
What is continuous penetration testing?
Annual security testing is no longer sufficient to defend against ever-evolving cyber threats. Rootshell Security’s Continuous Penetration Testing services help your organisation maintain and improve its security posture year-round.
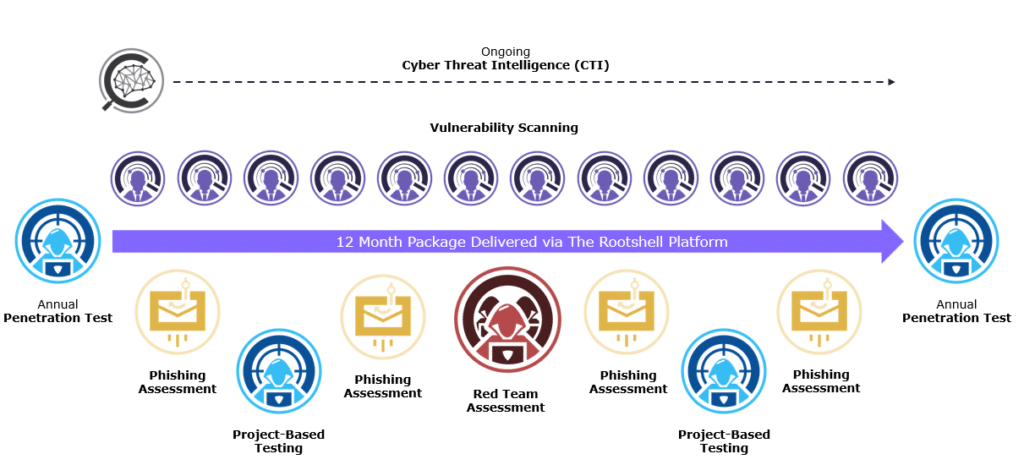
Our Continuous Testing services include penetration tests, managed vulnerability scans (MVS), cyber threat intelligence (CTI), phishing assessments, and red team assessments as part of a combined, continuous security solution, tailored to your organisation.
Our security consultants work closely with you to design a continuous testing solution that best suits your requirements.
Our Continuous Security Testing Services
We offer interlocking cyber threat intelligence (CTI), managed vulnerability scanning (MVS), phishing assessments, penetration tests, and red team assessments as part of a combined security package. These are offered as a series of recurring monthly, quarterly, and yearly undertakings to minimise your risk.
Our Continuous Testing packages are tailored to meet your objectives, risk appetite, and budget. Below, you can see an example of a fully managed Continuous Testing package. The Rootshell Platform enables you to pick and choose the services that best fit your organisation.
The benefits of continuous pen testing
Bolster your security strategy and ensure year-round protection with continuous security testing.
- Year-round protection: A lot can happen between annual penetration tests. Our continuous service tests your digital infrastructure year-round, so you can ensure your security posture is maintained and improved on an ongoing basis.
- Prepare for a real-world attack: Penetration tests are one of the most effective ways to evaluate your security posture. By emulating the tactics, techniques, procedures used by hackers, our services truly put your organisation’s defences to the test.
- Uncover critical vulnerabilities: As the risk of cyber attacks continues to increase, it’s crucial you have complete visibility of your organisation’s vulnerabilities. Our continuous pen testing service identifies any vulnerabilities, from low to high risk, so you can take action.
- Effectively remediate risk: Continuous pen testing provides you with the data you need to resolve vulnerabilities. Our penetration testers offer expert support so you can remediate as quickly and effectively as possible.
- Comply with security standards: Carrying out penetration testing is essential for meeting a number of different regulatory standards. Our CREST-certified continuous pen testing will ensure your organisation is compliant.
