A member of our leadership team received a SMiShing (SMS Phishing) message that appeared to be from the Royal Mail, and almost clicked it.
Phishing scams, including SMiShing attacks, are one of the most common ways threat actors attempt to steal personal information, which threatens the security of both individuals and organisations. Read on to hear how one of our team almost fell for a recent SMiShing attack, in our real life SMiShing attack example.
The SMiShing attack
Below, you can see the SMiShing text that was sent to one of our leadership team members.
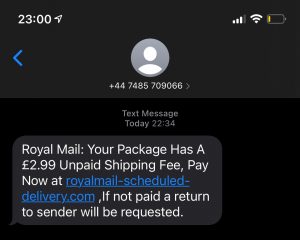
It reads: “Royal Mail: Your Package Has A £2.99 Unpaid Shipping Fee, Pay Now at royalmail-scheduled-delivery.com, If not paid a return to sender will be requested.”
Clicking the link takes the recipient to a very convincing fake mobile site.
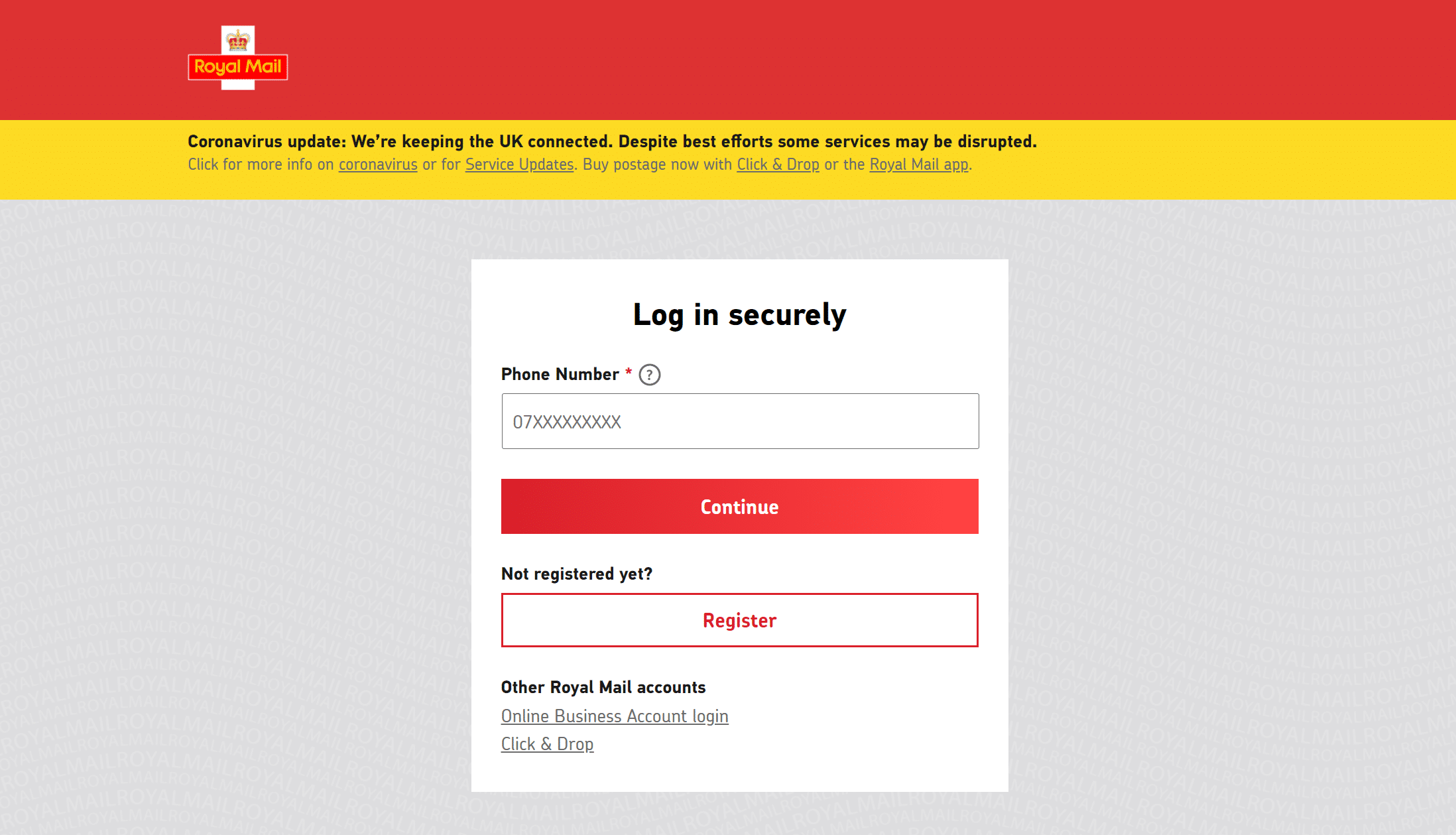
From a social engineering perspective, you have to admire the tactics employed. The SMiShing text was sent late in the evening to catch people when they may not be at their mental best, but not so late that everyone would be asleep.
‘Royal Mail:’ is the first thing a recipient would read, and if the text is only given a cursory, tired-eyed scan, ‘royalmail’ is the only part of the URL they may pick up.
The message also conveys a sense of urgency (i.e. ‘if not paid…’), which is a tactic commonly employed by threat actors to pressure recipients into complying.
Spoofing the Royal Mail is a clever strategy to achieve maximum applicability and impact. It’s the same reason that SMiShing texts and phishing emails often come from companies like Amazon; almost everyone has used the Royal Mail or Amazon at some point.
Shaun Peapell, Rootshell Security’s VP of Global Threat Services went on to say: “SMiShing attacks are a very powerful tool to socially engineer the target victim. These attacks can also become very personal, where the attacker can potentially ‘spoof’ the originator or sender’s number by manipulating the 11 character / number identifying the caller. By doing so, an SMS text can often fool the most diligent user!”
Worried about SMiShing attacks? Find out how you can protect your organisation.
What is a SMiShing attack?
SMiShing is a type of phishing attack that uses text messages to trick recipients into divulging confidential information. It is a form of ‘social engineering’, which are cyber attacks that rely on misleading people; email phishing is another example.
A SMiShing text message will appear to be from a credible sender and contain a link to a mobile site that attempts to convince the recipient to take an action, such as ‘log in’ or ‘create an account’. This allows cyber criminals to harvest email addresses and passwords, which could have devastating consequences if a victim has used the same credentials for, say, a bank account.
SMiShing can also pose risk to businesses if an employee uses the same password to access their work account.
How can you defend against a SMiShing attack?
- Never click a link received through a text message. Instead, go directly to the sender’s website or contact them using their official details to verify the message.
- Be very wary of messages that suggest urgency, e.g. ‘you need to act now’. This is a common tactic employed in SMiShing scams. Take your time to verify the message; avoid knee jerk reactions to any kind of correspondence that is requesting your details.
- According to the National Cyber Security Centre (NSCS) in the UK, you should forward suspicious text messages to 7726. This is a free-of-charge service that enables your telephone provider to investigate the text and take action, if the text is found to be a SMiShing attack.
- As an organisation, it’s essential to ensure your workforce is adequately cyber aware to defend against SMiShing attacks. Working with a phishing assessment expert like Rootshell Security can help. A recent report found that after one year of monthly phishing assessments and regular training, the percentage of employees that would fall victim to a phishing attack falls from 37.9% to 4.7%.
Find out more about how you can protect your organisation from SMiShing attacks.
Subscribe So You Never Miss an Update




