CVE-2021-27202.
Read our previous bug releases:
Rootshell Discover KeyScrambler Security Flaw That Enables Encryption To Be Bypassed
Rootshell Discover Remote Heap Corruption Bug Within MiniDLNA And Develop Proof Of Concept Exploit
Rootshell Discover a Denial of Service Flaw in Dekart Private Disk Encryption Software
Subscribe So You Never Miss an Update