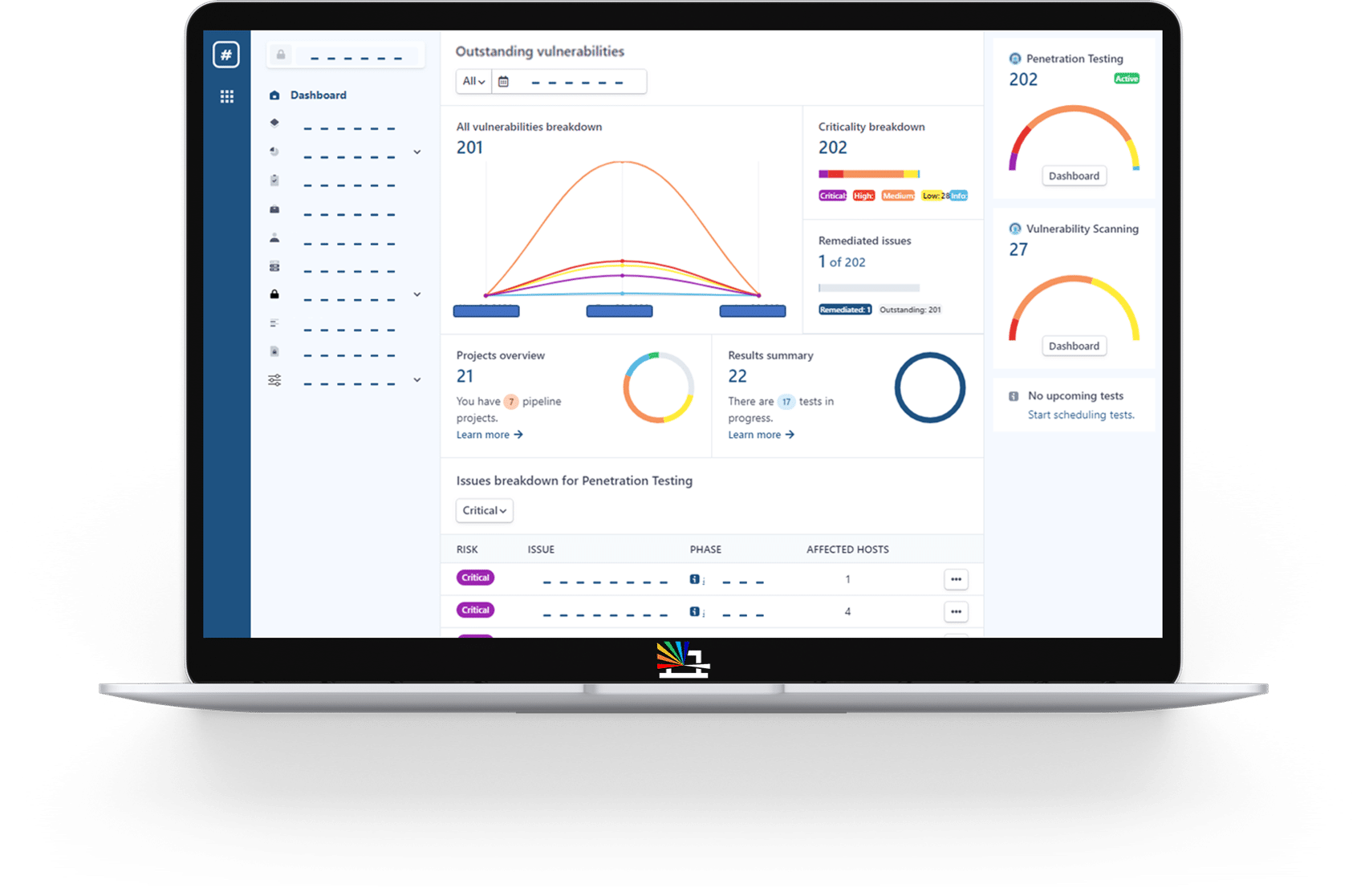
View results from your continuous testing services in a single consolidated interface
The Rootshell Platform is a vendor-agnostic vulnerability management solution that puts you at the centre of your IT security ecosystem. Consolidate assessment results, accelerate remediation from start to finish, and gain real-time insight into your ever-changing threat landscape.
Why Rootshell’s Continuous Testing services?
We’re proud to be a trusted provider of continuous security testing for some of the UK’s largest organisations.
- CREST-certified pen testing: CREST is an internationally recognised accreditation for penetration testing services. Our CREST-certified testers work to the highest technical and ethical standards.
- Quality assured: We deliver our pen testing services to industry standards, such as Open Web Application Security Project (OWASP) guidelines, the National Institute for Standards and Technology (NIST), and the Penetration Testing Execution Standard (PTES).
- Expert advice and support: Our highly experienced testers provide you with expert guidance and support throughout. You will receive clear reports and advice, along with step-by-step instructions, ensuring you know exactly how to remediate and reduce risk.
- Remote penetration testing: Our pen testing devices enable our testers to remotely access your organisation from our secure Security Operation Centre (SOC). This allows your organisation to operate as normal whilst conducting continuous penetration testing.


